Hands-On Projects
 1. Use the S-Tools program to hide a file inside a WAV file.
1. Use the S-Tools program to hide a file inside a WAV file.
■Navigate to Chapter 1 of the Student Resource Center.
■Install and launch the S-Tools program (Figure 1-44).
Figure 1-44Install and launch the S-Tools program.
Hands-On Projects
■Drag a WAV file from Windows Explorer to theActionswindow (Figure 1-45).
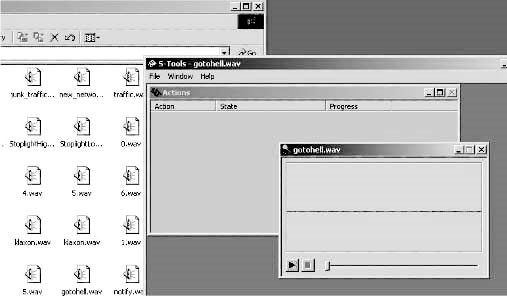
Figure 1-45Drag a WAV file to theActionswindow.
■Select a file to be hidden and drag that file inside the window of the WAV file
(Figure 1-46).
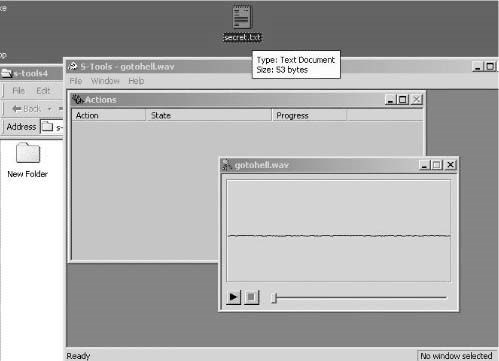
Figure 1-46Select a file to be hidden.
■Enter the passphrase (Figure 1-47).
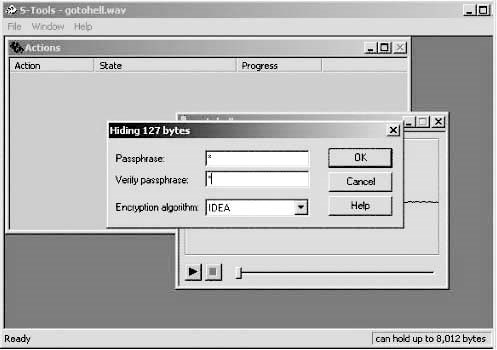
Figure 1-47Enter the passphrase.
■Right-click thehidden datawindow and selectSave(Figure 1-48).
■To view the data file, selectReveal.
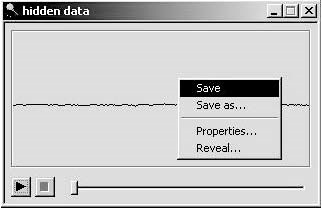
Figure 1-48Right-click thehidden datawindow and save the file.
- Use the StegHide program to hide text in images.
■Navigate to Chapter 1 of the Student Resource Center.
■Open the StegHide program in the command shell (Figure 1-49).
Hands-On Projects
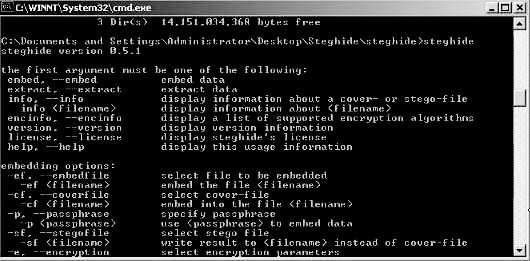
Figure 1-49Open the StegHide program in the command shell.
■To embed emb.txt in cvr.jpg, use the following command:steghide embed -cf cvr.jpg -ef emb.txt.
■To extract embedded data from stg.jpg, use the following command:steghide extract -sf
stg.jpg.
- Use the FortKnox program to hide data within another file.
■Navigate to Chapter 1 of the Student Resource Center.
■Install and launch the FortKnox program.
■Explore various options (Figure 1-50).
Figure 1-50Explore the various options in FortKnox.
■SelectSteganography 2.8from the Utilities menu. Browse the image file and message file, and click theEncryptbutton (Figure 1-51).
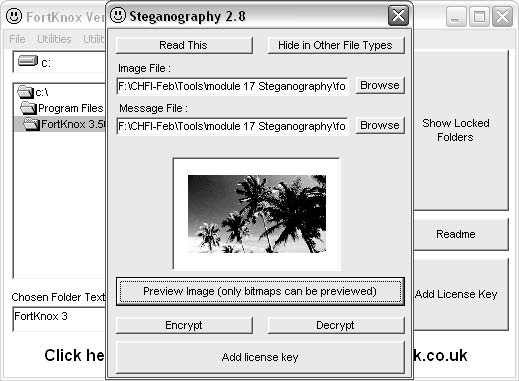
Figure 1-51Browse the image and message files, and click theEncryptbutton.
■SelectWindows Securityfrom the Utilities (Figure 1-52).
Figure 1-52SelectWindows Securityfrom the Utilities.
Objectives
After completing this chapter, you should be able to:
Determine the best data acquisition methods
Understand data recovery contingencies
Understand the need for data duplication
Use common data acquisition tools
Use common data duplication tools
Key Terms
Data acquisitionthe act of taking possession of or obtaining control of data and adding it to a collection of evidence

Data**AcquisitionandDuplication**
Chapter
2
Data duplicationthe act of making a copy of data already acquired to preserve the original evidence in pristine condition
Sparse data copya copy that an investigator makes of only part of a large set of data in which only the data pertinent to the investigation is included, in order to reduce the overall size of the evidence file; this technique is often used when copying data from RAID arrays, when dealing with terabytes or petabytes of information, or when only specific evidence is needed
Transmission Control Protocol (TCP)a protocol that implements a core set of rules that allow reliable connection-oriented connections between host computers over a network
User Datagram Protocol (UDP)a nonreliable protocol that implements a best-effort set of rules that allow for network communication where exact delivery of each packet is not critical, such as for streaming video
2-1
Case Example
Jeremy Johnson, 26, was hired by Adams Central School District as a teacher. During his tenure as a teacher, there were rumors around the school campus about an inappropriate relationship between him and a female student. Both denied the rumors. Since school officials had no evidence of the relationship, they could only issue a warning. Several months later, the student told her cousins about the relationship. This triggered an investigation by the Adams County Sheriff’s Department.
The police searched Johnson’s home. Johnson’s bedroom matched the description given by the student in an interview with a female police officer. Johnson continued to deny the girl’s claims concerning their sexual relationship. During the search, they seized his laptop and desktopcomputer. The investigators were able to verify that Johnson and the student exchanged e-mails. Johnson had reportedly set up an e-mail account for the girl in his wife’s name. Though the e-mails were not explicit, the investigators could prove that Johnson and the student had been having a sexual relationship.
Later, the forensic examiner found that Johnson had been trading child pornography over the Internet. He had hundreds of nude pictures of children obviously under the age of 18. He had tried to hidethe images by putting them in a folder labeled “music.”
Jeremy Johnson was arrested and jailed on 19 charges of child seduction, a Class D felony.
Introduction to Data Acquisition and Duplication
This chapter focuses on data acquisition and data duplication.Data acquisitionis the act of taking possession of or obtaining control of data and adding it to a collection of evidence.Data duplicationis the act of making a copy of data already acquired to preserve the original evidence in pristine condition. The chapter starts by discussing how to determine the best data acquisition methods for a certain situation. It then discusses how to make sure crucial data is not lost during the acquisition process. The chapter then covers the importance of data duplication before moving on to descriptions of the tools investigators use for data acquisition and duplication.
Determining the Best Acquisition Methods
Forensic investigators can acquire digital evidence using the following methods:
Creating a bit-stream disk-to-image file
Making a bit-stream disk-to-disk copy
Creating a sparse data copy of a folder or file
Disk-To-Image File
Creating a bit-stream disk-to-image file is the most common method forensic investigators use. When using thismethod, forensic investigators are able to make as many copies of the digital evidence as they need. Investigators are able to image the original disk to another disk. An investigator can then make use of other tools such as EnCase, FTK, Smart, Task, andIlook to read and analyze the image file.
Disk-To-Disk Copy
If an investigator is unable to create a bit-stream disk-to-image file, the alternative is to create a bit-stream disk-to-disk copy of the suspect’s disk drive in order to acquire the informationfrom it. There are several bitstreaming programs that can copy the information from one disk to another. Disk-to-disk imaging tools include SafeBack, SnapCopy, and Norton Ghost. Many of these applications run under MS-DOS.
Sparse Data Copy
There are timesduring a forensic investigation when an investigator finds incriminating evidence in a particular file or folder. Therefore, it would not be necessary to create a bit-stream disk-to-image file or a disk-to-disk copy. The investigator would just need to create a sparse data copy of the folder or file. Asparse data copyis a copy that an investigator makes of only part of a large set of data in which only the data pertinent to the investigation is included. An investigator may choose to make a sparse data copy to reduce the overall size of an evidence file.
Data Recovery Contingencies
Investigators must make contingency plans when data acquisition failure occurs. To preserve digital evidence, investigators must create a duplicate copy of the evidence files. In case the original data recovered is corrupted, investigators can make use of the second copy. Investigators can use forensic tools such as EnCase and SafeBack to obtain multiple copies.
Typically, computer forensic investigators make at least bit-streamimage copies of the digital evidence that is collected. Investigators have at their disposal more than one bit-streaming tool. They should use at least two of these tools to make copies of the digital evidence in case one tool doesn’t properly acquire thedata.
During the data recovery process, an investigator must remember not to make any changes to the digital evidence. Forensic activities must be performed only on the bit-stream copies of digital evidence to ensure that the original evidence is not altered orcorrupted.
The Need for Data Duplication
Investigators need to be concerned about destructive devices that can be planted in computer systems by their owners. Evidence can be destroyed if an investigator is not careful. These destructive devices can overwrite data fragments, and they can alter or destroy data stored in the Windows swap file. A suspect could use a selfdestructing program that could wipe out any evidence when it detects a certain trigger. This can hamper an investigation and make the collection of evidence much more difficult. Thus, data duplication is essential for the proper preservation of digital evidence.
Data Acquisition Software Tools
There are many different data acquisition tools available to forensic investigators. All of these tools have different features that make them useful in different situations.
Windows Standard Tools
Windows data acquisition tools—such as xcopy, diskcopy, Volume Shadow Copy, and Windows Explorer— allow an investigator to easily examine or acquire evidence from a disk with the help of removable media, such as a USB storage device. These tools can also use Firewire to connect hard disks to forensic lab systems. However, Windows data acquisition tools cannot acquire data from a protected area of a disk.
Windows is equipped with many tools that are intended for administrators but are also useful for computer forensic investigators. These tools permit the investigator to acquire and replicate digital evidence. The forensic investigator is able to find out where logical volume information is found and is able to collect evidence from a system even when it is running. Windows data acquisition tools enable forensic investigators to acquire a full logical image of a drive. But, Windows tools can only acquire data that the operating system can recognize and do not include slack space or deleted files.
Home and workplace computer systems are designed with hard drives with large storage capacities. Imaging a 500 GB hard drive using traditional methods, for instance, may take a total of 24 hours to complete. From a forensic investigative point of view, 24 hours is a long time. This can lead to a loss of productivity for the company that owns the computer containing the evidence.
On the other hand, data acquisition programs like dd and netcat usually spend a lot of time copying data from one buffer to another. In order to image a logical volume, data on the volume must be paged from internal buffers to the file systems in memory. This process takes a lot of time, and this is one of the main limitations of standard forensic tools when compared to Windows forensic tools.
Linux Standard Tools
Forensic investigators use the built-in Linux command dd to copy data from a disk drive. This command can make a bit-stream disk-to-disk copy or a disk-to-image file. The dd command can copy data from any disk that Linux can mount and access. Other forensic tools, such as AccessData FTK and Ilook, can read dd image files.
One of the advantages of using the dd command in Linux is that it is free software that does not rely on any additional resources from the computer. The dd command in Linux can create images of ext2, ext3, UNIX, FAT12, FAT16, FAT32, NTFS, HFS, and HPFS file-system disks. The dd command also enables examiners to extract digital evidence and copy it to any type of media that the Linux operating system is able to access.
The dd command in Linux does have certain limitations. An investigator needs to understandand be able to implement advanced UNIX shell scripting commands. The investigator must also define the exact number of blocks in the save set volume in order to create a volume save set. Also, the dd command is not available in all versions of Linux.
Using the dd Command
The syntax for the dd command is as follows:
dd if of
**Illegal HTML tag removed : bs
(usually some power of 2, not less than 512 bytes [i.e., 512, 1024, 2048, 4096, 8192])skip seek conv
source: where the data is to be read from
target: where the data is to be written to
skip: number of blocks to skip at start of input
seek: number of blocks to skip at start of output
conv: conversion options
For example, an investigator would use the following commands for these tasks:
To make acomplete physical backup of a hard disk:dd if/dev/hda of/dev/case5img1
To copy one hard disk partition to another hard disk:dd if/dev/sda2 of/dev/sdb2 bs4096 convnotrunc,noerror
To make an image of a CD:dd if/dev/hdc of/home/sam/mycd.iso bs2048 convnotrun**c**
To copy a floppy disk:dd if/dev/fd0 of/home/sam/floppy.image convnotrunc
To restore a disk partition from an image file:dd if/home/sam/partition.image of/dev/sdb2 bs4096 convnotrunc,noerror
To copy RAM memory to a file:
dd if/dev/mem of**/home/sam/mem.bin bs1024**
Using dd to Extract the MBR
The master boot record (MBR) is the consistent starting point for hard disks. It stores information about the disk. The MBR is always located at cylinder zero, head zero, and sector one, the first sectoron the disk. The MBR consists of the following:
Master partition table: This table contains a complete description of the partitions on the disk.
Master boot code: This is the small bit of code that the BIOS loads to start the bootstrapping process.
To see the contents of the MBR, an investigator uses the following commands:
dd if/dev/hda ofmbr.bin bs512 count1 od -xa mbr.bin
This dd command must be run as root. It reads the first 512 bytes from /dev/hda (the first IDE drive) and writes them to the mbr.binfile.
The od command prints the binary file in hex and ASCII formats.
Using netcat with dd
The netcat command supports the dd command with networking features. An investigator can use it to read and write data across the network using TCP or UDP.TCPis a protocol that implements a core set of rules that allow reliable connection-oriented connections between host computers over a network.UDPis a nonreliable protocol that implements a best-effort set of rules that allow for network communication where exact delivery of each packet is not critical, such as for streaming video.
To make a partition image on another machine:
On a source machine:dd if/dev/hda bs16065b | netcat targethost-IP 1234
On a target machine:netcat -l -p 1234 | dd of/dev/hdc bs**16065b**
DriveSpy
DriveSpy enables an investigator to direct information from one particular sector range to another sector. The DriveSpy application gives forensic investigators two methods to access disk sectors:
Defining the absolute starting sector aftera command and the total number of sectors to be read on the drive
Listing the absolute starting and ending sectors
Many of the DriveSpy commands are able to work with multiple ranges of sectors. These commands include CopySect, SaveSect, WriteSect, and Wipe. When a sector range is required as a parameter for a DriveSpy command, the ranges may be specified using the following syntax:
[Drive ID]: [Absolute Start Sector],[Number of Sectors]
[Drive ID]: [Absolute Start Sector]-[Absolute End Sector]
An investigator specifies the exact sector range by identifying a starting sector and then the total number of sectors using the first syntax. The second syntax defines a range by identifying both the starting and ending sectors. A comma and a hyphen differentiate the two syntaxes.
DriveSpy Data Manipulation Commands
There are two commands in DriveSpy that are used for data manipulation:
- SaveSect:The SaveSect command is used to copy particular sectors on a disk to a file. The SaveSect command copies the sectors as a bit-stream image so that the file is a duplicate of the original sectors. The syntax for the SaveSect command is as follows:
SAVESECT [Source Sector Range] [Destination File]
If a path is not identified in the file specification, the fileis created in the current working directory.
- WriteSect:The WriteSect command is used to regenerate information acquired through the SaveSect command. The WriteSect command copies the contents of an image file created by SaveSect to a series of sectors. The syntax for the WriteSect command is as follows:
WRITESECT [Source File] [Destination Sector Range]
As with the SaveSect command, if a path is not identified in the file specification, the file is created in the current working directory.
DriveSpy Data Preservation Commands
The DriveSpy application gives forensic examiners the ability to create and restore compressed images of drive partitions. If an investigator makes an image of a DOS partition, the free space is not included, as DOS cannot see thefree space in a cluster. However, if an investigator makes an image of a non-DOS partition, every byte is preserved, including the free space.
There are three data preservation commands available in DriveSpy:
- SavePart:The main function of the SavePart command is to generate an image of a partition. The syntax of the SavePart command is as follows:
SAVEPART [Destination File]
Investigators mainly make use of the SavePart command in DriveSpy to create a compressedforensic image of the present partition. SavePart allows an investigator to span media to store the complete image when necessary. After creating an image of the partition, DriveSpy provides a summary of the MD5 hash that is maintained for the image to ensure data integrity when the image is restored.
- WritePart:The main function of the WritePart command is to restore an image of a partition. The image can be one that is stored in the partition that is being examined. The syntax of the WritePart command isas follows:
WRITEPART [Source File]
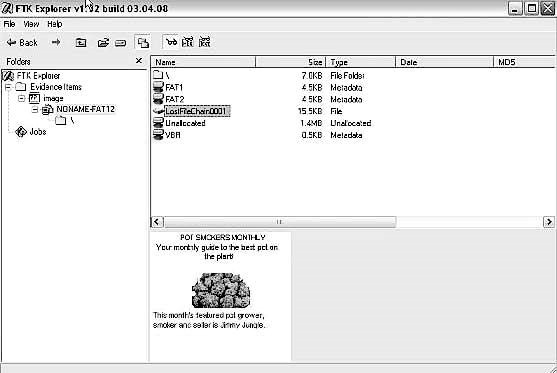
Figure 2-1FTK Imager is a powerful data acquisition tool.
If the image is stored across many parts of media, the WritePart command would automatically look for the media that is necessary.
- CopySect:The main function of the CopySect command is to copy sectors from one disk to a location on the same disk or on a different disk. The syntax of the CopySect command is as follows:COPYSECT [Source Sector Range] [Destination Sector Range]
Forensic investigators mostoften use the CopySect command as it helps in creating direct disk-to-disk images of suspect media.
FTK Imager
The Forensic Toolkit Imager (FTK Imager) is a commercial forensic imaging software package distributed by AccessData.
FTK Imager allows a forensic investigator to acquire physical device images and logically view data from FAT, NTFS, ext2, ext3, HFS, and HFS file systems. Figure 2-1 shows the main FTK Imager screen.
Mount Image Pro
Mount Image Pro is a computer forensics tool that allows an investigator to mount the following types of images:
EnCase
UNIX/Linux dd
SMART
ISO
Key Features of Mount Image Pro
The following are the key features of Mount Image Pro:
It maps an image as a single drive letter so that an investigator can explore unused or unpartitioned disk space or map specific drive letters to any or all partitions within the image files. Figure 2-2 shows an image selection screen in Mount Image Pro.
It fully maintains MD5 hash integrity.
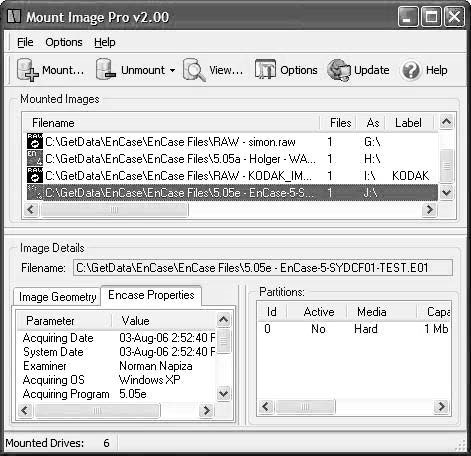
Figure 2-2An investigator can examine the properties of an image in Mount Image Pro.
It will open EnCase password-protected image files without the password.
It is compatible with third-party file-system drivers for Linux.
System Requirements for Mount Image Pro
The following are the system requirements for Mount Image Pro:
Operating system: Windows 2000/XP/2003/Vista
RAM: 128 MB recommended
Hard disk: At least 6 MB of free disk space
Drive SnapShot
Drive SnapShot is a dataacquisition tool that creates an exact disk image. It can create this image while an investigator continues doing his or her work in Windows. Booting into DOS is not necessary. It is compatible with all Windows file systems and most Linux file systems. Only a user with administrative privileges can use Drive SnapShot. Figure 2-3 shows the startup screen for Drive Snapshot.
System Requirements for Drive SnapShot
Operating system: Windows NT 4.0 SP3/2000/XP/2003/PE/Vista
RAM: 8 MB
Hard disk: At least 2 MB offree disk space
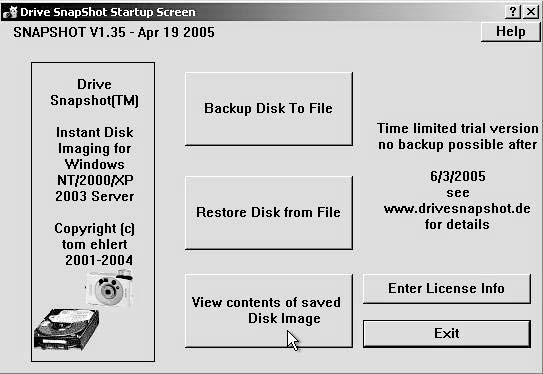
Figure 2-3Drive SnapShot can create disk images of Windows and Linux file system disks.
SnapBack DatArrest
DatArrest is a tool used for disk imaging and file recovery. A user can make an image of a server while it is running and being used. When using DatArrest, a user can copy the following:
Server or PC hard drive to removable media
Hard drive to hard drive
Tape to tape
Images captured by DatArrest contain all the system software, networking software, associated drivers, software applications, configurations, data files, and CMOS settings for the system.
SafeBack
SafeBack is a data acquisition tool that investigators can use to create bit-stream backups of entire hard drives or partitions on hard drives. It ensures data integrity using CRC-32. SafeBack creates a log file of all transactions it performs.
Data Acquisition Hardware Tools
Forensic investigators use a variety of hardware tools to acquire data from a suspect’s computer systems both in the lab and in the field. Some of these tools acquire data by connecting directly to the storage devices, while others can acquire data throughFirewire or USB ports.
Image MASSter Solo-3
The Image MASSter Solo-3 is a lightweight handheld tool that investigators use to acquire data. It can pull data off of PATA, SATA, and SCSI notebook and desktop hard drives. It can also pull data off of flash memory cards. An investigator can also connect the device to a computer’s USB or Firewire port and acquire data from any storage device in the system. The Image MASSter Solo-3 can copy up to two evidence disks at a time at speeds exceeding 3 GB/min. Figure2-4 shows the Image MASSter Solo-3 with two evidence disks attached.
Data Acquisition Hardware Tools

Figure 2-4The Image MASSter Solo-3 performs high-speed data acquisition.
The following are the specifications of the Image MASSter Solo-3:
Supply voltage: 90–230 V/50–60 Hz
Power consumption: 10 W without drives
Operating temperature: 5°C–55°C
Relative humidity: 20%–60% noncondensing
Net weight: 2.2 lbs
Overall dimensions: 8.3” 5.8” 2.2”
Power supply: UL and PSU certified, with universal autoswitching input voltage The following are some of the features of the Image MASSter Solo-3:
MD5 and CRC-32 hashing: MD5 and CRC-32 hashing ensure data integrity.
Touch-screen user interface: The unit’s advanced touch-screen user interface and programmable keyboard provide for ease of use.
Built-in write protection: The suspect drive’s data is protected with built-in write protection.
Audit trail and logs: An investigator can print detailed operational event log information or save it to a CompactFlash card.
Upgradeability: An investigator can perform software and firmware upgrades using a CompactFlash card. The following are some of the software features of the Image MASSter Solo-3:
Device configuration overlay (DCO) option: DCO can be used to hide and protect part of a drive from the operating system and file system. If the Image MASSter Solo-3 detects a DCO on a suspect’s drive, it can capture this hidden data.
Host protected area (HPA) option: An HPA may exist on a drive, hiding a certain portion of the drive’s contents from the operating system and file system. If an HPA exists on a suspect’s drive, the ImageMASSterSolo-3 can acquire data stored in the HPA.
WipeOut DoD option: WipeOut was designed to meet the U.S. Department of Defense specification DOD 5220-22M, regarding the sanitization of hard disk drive data. WipeOut performs three iterations to completely erasethe contents of a hard drive.
WipeOut fast option: The WipeOut fast option provides a quick non-DoD method of sanitizing a drive of all previously stored data.
Linux dd capture option: The Linux dd capture option captures data as individual Linux dd segmented files. This option allows an investigator to perform multiple data acquisition operations using the same evidence drive.
LinkMASSter-2
The LinkMASSter-2 acquires data from a laptop or desktop by imaging a suspect’s hard drive through the computer’s USB or Firewire ports. It captures data at speeds exceeding 3 GB/min. It uses write protection and supports MD5, CRC-32, and SHA-1 hashing to ensure data integrity. Figure 2-5 shows the LinkMASSter-2 attached to a laptop.
The following are the specifications of the LinkMASSter-2:
Supply voltage: 100–240 V/50–60 Hz
Power consumption: 3.5 W without drives
Operating temperature: 5°C–55°C
Relative humidity: 20%–60% noncondensing
Net weight: 0.55 lb
Overall dimensions: 5.5” 3”1”
Power supply: universal autoswitching input voltage
The following are some of the features of the LinkMASSter-2:
Forensic toolkit graphical user interface: The LinkMASSter-2 forensic toolkit application provides all the tools necessary to perform high-speed data acquisition operations. The interface runs on the Windows XP Professional platform.
Multiple media support: The device supports data transfers between PATA, SATA, and SCSI hard drives. With its built-in 2.5” interface, it supports capturing datato notebook drives.
Audit trail and logs: An investigator can print detailed operational event log information or save it.

Figure 2-5The LinkMASSter-2 reads data through USB and Firewire ports.
Data Acquisition Hardware Tools
The following are some of the software features of the LinkMASSter-2:
LinkMASSter application: The LinkMASSter application is run from the supplied LinkMASSter bootable CD, which provides write protection for the suspect’s drive during initialization and during data acquisition.
Single capture option: The single capture option allows an investigator to acquire data using a forensic sector-by-sector format method.
Linux dd capture option: The Linux dd capture option supports seizing the entire contents of a suspect’s drive by capturing data as individual Linux dd segmented files, which are then stored in individual subdirectories on the evidence drive. This option allows any number of seizures to be performed using the same evidence drive, provided there is adequate space to save the seized data.
Intelligent capture option: The intelligent capture option (IQCopy) provides a fast method of acquiring data from FAT16, FAT32, and NTFS file systems. This method analyzes the file system and captures only the allocated drive space.
WipeOut DoD option: This option is designed to erase all data on disk drives.WipeOut was designed to meet the U.S. Department of Defense specification DOD 5220-22M, regarding the sanitization of hard disk drives.
WipeOut fast option: The WipeOut fast option provides a quick non-DoD method of sanitizing a drive of all previously stored data.
RoadMASSter-2
The RoadMASSter-2 is a forensic data acquisition and analysis tool designed for use in the field. It provides an investigator with all the tools necessary to acquire and analyze data from Firewire and USB ports, flash memory cards,and PATA, SATA, and SCSI disks. Figure 2-6 shows the RoadMASSter-2. The following are the specifications of the RoadMASSter-2:
Supply voltage: 100–240 V/50–60 Hz
Power consumption: 150 W without drives
Operating temperature: 5°C–55°C
Relative humidity: 20%–60% noncondensing
Net weight: 32 lbs
Overall dimensions: 13” 21” 7.5”
Power supply: universal autoswitching input voltage •Processor: AMD64 3500

Figure 2-6The RoadMASSter-2 is used for data acquisition in the field.
Memory: 2 GB RAM
Hard drive: 60 GB 7200 rpm internal IDE drive
Other storage: CD-RW, DVDRW, DVD-RW, floppy disk
Display: 15” TFT color LCD display
Card reader/writer: 1–7 multicard read/write slots and 1–7 multicard read-only slots
Sound system: Stereo speakers and line in/line outconnector
Operating system: Windows XP Professional
The following are some of the features of the RoadMASSter-2:
MD5, CRC-32, and SHA-1 hashing: These hashing techniques ensure data integrity.
Forensic toolkit graphical user interface: The RoadMASSter-2 forensic toolkit application provides an investigator with all the tools necessary to perform high-speed forensic data acquisition operations.
High-speed operation: Data transfer rates can exceed 3.3 GB/min.
Multiple capture methods: Investigators can acquire data using a forensic sector-by-sector format method or using a Linux dd segmented file format method. The Linux dd capture method allows an investigator to put multiple images on one evidence drive.
Built-in write protection:The data on the suspect’s drive is protected with built-in write protection.
Multiple media support: The RoadMASSter-2 supports data transfers between PATA, SATA, and SCSI hard disk drives. Interface ports and readers are available to support flash memorycards, external Firewire and USB drives, and DVD and CD media. The built-in 2.5” interface supports notebook drives.
Preview and analysis: The toolkit provides an investigator with the capability to preview and analyze a suspect’s write-protected data.
Au__dit trail and logs: An investigator can print detailed operational event log information or save it.
The following are some of the software features of the RoadMASSter-2:
WipeOut DoD option: This option is designed to completely erase data on disk drives.WipeOut was designed to meet the U.S. Department of Defense specification DOD 5220-22M, regarding the sanitization of hard disk drives.
WipeOut fast option: The WipeOut fast option provides an investigator with a quick non-DoD method of sanitizing a drive.
LinkMASSter application: The LinkMASSter application is run from the supplied LinkMASSter bootable CD, which provides write protection for the suspect’s drive during initialization and during data acquisition.
Intelligent capture mode: The intelligent capture option (IQCopy) provides a fast method of acquiring data from FAT16, FAT32, and NTFS file systems. This method analyzes the file system and captures only the allocated drive space.
Data Duplication Software Tools
Computer forensic investigators have many software tools at their disposal for the purpose of data duplication. These tools provide high-speed backup and imaging capabilities.
R-Drive Image
R-Drive Image is a software tool used to create disk images with various compression levels for backup or duplication purposes. A disk image file contains an exact byte-by-byte copy of a hard drive, partition, or logical disk. These image files can then bestored on a variety of media, including removable media such as CD-RWs and DVD-RWs. Figure 2-7 shows the action selection screen for R-Drive Image.
Data Duplication Software Tools
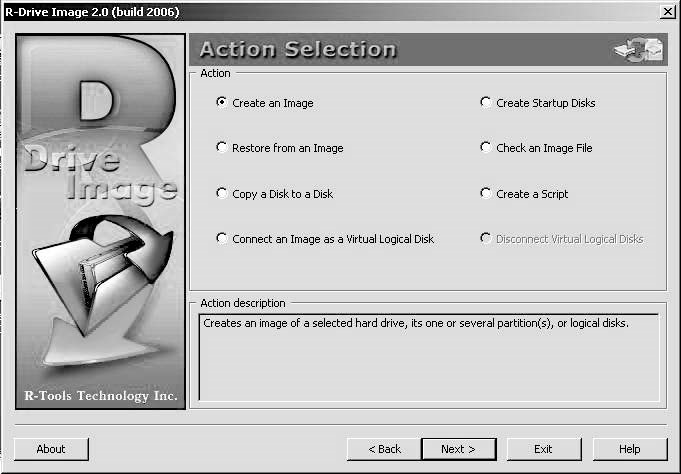
Figure 2-7R-Drive Image is used for data duplication.
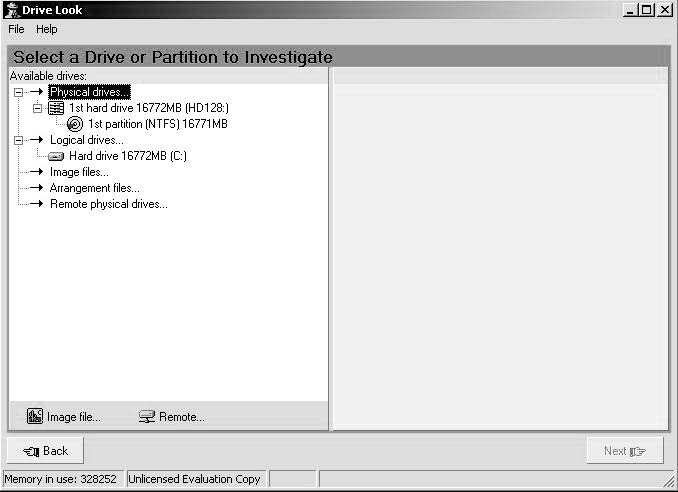
Figure 2-8DriveLook allows an investigator to remotely access drives.
DriveLook
DriveLook provides access to remote drives through serial cables or TCP/IP. Figure 2-8 shows a screenshot of DriveLook.
Forensic investigators use this tool to:
Index a drive for all text that has ever been written to it
Search the drive for particular words
View the location of words in a disk editor
Switch between hex and text views
Use image files as input
DiskExplorer
The DiskExplorer tool is a sophisticated disk editor that allows a forensic investigator to investigate a FAT or NTFS drive and recover data from it. Figure 2-9 shows a screen displaying the partition table of a drive. An investigator can perform the following tasks using DiskExplorer:
Navigate through the drive by jumping to the partition table, boot record, master file table, and root directory
Choose between views such as hex, text, index allocation, MFT, boot record, and partition table, and inspect file entry details
Save files and directories from anywhere on the drive
Identify the file a certain cluster belongs to
Create a virtual volume when the boot record is lost or corrupt
Edit the disk drive by using the direct read/write mode or the virtual write mode
Save-N-Sync
Save-N-Sync allows an investigator to synchronize and backup files from a source folder on one computer to a target folder on a second networked computer or local storage device. An investigator can manually or automatically schedule regular synchronization and backup operations. It works on Windows NT, 2000, and XP. Figure 2-10 is a screenshot from Save-N-Sync.
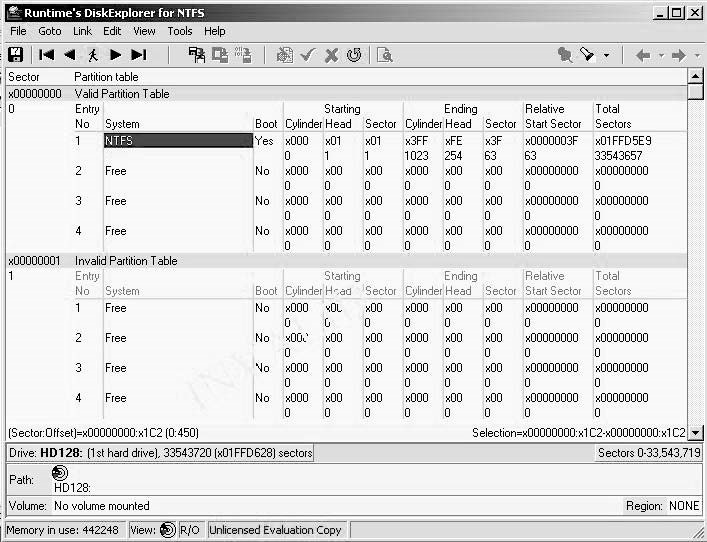
Figure 2-9DiskExplorer allows an investigator to recover data.
Data Duplication Software Tools
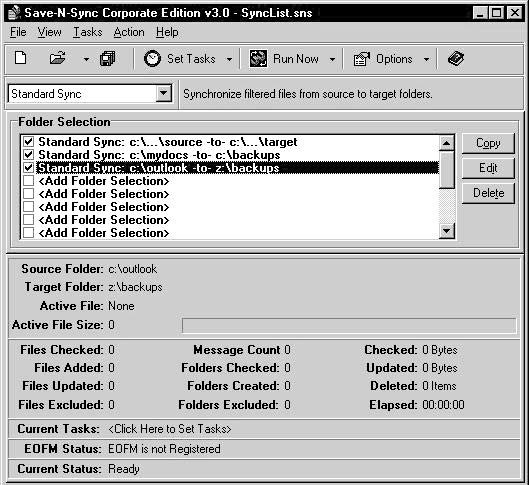
Figure 2-10Save-N-Sync is used for data backups and data synchronization.
The following are some of the features of Save-N-Sync:
Standard and bidirectional synchronization: Standard synchronization compares source and target files, and new or updated files on the source PC are copied to the target PC or storage device. Bidirectional synchronization adds the extra step of copying the files back to the source.
Daily timer: This feature allows an investigator to schedule file synchronizations for any time on any day of the week.
Unobtrusive background processing: An investigator can continue working, even during the synchronization process.
Embedded open file manager option: This option allows an investigator to backup locked files, such as Outlook and QuickBooks files.
F__ile attribute transfers: File attributes are maintained when a file is copied from the source to the target.
Extensive filtering capabilities: An investigator can include or exclude specific files or folders.
Command-line capabilities: Save-N-Sync can be launched from the command line, a batch file, or a script.
DFSMSdss
Data Set Services (DFSMSdss) is a component of IBM’s DFSMS (Data Facility Storage Management Subsystem). An investigator can use this tool to quickly and efficiently duplicate data. DFSMSdss can copy data from one disk to another or from a disk to a tape.
The following are some of the features of DFSMSdss:
Movement and replication of data: The tool offers powerful, user-friendly functions that allow an investigator to move or copy data between volumes of like and unlike device types. It can also copy data that has been backed up.
Backup and recovery of data: With this tool, an investigator can backup and recover data at both the data set and volume levels. An investigator can also use DFSMSdss to restore vital system packs during disaster recovery without a host operating system.
Conversion of data sets and__volumes: DFSMSdss converts data sets and volumes to system-managed storage, or returns data to a non-system-managed state, as part of a recovery procedure that doesn’t include moving data.
SCSIPAK
SCSIPAK is a software-based data conversion and duplication system. SCSIPAK is a set of system tools that extend the support of tape drives under Microsoft Windows NT and Windows 2000.
These tools allow an investigator to identify drives on a SCSI bus, transfer data between disks and tapes or optical discs, and copy data between tapes or optical discs.
SCSIPAK reads data from a tape or optical disc and simultaneously writes it to up to seven drives at once. The image file from the tape or optical medium is stored along with an index file, which contains details of the tape file and set marks, directory partitions, or unused optical sectors. This allows an investigator to duplicate even complex-format tapes and optical discs.
Data Duplication Hardware Tools
The data duplication hardware tools that forensic investigators use are high-speed, high-volume devices. Most of these tools also provide investigators with the capability to completely erase data from a disk.
ImageMASSter 6007SAS
The ImageMASSter 6007SAS is a high-speed data duplication device. It has a graphical Windows XP–based interface and a gigabit Ethernet connection. It can copy an SATA, SAS, SCSI, or IDE hard drive to any seven SAS, SATA, or IDE local or network hard drives. Figure 2-11 shows the ImageMASSter 6007SAS. The following are the specifications of the ImageMASSter 6007SAS:
Supply volt__age: 100–240 V/50–60 Hz
Power consumption: 125 W without drives
Operating temperature: 5°C–55°C
Relative humidity: 20%–60% noncondensing
Net weight: 40 lbs

Figure 2-11The ImageMASSter 6007SAS performs high-speed data duplication over local or network connections.
Data Duplication Hardware Tools
Overall dimensions: 21” 16.75” 6.75”
Power supply: UL and PSU certified universal autoswitching input voltage The following are some of the features of the ImageMASSter 6007SAS:
High-speed copy operation: Data transfer rates exceed 3.7 GB/min.
Multiple copy modes: The device supports sector-by-sector and data-only copying. Multiple images can be stored on a single target drive.
Hot swapping of drives: Hard drives can be removed or connected while the system is on (hot swap). The following are some of the software features of the ImageMASSter 6007SAS:
IQCopy: IQCopy provides a fast method of duplicating Windows 95, 98, 2000, and XP drives. The device analyzes the file system and copies only the allocated drive space. IQCopy automatically scales hard drive partitions to the size of the target drive. It allows an investigator to mix different-sized drives in the same duplication process. IQCopy can create a fully operational data copy in under a minute.
Image copy: The ImageMASSter 6007SAS transfers data using a sector-by-sector copy method to produce an exact image of a source drive. All allocated and unallocated drive space is copied. The device supports all operating systems and file systems.
WipeOut DoD option: This function is designed to erase all data on hard disk drives, to U.S. Department of Defense specification DOD 5220-22M. An investigator can sanitize up to nine drives simultaneously at speeds exceeding 3 GB/min.
WipeOut fast option: The WipeOut fast option provides a quick non-DoD method of wiping hard drives of all previously stored data.
Log information display and storage: The device provides functions to display and store real-time event information in a log.
Error detection and verification: The ImageMASSter 6007SAS provides automatic real-time CRC-16 error detection and correction.
Management of user-defined settings: This built-in feature allows authorized users to store multiple user-defined unit settings.
Disk Jockey IT
Disk Jockey IT is a high-speed data duplication tool. It can copy data from PATAand SATA desktop and laptop drives. It is a lightweight handheld device that can copy data to one or two target drives at speeds exceeding 2 GB/min. Figure 2-12 shows the Disk Jockey IT.
The following are some of the features of the Disk Jockey IT:
- Stand-__alone HD mode: An investigator can mount one or two PATA or SATA hard drives on a Windows or Macintosh computer, through Firewire or USB 2.0, without installing any extra drivers. The Disk Jockey IT includes 2.5” laptop adapter cables and 3.5” desktop cables.

Figure 2-12The Disk Jockey IT can copy data from one drive to one or two target drives.
Mirroring: The Disk Jockey IT allows an investigator to mirror two hard drives for real-time backup (RAID 1). If one drive fails, there will be no downtime, as the data is stored simultaneously on the second drive.
Spanning: An investigator can easily make one large logical volume from two disks attached to the Disk Jockey IT. The investigator can then connect the Disk Jockey IT to a Firewire or USB port on a Windows or Macintosh computer to access the two drives as standard external storage.
Disk copy compare/ver__ification: This feature allows an investigator to verify that a copy is an exact duplicate, ensuring that there is no data loss.
Hard disk read test: The Disk Jockey IT can perform a sector-by-sector hard disk read test to test the overall health of a hard drive.
Two levels of erasure: The Disk Jockey IT offers two levels of disk erasure. The first is a fast, one-pass erase. The second is a more thorough three-pass erase that an investigator can use when he or she needs to feel more confident that the datais irretrievably erased.
QuickCopy
QuickCopy is a tape duplication system. The following are some of the features of QuickCopy:
Duplicates a master tape to one or more target tapes
Duplicates from master images stored on local or network hard drives
Capable of multitasking for mixed jobs. For instance, it can duplicate a 4-mm tape and a DLT simultaneously.
Provides 100% verification of all copies made
Uses the Microsoft NT operating system and graphical user interface (GUI)
Can also copy CD media with theQuickCopy-CD option
Chapter Summary
■This chapter has discussed the different procedures that forensic investigators follow in the duplication, acquisition, and preservation of data.
■Investigators can acquire data in three ways: by creating a bit-stream disk-to-image file, by making a bit-stream disk-to-disk copy, or by creating a sparse data copy of a specific folder or file.
■Data duplication is essential for the proper preservation of digital evidence.
■Windows data acquisition tools allow an investigator to easily acquire evidence from a disk with the help of removable media, such as USB storage devices.
■Forensic investigators use the built-in Linux command dd to copy data from a disk drive.
■The SavePart command generates an image of a partition on a hard disk.
Review Questions
- What are the methods investigators use to acquire digital evidence?
- How does an investigator acquire data on Linux?
- What do the SavePart and WritePart commands in DriveSpy do?
- Why is there a need for data duplication?
- How is netcat used with dd to acquire data?
- Write down the hardware tools used for data acquisition.
- Write down the hardware tools used for dataduplication.
- What file systems does dd work with?
- Describe the features of QuickCopy.
- What are the system requirements for Drive SnapShot?
Hands-On Projects
 Follow these steps:
Follow these steps:
■Navigate to Chapter 2 of the Student Resource Center.
■Change to the dd\bin\UnicodeRelease directory.
■Type the following command:dd if \.\D:\pagefile.sys ofd:\myimage.img
(You can replace the file with PhydicalDrive0 to image the complete disk.)
Figure 2-13 shows a screenshot of this process.
- Follow these steps:
■Navigate to Chapter 2 of the Student Resource Center.
■Install and launch Mount Image Pro.
■ClickMount(Figure 2-14).
Copyright 2010 Cengage Learning, Inc. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part.
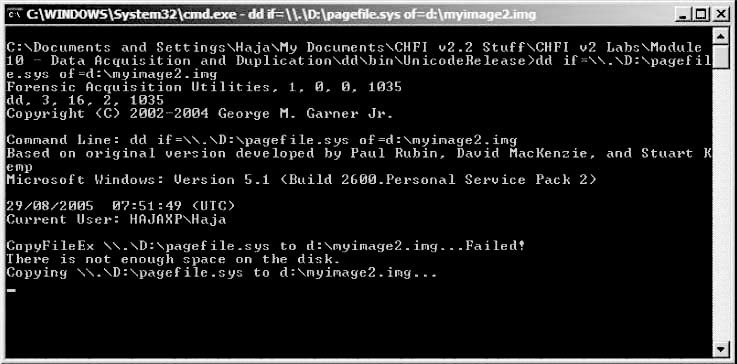
Figure 2-13An investigator can use dd to image a disk.
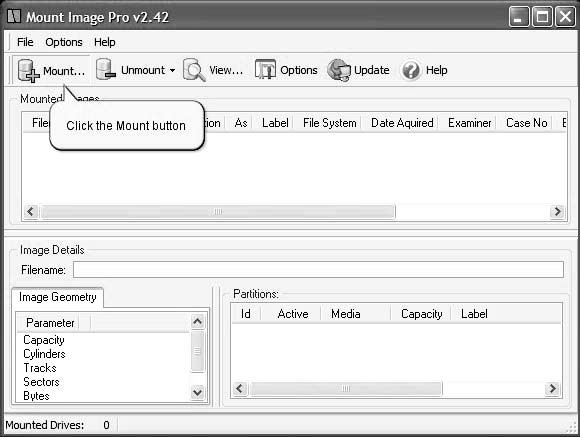
Figure 2-14Click the Mount button to choose the image file to mount.
Select the EnCase image file (Figure 2-15).
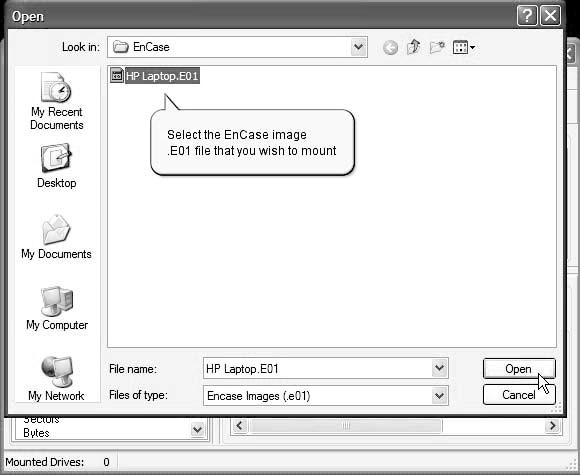
Figure 2-15Select the image file that you want to mount.
■Select the proper start drive letter.
■Check theMount as single drivebox and clickOK(Figure 2-16).
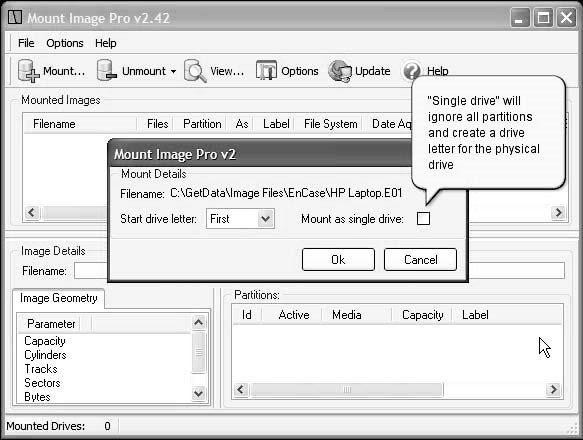
Figure 2-16Choose this option to mount the entire image as a single drive.
Click on theEncase Propertiestab (Figure 2-17).
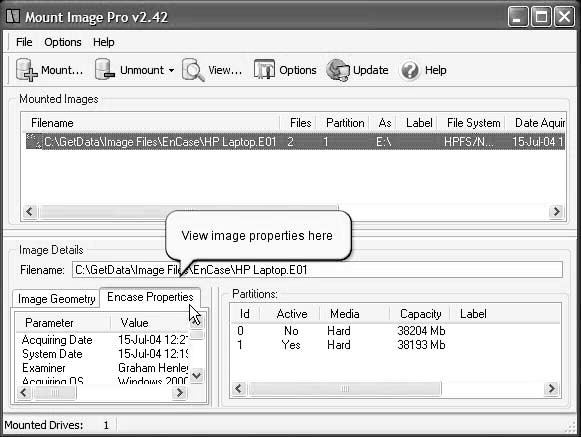
Figure 2-17You can view the properties of the image once you’ve mounted it.
■Double-click the mounted image to open Windows Explorer (Figure 2-18).
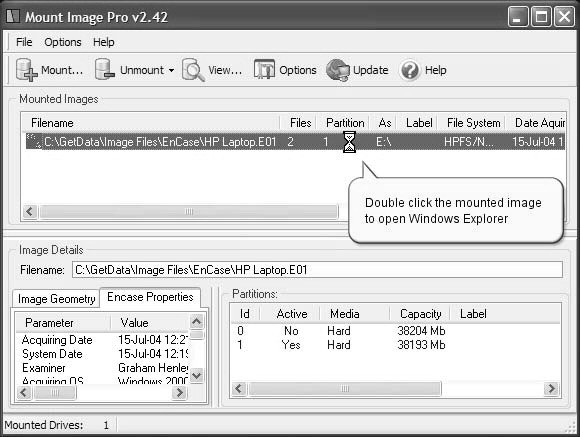
Figure 2-18You can double-click the mounted image to open it in Windows Explorer.
Browse the read-only contents of the EnCase image in Windows Explorer (Figure 2-19).
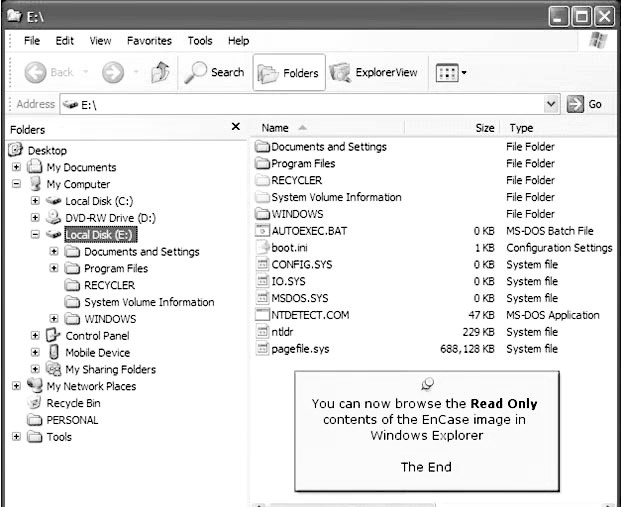
Figure 2-19This is the contents of the mounted image. Note that the image can’t be written to.
3. Follow these steps:
■Navigate to Chapter 2 of the Student ResourceCenter.
■Install and launch the R-Drive Image program.
■ClickNext(Figure 2-20).
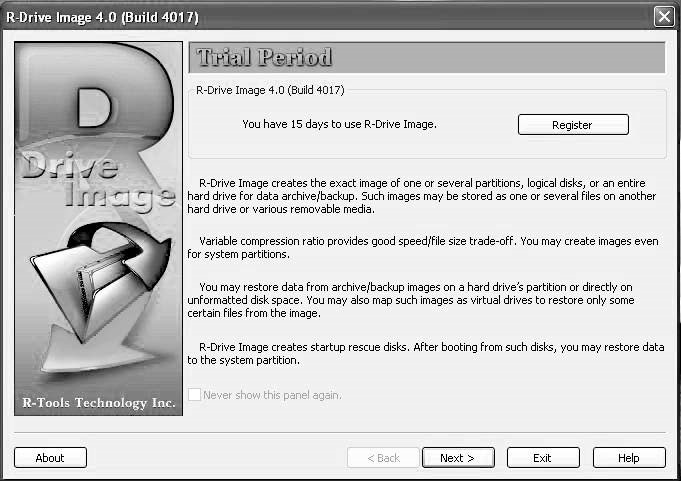
Figure 2-20This is the opening screen for R-Drive Image.
Create an Image(Figure 2-21).
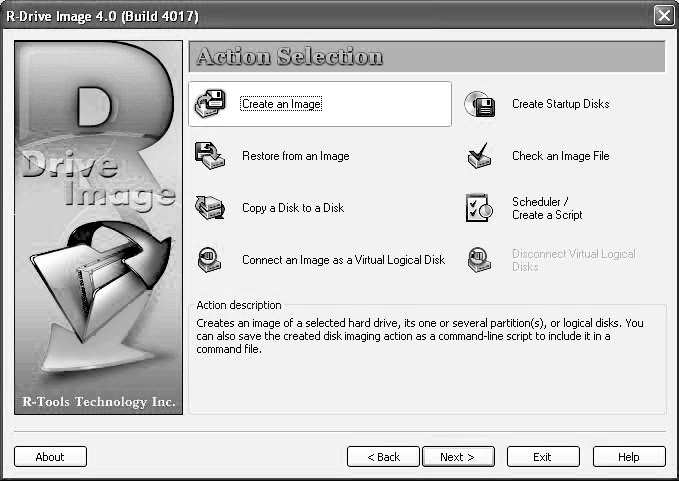
Figure 2-21R-Drive Image can create images of entire hard drives or individual partitions.
■ClickNext.
■Select a partition and clickNext(Figure 2-22).
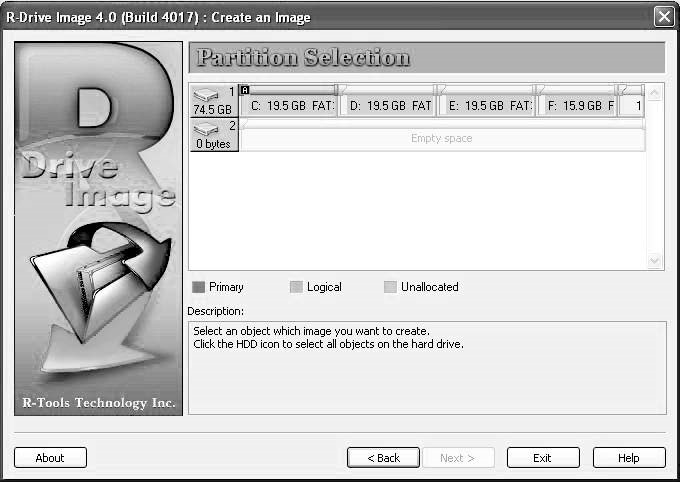
Figure 2-22R-Drive Image shows information about all partitions on a drive during the selection process.
Select a destination and clickNext(Figure 2-23).
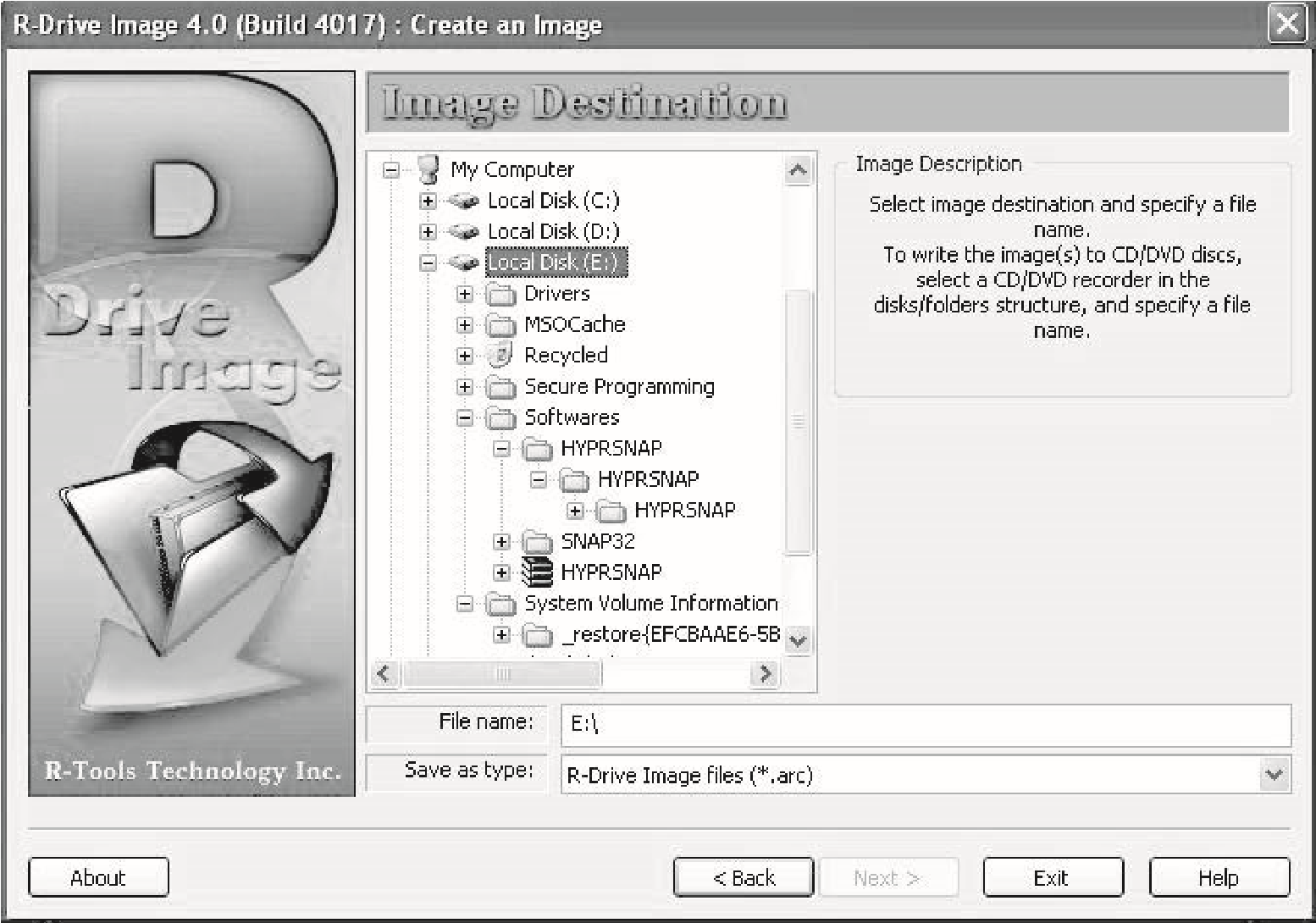
Figure 2-23R-Drive Image can write images to various types of media, including hard disks and optical media.
4. Follow these steps:
■Navigate to Chapter 2 of the Student Resource Center.
■Install and launch the Save-N-Sync Corporate Edition program.
Addand specify the source and target folders (Figure 2-24).
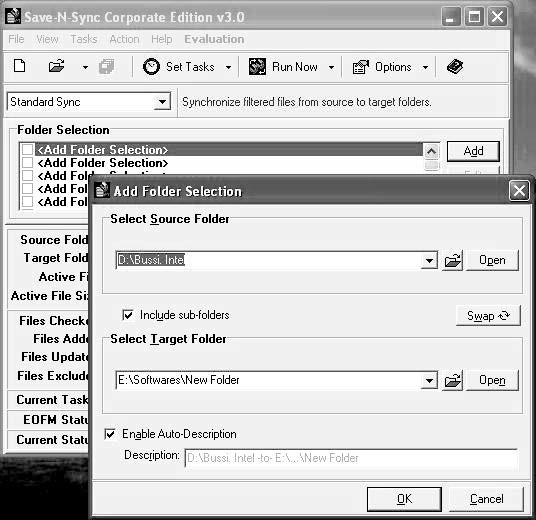
Figure 2-24Specify the source and target folders.
■ClickOK.
ClickRun Now(Figure 2-25).
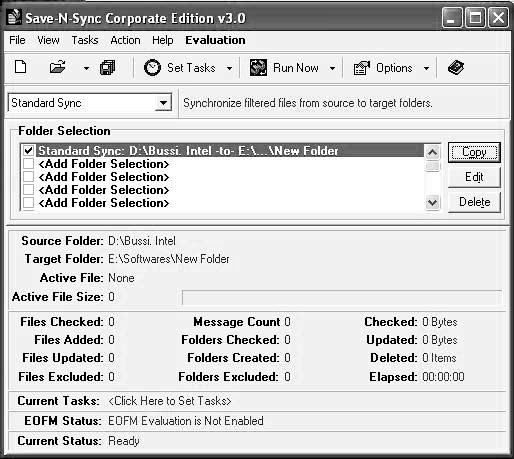
Figure 2-25ClickRun Nowto finalize your selections.
■ClickYesto save the changes (Figure 2-26).
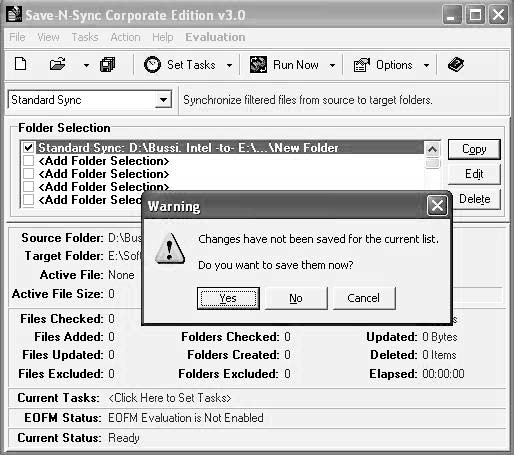
Figure 2-26ClickYesto save the changes you have made.
■OK(Figure 2-27).
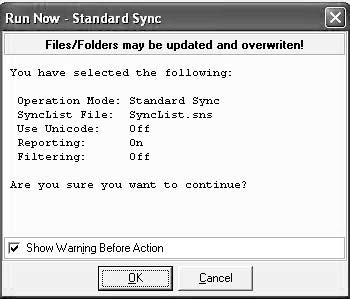
Figure 2-27ClickOKto start the sync process.
5. Follow these steps:
■Navigate to Chapter 2 of the Student Resource Center.
■Install and launch the FTK Imager program.
■ClickFileand then click onAdd Evidence.
■ChooseLogical Driveas the source evidence type (Figure 2-28).
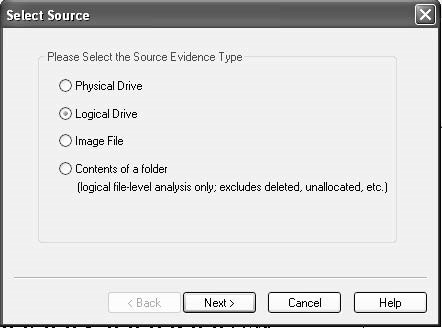
Figure 2-28The source evidence for this project is a logical drive, so chooseLogical Drive.
ClickNextand select the drive (Figure 2-29).
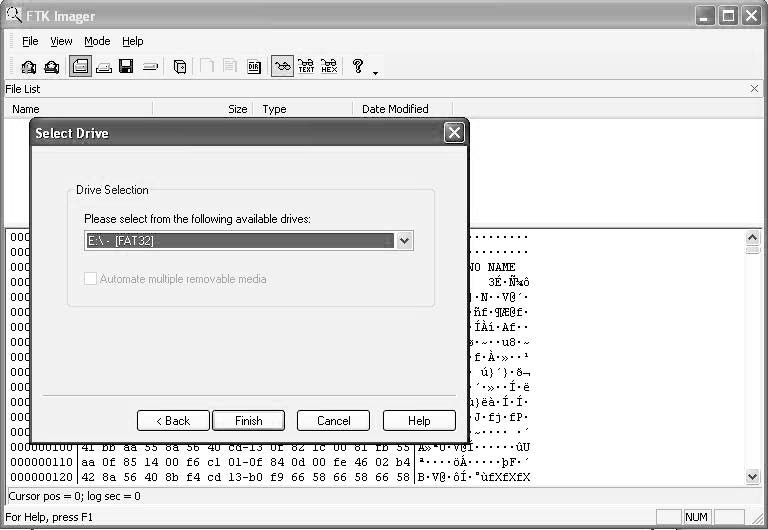
Figure 2-29Choose the drive you want to use as evidence.
■ClickFinishand view the results (Figure 2-30).
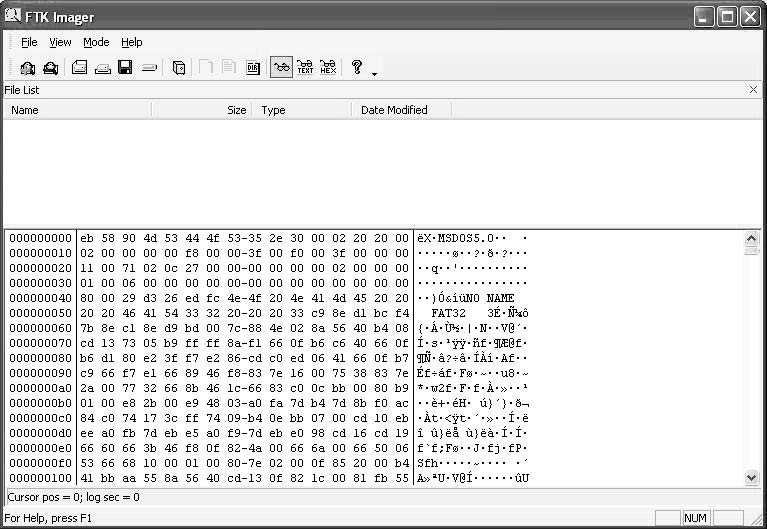
Figure 2-30This is how the screen will look after adding the drive as evidence.
Objectives
After completing this chapter, you should be able to:
Understand evidence files
Verify evidence file integrity
Perform hashing
Configure EnCase
Search using EnCase
Use bookmarks in EnCase
View recovered files
Understand the master boot record
Understand the NTFS starting point
Understand hash values
Perform signature analysis

Forensic**Investigations**
Using**EnCase**
Chapter
3
Perform e-mail recovery
Key Terms
Cyclic redundancy check (CRC)a type of function that takes a quantity of data of any size and produces an output of a fixed length, usually a 32-bit integer that is generally used to verify the integrity of the original data
Checksum(also called a hash sum) a fixed-size integer resulting from the application of an algorithm to a block of digital data for the purpose of verifying the integrity of the original data; often used when comparing copied data with the original data
Hashinga well-defined mathematical function that converts a large variable-sized amount of data into a small fixed-length integer that may serve as an index into an array, as a method of obscuring and protecting passwords being transferred over a network, or to verify the integrity ofstored data; Message Digest v5 (MD5) and Secure Hashing Algorithm (SHA) are two of the most common hashing functions.
3-1
Introduction to Forensic Investigation Using EnCase
This chapter focuses on forensic investigation using EnCase. EnCase is a forensic software suite that provides investigators with a full set of tools for forensic investigations. The chapter gives some information about EnCase and discusses how investigators can use EnCase to perform different forensic tasks.
Evidence Files
An evidence file is the core component of EnCase. It is a proprietary file created by EnCase to compress and preserve bit-stream images of acquired media. The EnCase evidence file is widely known throughout the law enforcement and computer security industries. Courts in the United States, including at the federal appellate level, and in the international community have accepted EnCase evidence files in both civil and criminal cases.
EnCase evidence files are used to preserve evidence and continue the examinationwithout having to restore the image to separate media. The bit-stream image in an EnCase evidence file can be mounted as a read-only file or virtual drive, from which EnCase reconstructs the file structure using the logical data in the bit-stream image. This allows the investigator to search and examine the contents of the acquired drive within the EnCase Enterprise Examiner environment. The EnCase evidence file contains an exact copy of the data from the original media, including time stamps, deleted files, unallocated space, and file-system attributes. An investigator can easily transfer an EnCase evidence file to different types of media and archive it for future reference. If necessary, an investigator can also use the evidence file to restore the exactimage to another hard drive. An evidence file consists of the following:
Header: The header contains the date and time of evidence acquisition, the examiner’s name, notes on the acquisition, an optional password, and its own cyclic redundancy check (CRC) checksum.CRCis a type of function that takes a quantity of data of any size and produces an output of a fixed length, usually a 32-bit integer that is generally used to verify the integrity of the original data. Achecksumis a fixed-size integer resulting from the application of this algorithm. The header is always prefixed withCase Info.
Checksum: One of the main parts of an EnCase evidence file is CRC checksums. An evidence file saves checksums for every block of 64 sectors (~32 KB) of evidence.
Data blocks: Data blocks contain an exact replica of the original evidence. EnCase saves a bit-stream image of evidence.
Footer: The footer contains an MD5 hash for the entire bit-stream image.
Verifying Evidence Files
After burning the discs, an investigator can runVerify Evidence Filesfrom theToolsmenu on each disc to verify that the burn was thorough and that the evidence file segment is intact.
Evidence File Format
Each evidence file is an exact sector-by-sector copy of a floppy or hard disk. Every byte of the file is verified using a 32-bit CRC, and it is virtually impossible to tamper with the evidence once it has been acquired.
EnCase uses ASR Data’s Expert Witness Compression Format for storing images of evidence; this format can reduce file sizes by up to 50%.
EnCase can store media data in multiple evidence files called segment files. Each segment file consists of multiple sections. Each section consists of a section start definition. This definition contains a section type.
From version 4 onward, EnCase has had two header sections, header and header2. The header section is defined once, and the header2 section is defined twice within the file; both copies of header2 contain the same information.
Evidence Files
Verifying File Integrity
Whenever an investigator adds an evidence file to a case, he or she can use EnCase to verify the integrity of the file (Figure 3-1).
Hashing
Hashingis a well-defined mathematical function that converts a large variable-sized amount of data into a small fixed-length integer that may serve as an index into an array, as a method obscuring and protecting passwords being transferred over a network, or to verify the integrity of stored data. EnCase calculates an MD5 hash when it acquires a physical drive or logical drive, as shown in Figure 3-2.
Figure 3-1Verifying file integrity is a crucial step during an investigation.
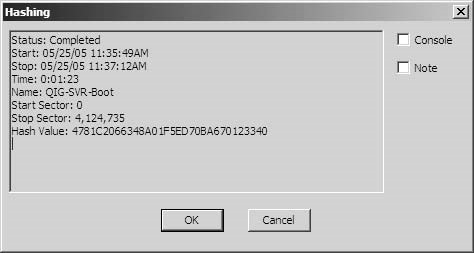
Figure 3-2MD5 hashing helps to verify file integrity.
Acquiring an Image
An investigator can acquire an image by performing the following steps:
ClickFileand thenAdd Deviceto acquire the image. The investigator can alternately click theAdd Devicebutton on the toolbar. Figure 3-3 shows a screenshot of this process.
Select the device type. If the device is a USB drive, it should not be connected to the forensic computer prior to the boot process.
Configuring EnCase
An investigator can clickToolsand thenOptionsto configure EnCase. Figures 3-4 and 3-5 depict some of theOptionsscreens.
View Menu
An investigator can launch various utilities using theViewmenu (Figure 3-6). TheViewmenu includes the following options:
Cases
File types
File signatures
File viewers
Keywords
Search IDs
Text styles
Scripts
Hash sets
Encryption keys
EnScript types
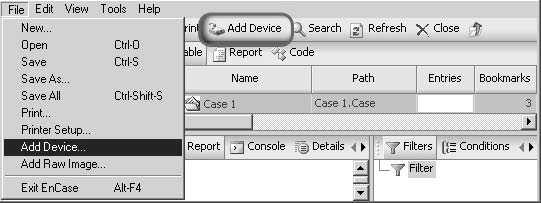
Figure 3-3An investigator can acquire an image of a device by adding the device to the evidence file.
View Menu
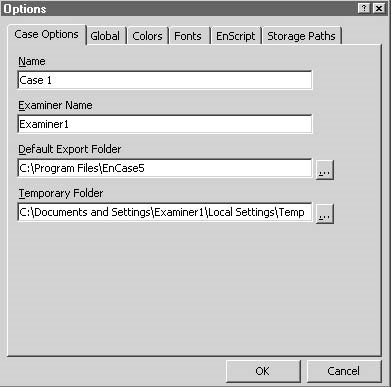
Figure 3-4TheCase Optionstab allows an investigator to configure basic options about a case.
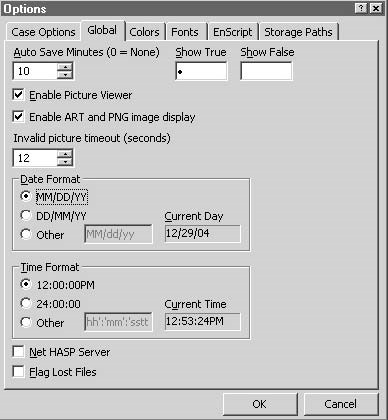
Figure 3-5TheGlobaltab allows an investigator to configure program options.
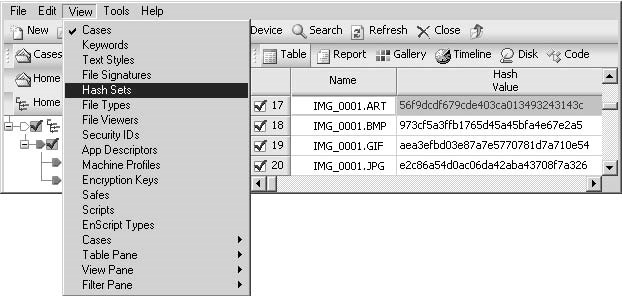
Figure 3-6TheViewmenu provides an investigator with many different utilities.
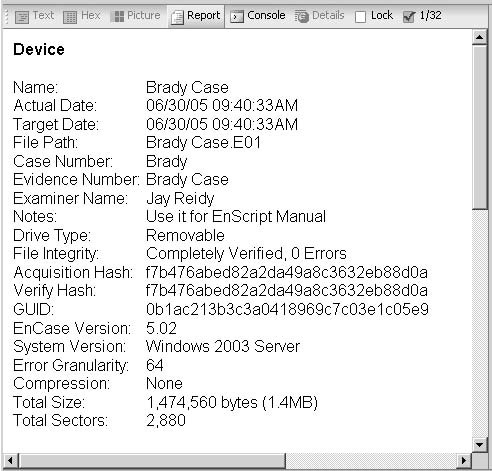
Figure 3-7TheDevicereport displays important information about an acquired device.
Device Tab
TheDevicereport shows information about the currently selected device, as shown in Figure 3-7. The information displayed includes the following:
Evidence number
File path
Examiner name
Status Bar
Actual date
Target date
Total size
Total sectors
File integrity
EnCase version
System version
Acquisition hash
Verify hash
Notes
Status Bar
The status bar (Figures 3-8 and 3-9) provides the following sector details for a selected file:
- Physical sector number• Logical sector number
Figure 3-8An investigator can view information about EnCase’s current task in the status bar.
Figure 3-9Thisshows a closer view of the status bar.
Cluster number
Sector offset
File offset
Length
Searching
EnCase provides powerful searching capabilities. An investigator can perform keyword searches at the logical level (file level) or physical level (byte-by-byte). EnCase can locate information anywhere on physical or logical media by using its deep analysisfeatures. EnCase has the following advanced search capabilities:
Concurrent search
Proximity search
Internet and e-mail search
E-mail address search
Global Regular Expressions Post (GREP) search: The GREP search utility enables the investigator to searchfor information with a known general format, such as any telephone numbers, credit card numbers, network IDs, logon records, or IP addresses, even when the specific number is not known
File finder: This searches within the page file, unallocated clusters,selected files or entire cases, looking for specific file types and structured data EnCase provides the following search options:
Case sensitive: EnCase searches for keywords only in the exact case specified in the text box.
GREP: The keyword is a regular expression.
RTL reading: This is a keyword search in a right-to-left sequence for international language support.
Active code page: This option allows an investigator to enter keywords in many different languages.
Unicode: This enables investigators to search for keywords with international language characters.
Big-endian Unicode: This enables investigators to search for keywords with international language characters.
Figure 3-10 shows a screenshot of theSearchwindow.
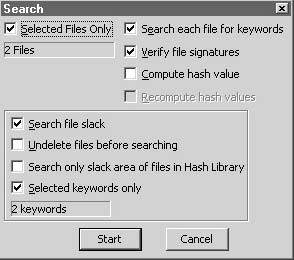
Figure3-10TheSearchwindow allows an investigator to choose different search options.
Searching
Keywords
A key component of any search is the keywords and their rules. Keywords are saved in the keywords.ini file.An investigator chooses keywords based on whathe or she is investigating. For example, the investigator might want to add keywords such as the following:
kill
suicide
cheat
Swiss bank
San Francisco
Adding Keywords
To add keywords, an investigator needs to right-clickKeywordand selectNew, as shown in Figures 3-11 and 3-12.
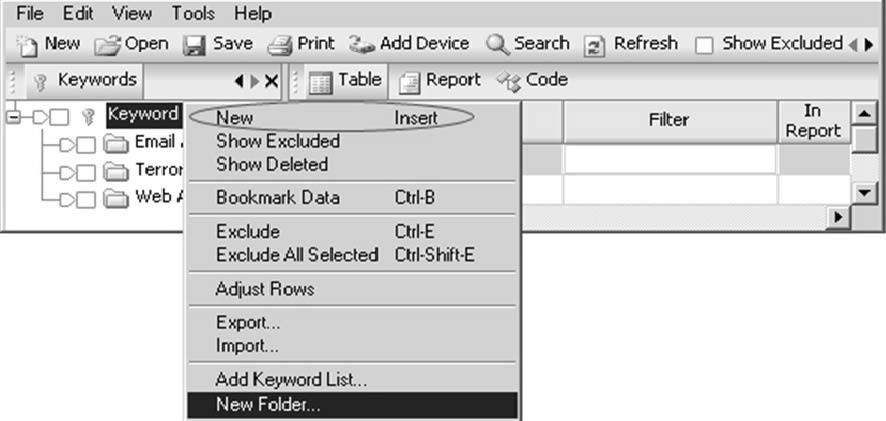

Figure 3-11TheKeywordmenu allows an investigator to add new keywords to a search.
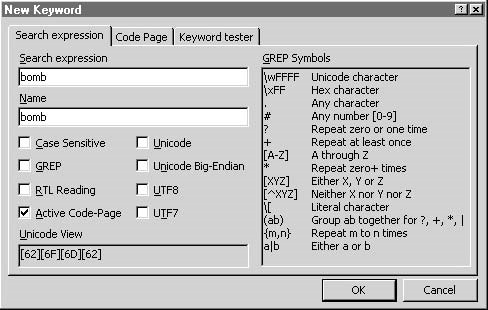
Figure 3-12An investigator can set options for keywords in theNew Keywordwindow.
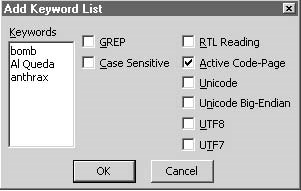
Figure 3-13TheAdd Keyword Listmenu allows an investigator to add a list of keywords to a search and set the same options on all of them.
Grouping Keywords
An investigator can group keywords to organize search terms. To do so, he or she right-clicksKeyword, selectsNew Folder, and types in a folder name.
Adding Multiple Keywords
To add multiple keywords, an investigator can right-click the keyword folder and chooseAdd Keyword List. Figure 3-13 shows a screenshot of theAdd Keyword Listwindow.
Starting the Search
An investigator cansearch a set of files, a set of folders, or an entire drive by performing the following steps:
Check the keywords that need to be searched.
Click theSearchbutton.
Search Hits Tab
TheSearch Hitstab reveals the search results, as shown in Figure 3-14.
Bookmarks
EnCase allows an investigator to bookmark files, folders, or sections of a file for easy reference. The investigator can view bookmarks by clickingViewand thenBookmark. Figure 3-15 shows theBookmarkstab.
Bookmarks
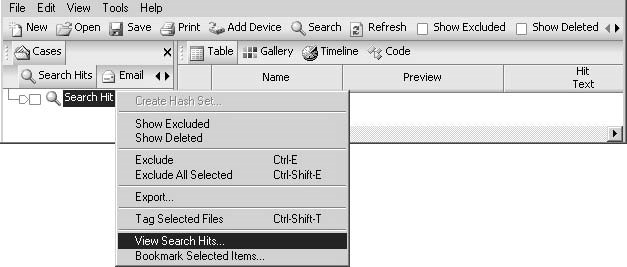
Figure 3-14TheSearch Hi**ts**tab shows the results of a search.
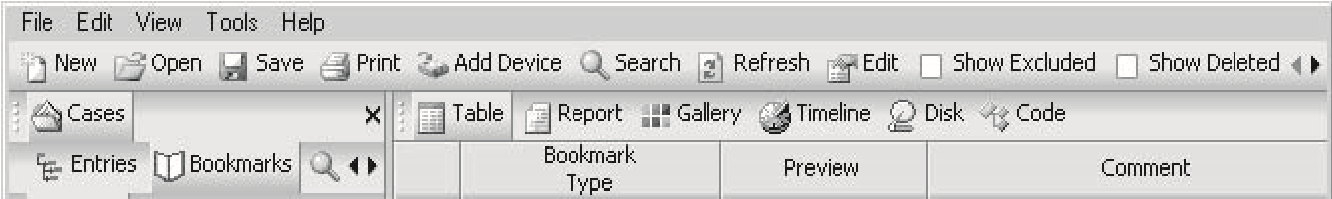
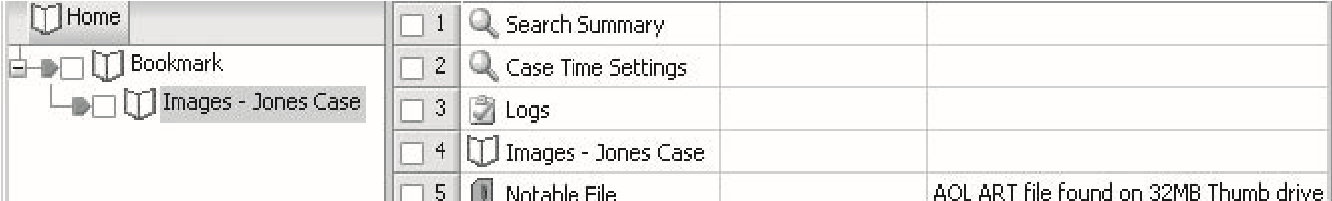
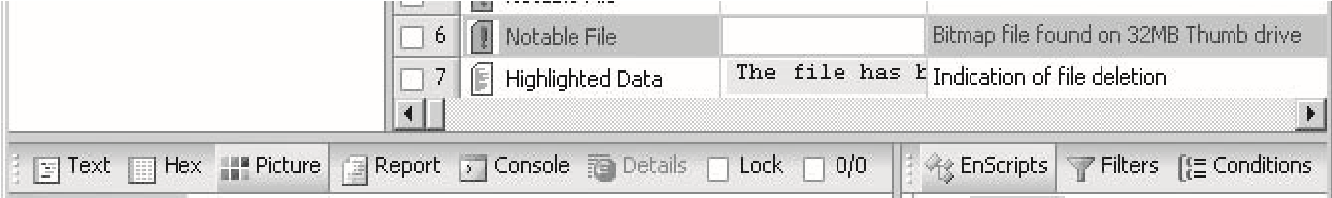

Figure 3-15TheBookmarkstab shows the bookmarks that an investigator has created.
Creating Bookmark Folders
An investigator can create a bookmark folder by checkingCreate new bookmark folderin theBookmark Fileswindow, as shown in Figure 3-16.
Adding Bookmarks
An investigator can add a bookmark by right-clicking on any file and selectingBookmark Files, as shown in Figure 3-17.
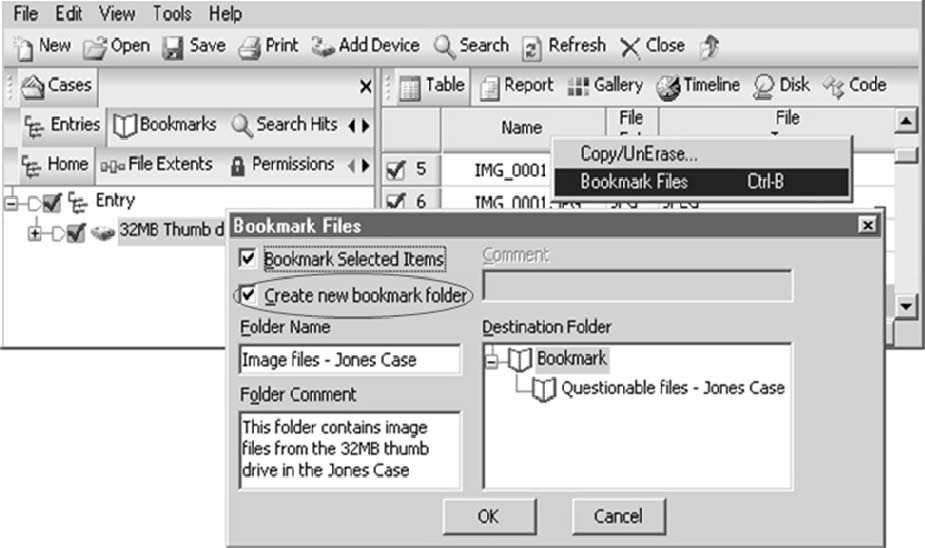
Figure 3-16Bookmark folders allow an investigator to organize bookmarks.

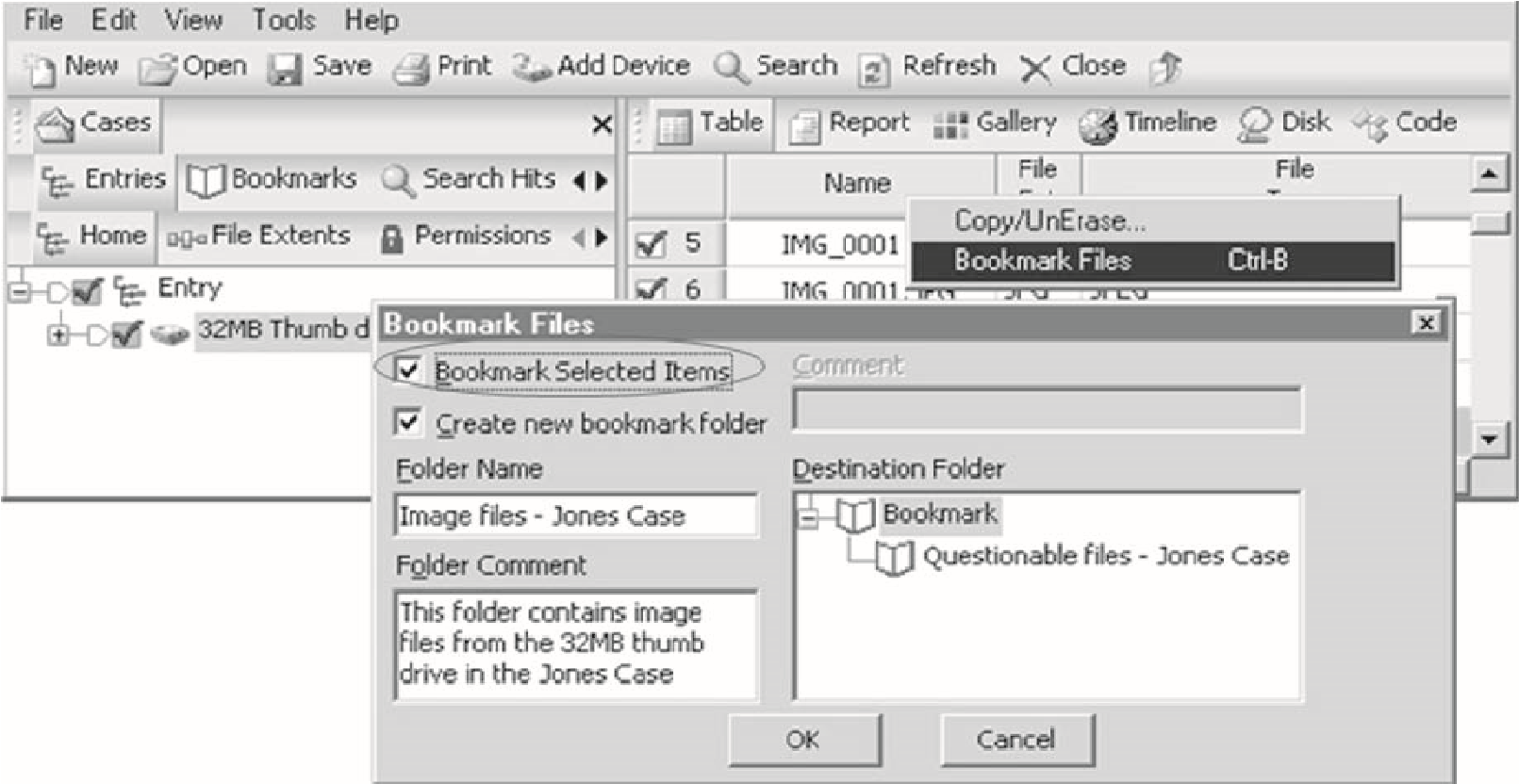
Figure 3-17An investigator can bookmark files easily.
Bookmarking a Selected Area
An investigator can bookmark a selected area by highlighting the text area and selectingBookmark Data, as shown in Figure 3-18.
Recovering Deleted Files/Folders in a FAT**Partition**
An investigator can recover deleted files and folders by right-clicking a FAT drive and selectingRecover Folders, as shown in Figures 3-19 and 3-20.
Recovering Files/Folders in an NTFS Partition
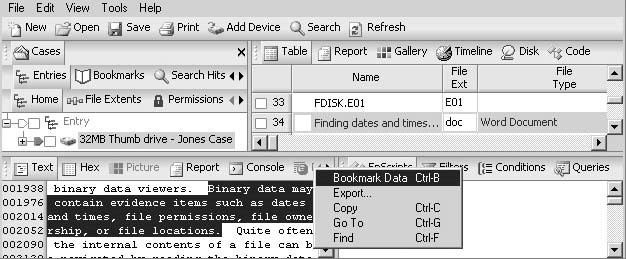
Figure 3-18An investigator can bookmark an area of text.
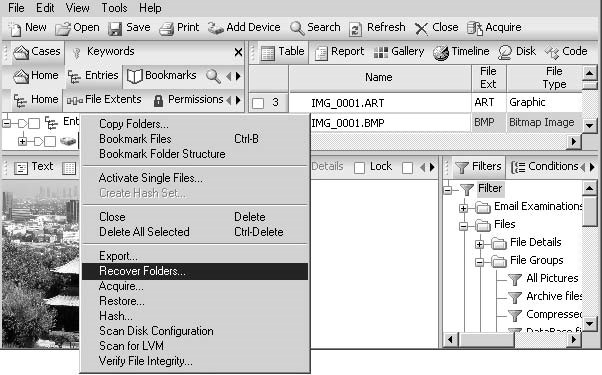
Figure 3-19EnCase allows an investigator to recover deleted files and folders.
Viewing Recovered Files
An investigator can select theRecovered Folderto view the deleted files and folders that have been recovered, as shown in Figure 3-21.
Recovering Files/Folders in an NTFS Partition
EnCase searches unallocated clusters in the master file table (MFT) to recover files and folders. It uses a similar recovery method with an NTFS partition as it does with a FAT partition.
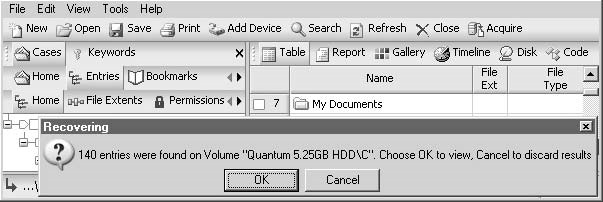
Figure 3-20An investigator can view the file and folder recovery results or discard them.
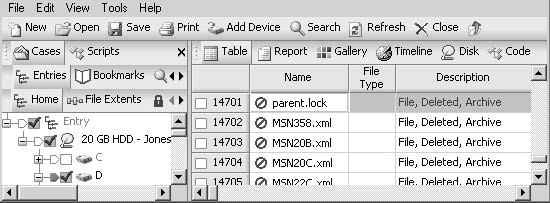
Figure 3-21TheRecovered Foldershows the files and folders that EnCase has recovered.
EnCase automatically rebuilds the structure of the formatted NTFS. It automatically searches the drive and finds artifacts from the previous partition. The partition information, directory structure, and folder structure are then automatically rebuilt. This capability is of critical importance in cases where a machine has been repurposed to another employee in the organization. If an individual who is the subject of an investigation used a repurposed machine, an investigator would need to recover the filesfrom the previous NTFS volume.
The folder recovery process can be slow and may take 60 minutes (1 hour) for 100-GB hard drives. The following are the steps to recover folders on an NTFS partition:
Right-click on the volume and selectRecover Folders.
ChooseOKto begin the search for NTFS folders.
Master Boot Record (MBR)
The master boot record (MBR) resides at the first sector (sector 0). The sector offset (SO) 446 contains the partition table.
The MBR allows four entries:
Each entry is 16 bytes long.
Partition entries range from LE 64 to 55 AA.
Master Boot Record (MBR)
The following are the steps for checking MBR entries:
Select sectors SO 446 to LE 64 (Figure 3-22).
Right-click and selectBookmark.
SelectWindowsand thenPartition Entry.
Enter a name for the bookmark.
NTFS Starting Point
Track 0 is normally considered the first 63 sectors of a disk and is reserved for the MBR. The MBR holds the partition table and the default Microsoft bootstrap code.
NTFS partitioning rules start the first primary partition in the 64th sector, as shown in Figure 3-23.
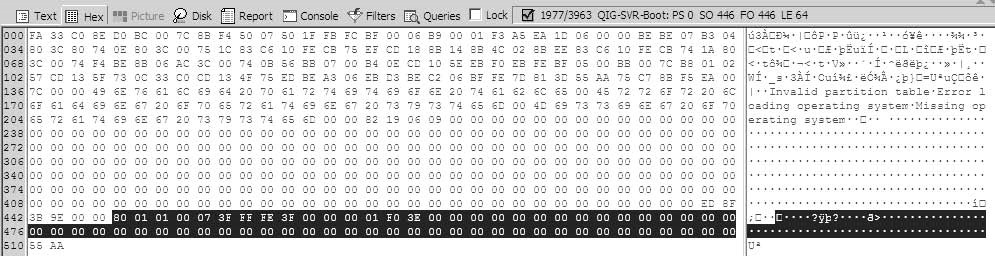
Figure 3-22An investigator can bookmark the master boot record.
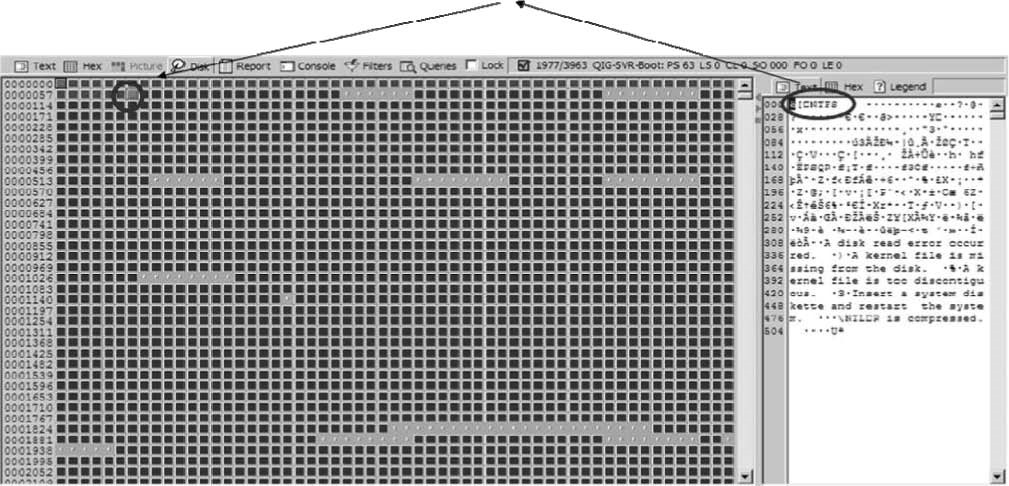
Figure 3-23The first primary partition on an NTFS disk starts in the 64th sector, immediately following the MBR.
Viewing Disk Geometry
An investigator can view disk geometry by highlighting the case and clickingReporton the top menu, as shown in Figure 3-24.
Recovering Deleted Partitions
There are two ways to check for deleted partitions:
Search for the followingin the unused disk area:
MSWIN4.1 (FAT partition)
NTFS (NTFS partition)
Look manually on the disk at the end of the first volume.
An investigator can recover the partition by right-clicking the area to recover and selectingAdd Partition, as shown in Figure 3-25. An investigator can delete a partition by right-clicking and selectingRemove user defined partitions.
Hash Values
Figure 3-26 shows a list of hash values for the files in a case.
Creating Hash Sets
An investigator can create ahash set by performing the following steps:
Select the files to be included in the hash set.
Right-click and chooseCreate Hash Set(Figure 3-27).
MD5 Hash
The MD5 hash is a 128-bit (16-byte) value that uniquely describes the contents of a file. It is a one-way hash function that converts a message into a fixed string of digits called message digests.
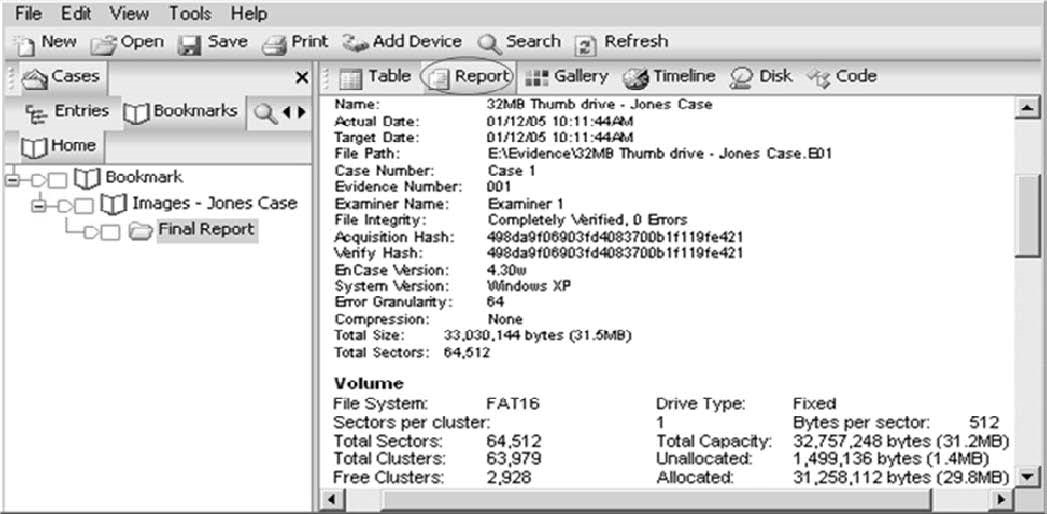


Figure 3-24TheReporttab shows the disk geometry of all devices in a case.
Hash Values
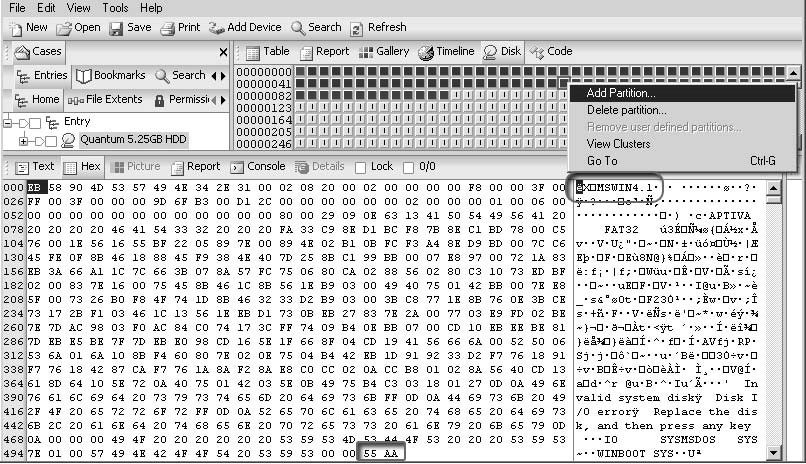
Figure 3-25An investigator can recover deleted FAT and NTFS partitions.
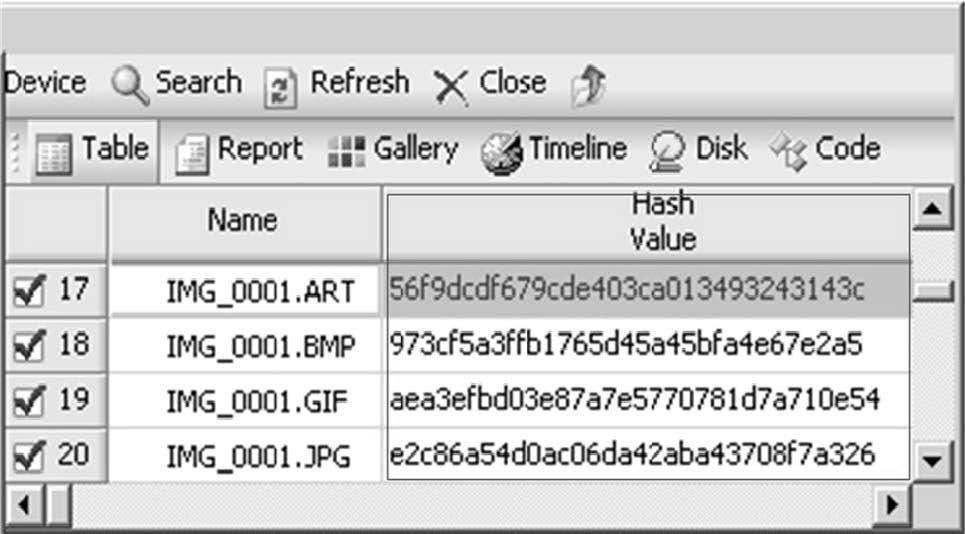
Figure 3-26EnCase hashes files to help in verifying file integrity.
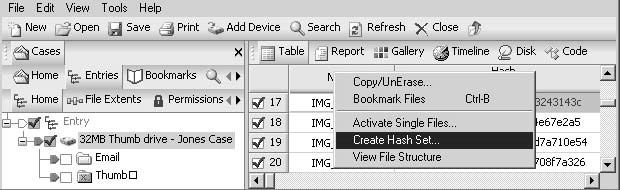
Figure 3-27Hash sets allow an investigator to organize hash values.
The purpose of the value within EnCase is to verify that the evidence file EnCase created is the same in byte structure as the original media. EnCase also uses MD5 hashing to create hash sets that are then added to the hash library. Hash sets are collections of hash files.
EnCase can create a hash value (digital fingerprint) for any file in the case.
The chance of two files having the same hash value is 2–128. The likelihood of duplication in MD5 is 340,282,366,920,938,463,463,374,607,431,768,211,456 to 1.
Creating Hashes
An investigator can clickSearchand selectCompute Hash Valueto create a hash for every allocated file. Figure 3-28 shows computed hash values for a set of files in the right column.
Viewers
EnCase allows an investigator to use externalviewers to view files. EnCase will copy a file to a temporary folder before launching the viewer to display the file. EnCase can use the following types of viewers:
External viewer: EnCase can be enhanced quickly to use external file viewers, easing the analysis of foreign file types, and allowing for the use of native applications from the source machine.
Registry viewer: The integrated registry viewer organizes the registry data file into folders, giving examiners an expedient and efficient way to viewthe Windows registry and determine values.
EnCase viewer: The fully integrated picture viewer automatically locates and displays many known graphical image types, including Microsoft thumbs.db files.
Timeline: This integrated viewer allows an examiner to see all relevant time attributes of all the files in the case (or selected group of files) in a powerful graphical environment.
An investigator can see the viewers by clickingViewersin theViewmenu. The investigator can create a new viewer just by entering the application path, as shown in Figure 3-29.
Signature Analysis
The ISO (International Organization for Standardization) and ITU (International Telecommunication Union) work to standardize types of electronic data. When a file type becomes standardized, a signature or header is stored along with the data. Applicationsuse the header to correctly parse the data. An investigator can view the file signature to identify the file type, even if its extension has been changed.
To perform signature analysis, an investigator can selectViewand thenFile Signatures.
Viewing theResults
Figure 3-30 shows the results of signature analysis.
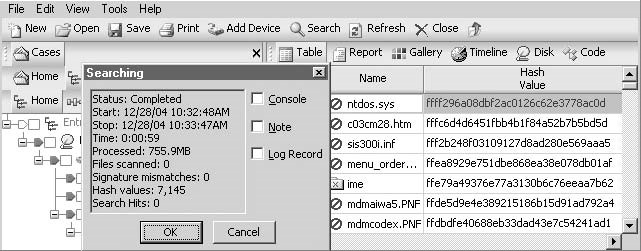
Figure 3-28An investigator can easily create hash values for every file in a case.
Reporting
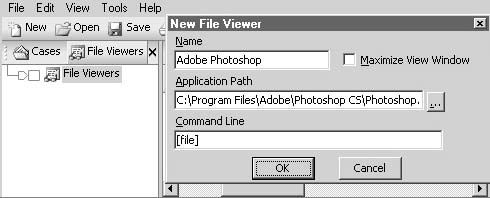
Figure 3-29An investigator can easily create a new type of external viewer.
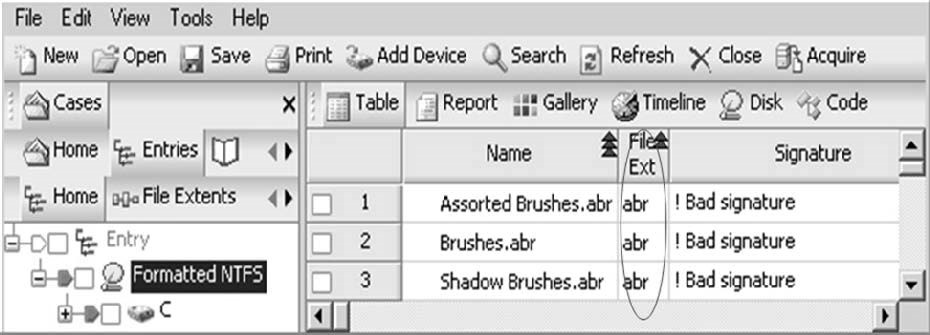
Figure 3-30EnCase displays the results of signature analysis once it has completed the task.
Copying Files and Folders
An investigator can select a group of files and folders to copy, as shown in Figure 3-31. The investigator can unerase the file if EnCase indicates that it has been deleted.
E-Mail Recovery
The default path for Outlook Express 5/6 in Windows XP is \Documents and Settings*Illegal HTML tag removed :* \Local Settings\Application Data\Identities\
Inbox.mbx
Outbox.mbx
Sent Items.mbx
Deleted Items.mbx
Drafts.mbx
An investigator can view these files in EnCase.
Reporting
The final stage of forensic analysis is reporting. A report must be easy to understand and cover in-depth information about the evidence. To create a report, an investigator can clickReportin theBookmarksmenu. Figure 3-32 shows a final report.
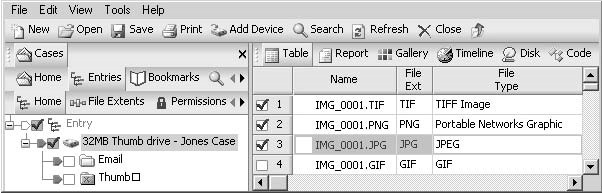
Figure 3-31An investigator can copy and unerase files and folders.
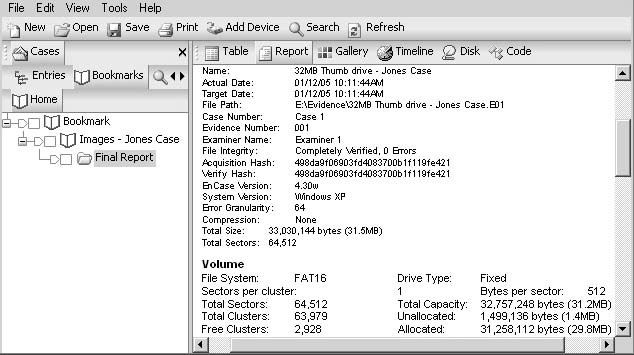
Figure 3-32The final report shows the analysis results for a case.
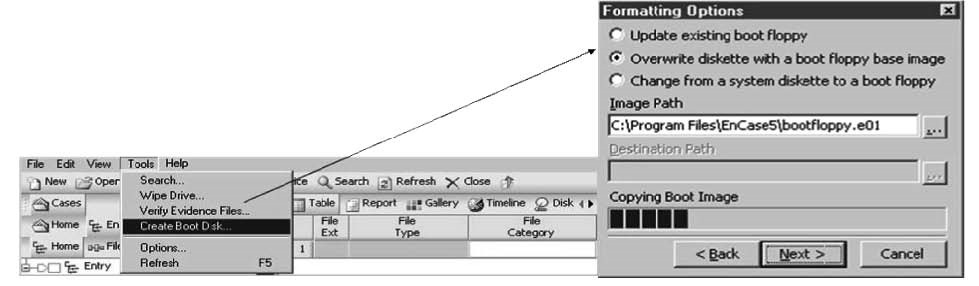
Figure 3-33An investigator can use an EnCase boot disk to create a bit-stream image of a device.
EnCase Boot Disks
An investigator can create a boot disk directly in EnCase. The investigator can use this boot disk to boot up in MS-DOS mode. By using this disk, he or she can create bit-stream images. Figure 3-33 shows EnCase creating a boot disk.
Review Questions
Chap**ter Summary**
■The evidence file is the core component in EnCase.
■Each evidence file is an exact sector-by-sector copy of a floppy or hard disk.
■EnCase calculates an MD5 hash when it acquires a physical drive or logical drive.
■EnCase provides powerfulsearching capabilities.
■EnCase allows an investigator to bookmark files, folders, or sections of a file for easy reference.
■EnCase searches unallocated clusters in the master file table (MFT) to recover files and folders.
■EnCase can create a hash value (digital fingerprint) for any file in a case.
Review Questions
- What is an evidence file, and what is it used for?
- Describe the main parts of an evidence file.
- Describe the steps involved in acquiring an image of a storage device.
- What does theDevicetab show?
- What is the purpose of an EnCase boot disk?
- Whatis the purpose of file-signature analysis?
- How does EnCase use MD5 hashing?
- Describe the kinds of searches an investigator can perform using EnCase.
Hands-On Projects
 Perform the following steps:
Perform the following steps:
■Install EnCase.
■Create a case file structure on the desktop:
Create a “MY CASES” folder to represent a pristine forensic hard drive.
Create a subfolder of MY CASES called “Case 1” to represent the case.
Create three subfolders of Case 1 called “evidence,” “temp,” and “export.”■Start Encase, and selectFileand thenNewfrom the menu.
TheCase Optionswindow for the new case opens. Set the options as follows:
Name: Case 1 (already identified)
Examiner Name:
Default Export Folder:
Temporary Folder:
- S electFileand thenSavefrom the menu. Name the case “Case 1” and save it in the MY CASES\Case 1 folder. You now have the structure necessary to support an entire forensic research project.
Perform the following steps:
■C reate a second case and name it “StudentDemo” (refer to the first hands-on project for
how to create a case if necessary).
■Copy all five evidence files from the Labs CD to StudentDemo/Evidence.
■S tart EnCase, selectFileandOpenfrom the menu, and navigate to the StudentDemo case file.
■W hen prompted, navigate to the correct path of your copied Quantum.E01 evidence file, and clickOpen.
■C orrect the location of support directories by selectingToolsand thenOptionsfrom the menu.
■I dentify your name, export directory, and temp directory, as in the first hands-on project.
■Save your case.
■You now have a snapshot of a complete forensic investigation underway.
3. Perform the following steps:
■Open the StudentDemo case. Note the three panes:
Left: Contains evidence file listings
Right: Contains folders and subfolders within the selected evidence file
Bottom: Contains the contents of the selected file structure
■In the left pane, expand (click “”) the C: drive within the Quantum evidence file.
■I n the left pane, highlight the My Documents folder by clicking on the folder name. Notice the itemized list of 22 files and subfolders in the right pane.
■C lick on the pentagon to the left of the My Documents folder name. Notice the itemized list has changed to 1,437 files and folders.
■H old the Ctrl key, and click on the pentagon to the left of the PhotoDlx folder. Notice
how additional files and folders have been added to the itemized list. Deselect PhotoDlx’s contents by clicking the pentagonagain.
Hands-On Projects
■H ighlight an image file in the right pane. Notice that images are interpreted and displayed in the bottom pane. Notice that icons at the top of the bottom pane change how file contents are displayed. Notice the text at the topright of the bottom pane identifies the exact position in the evidence file. The following are what the abbreviations here stand for:
PS: physical sector
LS: logical sector
CL: cluster number
SO: sector offset
FO: file offset
LE: file length in bytes
■P repare a list of words to search for by selectingViewand thenKeywordsfrom the menu. Notice the new view in the left and right panes. Use the following words:investigator,search warrant, andreports.
■Right-click onKeywordsin the left pane, and selectNew Folder.
■R ight-click onFolderand selectRename. Backspace and rename the folder “Search-
Words” and pressEnter.
■H ighlight SearchWords in the left pane, and right-click in the right pane to add a search word. Notice theNew Keywordwindow opens. Here are some things worth noting:
TheGREPcheck box indicates a phrase could be part of a word.
Active Code-Pageassists in identifying the language.
Unicodeturns on/off the Unicode interpreter.
Modifies the Unicode interpreter.
UTF8modifies the Unicode interpreter.
■A dd the wordsvictim,bomb,explosion,fire,gun, and_pain_with onlyActive Code-Pagechecked. ClickOKto close theNew Keywordwindow.
■Click on theSearchicon in the top toolbar.
Check the box next toSelectedFile Only, and clickStart.
Notice the flashing status at the bottom right of the screen showing the estimated time to completion.
Notice the search cannot be interrupted once started.
Notice that multiple searches can be started at one time.
Notice the summary screen display upon completion of the search.
■V iew search results when the search is complete by selectingViewand thenSearch Hits
from the menu. Click on individual search terms in the left pane, and view contextual hits in the right pane.
■Highlight the word_bomb_in the left pane.
■Locate search result #702 in the right pane.
Choose to review the contents as text in the bottom pane.
SelectViewand thenText Stylesfrom the menu.
HighlightLow Bit - ASCIIin the left pane.
HighlightASCII@80in the right pane.
■Bookmark this evidence for later reference.
ChooseViewand then Bookmarks from the menu.
Right-click onStudentDemoin the left pane, and selectNew Folder.
Right click onFolder 1to rename it to Quantum.E01.
Click and drag in the bottom pane to select text of interest (a few paragraphs).
Right-click the selected text and selectBookmark Data.
Create a comment by which to recognize this text.
Identify the destination folder as Quantum.E01 and clickOK.
Perform thefollowing steps:
■Open the StudentDemo case. Expand the Quantum bit image file.
■Highlight the C: drive in the left pane.
■P lace a check mark next toUnallocated Clustersin the right pane. Note how the check
marks echo back to the left pane’s identifiers.
■SelectViewand thenKeywordsfrom the menu.
■A s before, right-click onKeywordsin the left pane and create a new folder. Backspace, and rename the folder “File Headers.”
■Copy a current definition for JPEG headers from the Signatures database to your folder:
SelectViewand thenFile Signaturesfrom the menu.
Scroll down on the right pane just past halfway to locate theJPEG Imageentry.
Right-click on this entry, and selectEdit.
T heSearch Expressiondata field (containing \xFF\xD8\xFF[\xFE\xE0]\x00) is
highlighted.
Press Ctrl+C to copy the highlighted text.
Click theCancelbutton to close the JPEG definition window.
C lick on theKeywordstab at the top of the left pane to return to theKeywordswindow.
Right-click on your new folder, File Headers, and selectNew.
With the cursor in theSearch Expressionfield of theNew Keywordwindow, press
Ctrl+V to paste the text you copied from thesignatures database.
Add a descriptive title like “JPEG” to theNamefield, and check theGrepcheck box.
ClickOKto save and close theNew Keywordwindow.
Check the check box to the left of your new keyword.
■Perform the search:
Click theSearchiconin the toolbar.
C heck the check box to the left ofSelected Files Onlyto limit the search to unallocated space.
E nsureSearch each file for keywords,Search file slack, andSelected keywords onlyare checked.
C lear checks fromVerify file signatures,Compute hash value, andSearch only slack
area of files in Hash Library.
Click theStartbutton to begin the search.
At completion of the search, a status screen opens.
Hands-On Projects
■View the search results:
SelectViewand thenSearch Hitsfromthe menu.
Highlight the JPEG search string in the left pane. View the results in the right and
bott om panes.
Check the check box to the left of the JPEG keyword in the left pane.
Scroll to the last column in the right pane, titledPictures.
Right-clickinside this column and selectPicture-Invert Selected Items. Note that images are now viewable in the bottom frame.
■Save and close the EnCase application.
- Perform the following steps:
■Open the StudentDemo case.
■Right-click on theQIG-SVR-Bootfile entry and selectScan RAID configuration.
N ote: Upon completion, a new entry is created in the left pane, indicating a composite virtual drive.
N ote: The composite virtual drive is identified by the last volume drive letter assigned
toit.
- Note: The drive is ready for forensic analysis.
Objectives
After completing this chapter, you should be able to:
Delete files
Understand what happens when a file is deleted
Understand the Recycle Bin
Perform data recovery in Linux
Know and understand data recovery tools
Delete partitions
Recover deleted partitions
Know and understand partition recovery tools
Key Terms

Recove**ringDeletedFiles**
and**Deleted**Partitions
Chapter
4
Recycle Bina space on a disk for files and folders that are marked for deletion
Recycled foldera folder on each drive to which files deleted by compliant programs are moved
SID (security identifier)a unique name assigned by a Windows domain controller to identify a specific computer on a network
Undeleteto restore the content in files that have been deleted deliberately or accidentally from a disk
4-1
Case Example
William Hickey, a 44-year-old Mingus Union High School teacher, was suspected of downloading child pornography onto the school’s computer, but no charges were filed against him.
Though Hickey had tendered his resignation, he was allowed to work from homeuntil his resignation went into effect on December 22, 2006. Police seized the computer and sent it to the Department of Public Safety. There, police investigated whether it contained images of child pornography. They did locate some pornographic images but have not identified any potential victims. It was reported, however, that the forensic investigation could take weeks, or even months, to conduct tests.
Upon the receipt of the lab reports, the district attorney will decide whether charges should be filed.
Introduction to Recovering Deleted Files and Deleted Partitions
This chapter focuses on recovering deleted files and deleted partitions. It begins bycovering deleting files and the Recycle Bin. It then moves on to the subject of file recovery, including file recovery in Linux and the file recovery tools that forensic investigators use. The chapter then discusses deleting and recovering partitions. It finishes with an overview of partition recovery tools.
Deleting Files
There are different ways to delete files, depending on the file system and operating system a computer is using. On a Windows system, most deleted files are sent to the Recycle Bin. TheRecycle Binis a space on a disk for files and folders that are marked for deletion. The following steps show one way to delete files by moving them to the Recycle Bin:
Right-click on the file or folder you want to remove, and choose theDeleteoption inthe context menu (Figure 4-1).
Windows will confirm that you wish to send the file to the Recycle Bin. Click onYesto delete the file (Figure 4-2).
Copyright © by

All rights reserved. Reproduction is strictly prohibited
Figure 4-1This is a context menu that shows how to delete files from a Windows machine.
Figure 4-2This is the dialog box that will pop up when you are about to delete a file. ChooseYesif you are sure you want to delete the file.

Figure 4-3This image shows dragging and dropping files into the Recycle Bin.
There are other options for deleting files on a Windows computer:
Select the file or folder you want to delete, and press the Delete key on the keyboard.
Select the file or folder you want to delete. Go to the taskbar optionFileand clickDelete.
Drag and drop files into the Recycle Bin (Figure 4-3).
What Happens When a File Is Deleted in Windows?
When a user deletes a file, the operating system does not actually erase the file. It marks the file name in the master file table (MFT) with a special character that tells the processor that the file has been deleted.
The operating system replaces the first letter of a deleted file name with a hex byte code: E5h. E5h is a special tag that indicates that the file has been deleted. The corresponding cluster of that file in FAT is marked as unused, though it will continue to contain the information until it is overwritten.
The Recycle Bin in Windows
The Recycle Bin is located on the Windows desktop. When a user deletes an item from the hard disk, the Recycle Bin icon changes from empty to full. However, this item has not actually been erased. It is tagged as information to be deleted. When the user empties the Recycle Bin, he or she is telling the computer that the space those files used is now free to store new information.
Items deleted from removable media, such as a flash memory card or network drive, are not actually stored in the Recycle Bin. When a user ejects the removable media, he or she will no longer be able to access the files he or she deleted or moved to the Recycle Bin. The items present in the Recycle Bin still take up dedicated, adjustable space on the hard disk. These items can be restored to their original positions with the help of theRestore all itemsoption of the Recycle Bin. After being deleted from the Recycle Bin, these items still take up space in the hard disk until the operating system overwrites the location where the information is stored.
When the Recycle Bin becomes full, Windows automatically deletes the older items. Because the Recycle Bin takes up a specific space on each partition of the hard disk, very large items are not stored in the Recycle Bin. They are deleted permanently.
A user can manipulate the Recycle Bin in a number of ways. The following steps show how to change the storage capacity of the Recycle Bin:
Right-click onRecycle Binand chooseProperties.
Increase ordecrease the storage capacity by moving the bar.
The following steps show how to restore files in the Recycle Bin:
Open Recycle Bin.
Right-click the item to restore. Then chooseRestore.
It is possible to select more than one item to restore. Select the items to restore, and chooseRestore All(Figure 4-4).
The following steps show how to delete files in the Recycle Bin:
Open Recycle Bin.
Right-click the file to delete, and chooseDelete.
Storage Location of Recycle Bin in FAT and NTFS
On a FAT drive, deleted files are stored in the locationC:\RECYCLED; on an NTFS drive, files are stored in theC:\RECYCLERfolder.
The Recycle Bin folders in FAT and NTFS have two different names to avoid confusion, in case a computer system has both file systems, or a file system is converted to another file system, as when FAT is converted to NTFS.
FAT and NTFS Recycle Bins have different internal structures. All recycled files in the FAT system are dumpedinto a singleC:\RECYCLEDdirectory, while recycled files on the NTFS system are categorized into directories named asC:*RECYCLER\S- . . . .,based on the user’s Windowssecurity identifier**(SID)*. Figure 4-5 shows a command shell viewing one of these directories.
Figure 4-4This image shows the Restore All feature of the Recycle Bin.
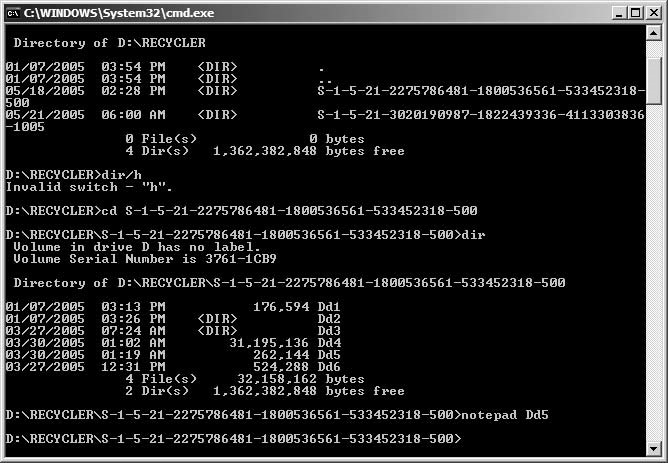
Figure 4-5This shows the locations of the Recycler directory in NTFS. The security identifier is S-1-5-21-2275786481-18000536561-533452318-500.
By default, Windows reserves 10% of the hard drive space for the Recycle Bin. The maximum possible capacity for any drive over 40 GB is 3.99 GB per drive. Items that exceed the capacity of the Recycle Bin are deleted immediately.
How the Recycle Bin Works
Each hard disk has a hidden folder namedRecycled. This folder contains the files deleted from Windows Explorer or My Computer.
Deleted files are stored in theRecycled folder. Each deleted file in the folder is renamed. A hidden file called INFO2 holds the original names and paths. This information is used to restore the deleted files to their original locations. The syntax for renaming is the following:Dxy.ext.
All recycled files begin with the letterD;Ddenotes that a file has been deleted.
The secondletter (x) is the letter of the drive where the file is located. If the file resides on the main hard drive, it will be the letterC. If it is on the floppy drive, it will be the letterA.
The final piece (y) denotes a sequential number starting from 0.
The file will keep the same extension as the original file, such as .doc or .pdf.
Consider the following example:
New file name:Dc1.txt (C drive, second file deleted, a .txt file)
INFO2 file path: C:\Windows\Desktop\Forensics.txt
New file name: De7.doc(E drive, eighth file deleted, a .doc file)
INFO2 file path: E:\Homework\James Joyce Essay.doc
Damaged or Deleted INFO2 File
Once the INFO2 file is damaged or deleted, it will not appear in the Recycle Bin, but the deleted renamed files will still be present in the Recycled folder. Because the files were renamed in the Recycled folder, but not changed, they can be searched and restored by locating the file based on the new naming convention and renaming the file.
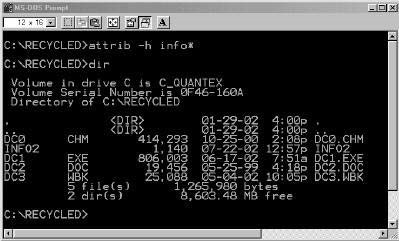
Source:http://www.geekgirls.com/windows_recycle_bin.htm.Accessed 2/2007.
Figure 4-6This shows the location of the INFO2 file in the Recycled directory in a FAT file system. The other four files in that directory are files that have been deleted.
When the INFO2 file is deleted, it will be re-created when a user restarts Windows. If the Recycle Bin is damaged and not working, the user must delete the hidden INFO2 file from the Recycled folder and restart Windows to re-create the INFO2 file; this will enable the user to access the deleted files in the Recycle Bin. A user can also delete the INFO2 file from a command prompt window:
cd recycled
attrib -h inf*
del info
Figure 4-6 shows the location of the INFO2 file in a FAT file system.
Damaged Files in the Recycled Folder
Damaged or deleted files will not appear in the Recycle Bin. In such cases, follow the steps below to recover the deleted files:
Make a copy of theR**ecycled\Desktop.ini**file in a separate folder, and delete all the contents from the Recycled folder.
Delete all files in the Recycle Bin.
Restore the Desktop.ini file to the Recycled folder.
If there is no Desktop.ini file or if it is damaged, re-create itby adding the following information to a new Desktop.ini file:
[.ShellClassInfo]
CLSID={645FF040-5081-101B-9F08-00AA002F954E}
Damaged Recycled Folder
At times, the Recycled folder itself can be damaged. In this case, a user will still be able to send files to the Recycled folder, even though the Recycle Bin on the desktop appears full. The user will not be able to view the contents of the Recycle Bin, and theEmpty Recycle Bincommand will also be unavailable. Figure 4-7 shows a damaged Recycle Bin.
To fix this, a user needs to delete the Recycled folder and restart Windows; Windows will regenerate the folder and restore its functionality.
Figure 4-7This shows a corrupted or damaged Recycle Bin. The bin appears full, but in the context menu, the optionEmpty Recycle Binis grayed out.
The Recycled folder can also be generated from the command prompt:
| Right-click any empty space on the Windows desktop. |
|---|

Creating**aNewDesktop.iniFilein**Windows
attrib -s -h recycled
del recycled
Close the command window and restart the computer.
How to Undelete a File
If a file has been deleted from the Recycle Bin, in order to fully or partially restore it, a user will have toundeletethe file. The process of file undeletion involves locating the data on the disk partitions and allowing the operating system to access the file. There are two main ways of carrying this out:
Modify the existing file system to remove the “deleted” flag fromthe file to restore it.
Locate the data in the partition, and copy it to a new file.
Data Recovery in Linux
The main advantage that Linux has over Windows is its ability to access and recover data from otherwise problematic machines. All file systems are supported in a standard stock kernel, which should have the ability to support older file systems. Therefore,the Linux kernel supports a large number of file systems, including VxFS, UFS, HFS, and the aforementioned NTFS and FAT systems. Note that Mac OS X is based on OpenBSD and thus uses the same UNIX/Linux kernel.
Individuals can, in some cases, dual-boot Linux and Windows; this can be done by using FAT and NTFS. Data of machines that fail to boot in a Windows environment can easily be recovered using bootable Linux, such as Knoppix.
In Linux, files that are deleted using the command/bin/rmremain on the disk. If a running process keeps a file open and then removes the file, the file contents are still on the disk, and other programs will not reclaim the space. The second extended file system (ext2) is commonly used in most Linux systems. The design of the ext2 file system is such that it shows several places where data can be hidden.
It is worthwhile to note that if an executable erases itself, its contents can be retrieved from a /proc memory image. The commandcp /proc/$PID/exe/tmp/filecreates a copy of a file in /tmp.
Tools to Recover Deleted Files
Tables 4-1, 4-2, 4-3, and 4-4 show a sample of some tools investigators use to recover deleted files:
| Active@ UNDELETE | Fundelete | Restorer2000 |
|---|---|---|
| Active@ UNERASER | Handy Recovery | Search and Recover |
| BadCopy Pro | Mycroft V3 | SUPERFileRecover |
| DiskInternals Uneraser | O&O Unerase | Undelete |
| eData Unerase | PC Inspector File Recovery | VirtualLab |
| Easy-Undelete | PC Inspector Smart Recovery | WinUndelete |
| File Recover | R-Undelete | Zero Assumption Recovery |
| File Scavenger | Recover My Files | |
| File-Saver | Recover4all Professional |
Table 4-1This table lists file recovery tools for Windows
| e2undel | R-Linux | Stellar Phoenix |
|---|---|---|
Table 4-2This table lists file recovery tools for UNIX-based operating systems
| eIMAGE Recovery (image and media files) | Repair My Excel (Microsoft Excel files) |
|---|---|
| ImageRecall (image files) | RecoverPlus Pro (image files) |
| OfficeFIX (Microsoft Office files) | Zip Repair Pro (compressed files) |
| Word Repair (Microsoft Word Files) |
Table 4-3This table lists file recovery tools based on file type
| CD Data Rescue (CDs and DVDs) | eIMAGE Recovery |
|---|---|
| CDRoller (CDs and DVDs) | inDisc Recovery (CDs and DVDs) |
| DiskInternals Flash Recovery (flash drives) | IsoBuster (CDs and DVDs) |
| DiskInternals CD and DVD Recovery (CDs and DVDs) |
Table 4-4This table lists file recovery tools based on media type
File Recovery Tools for Windows
Tool: Active@ UNDELETE
Active@ UNDELETE is a powerful data recovery software that helps a user recover lost, deleted, and formatted data from hard drives, floppy disks, basic and dynamic volumes, hardware or software RAID (RAID0 and RAID5). It supports compressed, encrypted, andfragmented files. Besides hard disk drives and floppies, the program supports recovery from removable devices such as Secure Digital, CompactFlash, SmartMedia, Sony Memory Stick, Zip drives, and USB hard drives.
Active@ UNDELETE will help users restore data residing on hard drives formatted in FAT12, FAT16, FAT32, NTFS, NTFS5, NTFS, and EFS file systems, and it works under all Windows family operating systems: Windows 95/98/ME/NT/2000/2003 server and Windows XP. Active@ UNDELETE incorporates many wizards that provide expert users full control over the process of data restoration. The following are some of the features of Active@ UNDELETE:
Recovers files on IDE/ATA/SATA/SCSI hard disk drives
Recovers files on removable devices (SmartMedia, Secure Digital, Memory Stick, etc.)
Supports external Zip drives and USB hard drives
Recovers files from deleted, damaged, formatted, or reformatted partitions
| Operating Systems:Windows XP/98/ME/NT 4.0/2000/2003 serverFile Types:All |
|---|
Supports FAT12, FAT16, FAT32, NTFS, NTFS5, NTFS, and EFS file systems
Supports recovery of compressed, fragmented, and encrypted files on NTFS
Advanced search by file name, file date, mask, size range, and attributes
Two types of drive and device scan: Basic (fast) and Thorough (slow)
Ability to create and work with raw and compressed disk images representing the whole drive in one file
Ability to connect to remote machines and scan, create disk images, and recover data remotely
Supports hardware and software RAID
Figure 4-8 shows a screenshot from Active@ UNDELETE.Tool: Active@ UNERASER
Operating Systems:DOS and Windows
File Types:All
Media:Hard drives and floppy disks
Web Site:http://www.uneraser.com/
Cost:$49.99
Active@ UNERASER is powerful hard drive recovery software for DOS and Windows (Console) that can recover deleted files and folders on FAT12, FAT16, FAT32, and NTFS file systems. It can even restore files from deleted and reformatted partitions.
With this data recovery software, NTFS drives can be recognized and deleted items can be recovered while working from the DOS and Windows (Console) environment. It is not necessary to install the utility on a hard drive, as it fits on a bootable floppy disk,removing the possibility of overwriting the data a user wants to recover.
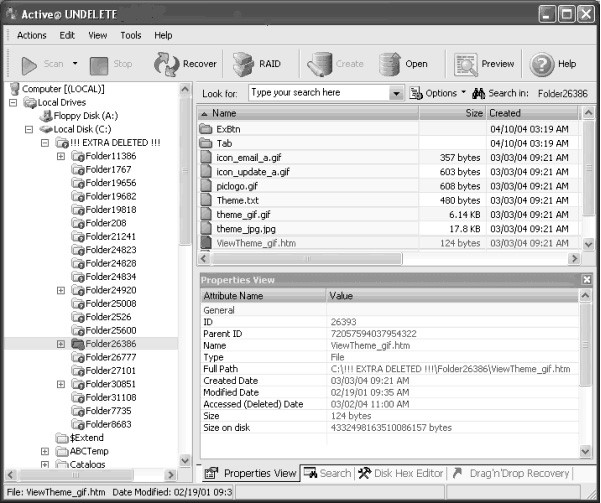
Source:http://www.active-undelete.com/.Accessed 2/2007.
Figure 4-8This figure shows the Active@ UNDELETE application screen.
The following are some of the features of Active@ UNERASER:
Recovers lost data on all DOS/Windows systems, whether FAT or NTFS partitions
Undeletes compressed, fragmented, sparse, and encrypted files on NTFS
Recovers deleted files with long or non-English file names
Unformats (i.e., recovers) files from formatted hard drives
Creates and works with raw and compressed drive images for backup purposes
Unerases files from deleted and damaged partitions and logicaldrives
Scans hard drives and displays deleted FAT and NTFS partitions and/or logical drives
Views files and any sector contents in hex/text viewer
Supports LBA mode for access to large hard drives
Two types of drive and device scan: Basic (fast) and Thorough (slow)
Full support for long and localized file names for display and recovery
Extended file and drive attributes support for information display
Encrypting File System (EFS) support in Windows (Console) application
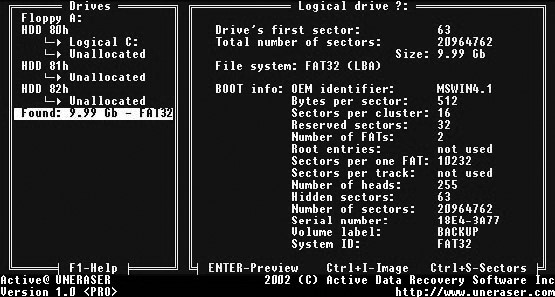
_Source:_www.uneraser.com (Active Data Recovery Software). Accessed 2/2007.
Figure 4-9This figure shows the Active@ UNERASER application recovering files from a hard drive. Notice that the application found 9.99 GB of data to recover.
_Source:_www.uneraser.com (Active Data Recovery Software). Accessed 2/2007.
Figure 4-10This image shows the recovery success for each of the sectors on the disk.
Advanced searching: by mask, size, attribute, deleted/existing only
Advanced disk imaging: raw and compressed disk images, composing disk images from raw chunks (created by other tools), and checking disk image consistency
Read and copy existing files from NTFS to FAT partition
Figures 4-9 and 4-10 show screenshots from Active@ UNERASER.
Source:http://www.jufsoft.com/badcopy/.Accessed 2/2007.
Figure 4-11This screenshot shows BadCopy Pro.
Tool: BadCopy Pro
Operating**Systems:**
Windows
File**Types:**
All
Media:
Harddrivesandremovablemedia
Web**Site:**
Cost:
$39.50
BadCopy Pro is an application that helps in recovering corrupted or lost data fully from floppy disk, CD, CD-R, CD-RW, digital media, and Zip drives or disks. This tool also supports all kinds of damage situations for any file types. The software does notwrite data to the original disk; however, it saves the recovered information to a new folder that the user specifies. BadCopy Pro also helps in the retrieval of data from all sessions on multisession CDs. This application is powerful in recovering deletedfiles from other removable storage hardware. Figure 4-11 shows a screenshot from BadCopy Pro.
Tool: DiskInternals Uneraser
Operating Systems:Windows
File Types:All
Media:Hard drives and removable media
Web Site:http://www.diskinternals.com/
Cost:$39.95
DiskInternals Uneraser can recover any deleted file, including documents, photos, mp3s, and Zip files, or even folders and damaged disks. In addition to HDD, the program supports any type of storage media (music sticks, cameras, flash drives, USB drives, etc). It works with encrypted files and helps undelete files lost because of a virus attack, or an employee’s malicious behavior.
Source:http://www.diskinternals.com/.Accessed 2/2007.
Figure 4-11aThis screenshot shows DiskInternals Uneraser.
The following are some of the features of DiskInternals Uneraser:
Standard Windows Explorer interface, drag-and-drop support.
Works under Microsoft Windows 95, 98, ME, NT, 2000, XP, 2003 Server.
Supported file systems: FAT12, FAT16, FAT32, NTFS (NT 4), NTFS5 (2000, XP).
Supports hidden file systems: Hidden FAT12, Hidden FAT16, Hidden FAT32, and Hidden NTFS.
Recovers compressed files (NTFS, NTFS5) and encrypted files (NTFS5).
Ignores file access rights (NTFS).
Recognizes localized names.
Long file names support (FAT12, FAT16, and FAT32).
Figure 4-11a shows a screenshot from DiskInternals Uneraser.
Tool: eData Unerase
Operating Systems:Windows ME/NT/2000/XP/2003
File Types:All
Media:Hard drives and removable media
Web Site:http://www.octanesoft.com/data_recovery.htmlCost:$32.00 (for professional version)
eData Unerase recovers deleted files, files emptied from the Recycle Bin, and files lost due to the format of a hard drive, virus infection, unexpected system shutdown, or software failure. Simply use eData Unerase to perform hard drive data recovery, or recover deleted files from floppy disks, Zip drives, CompactFlash cards, SmartMedia cards, or other removable media types.
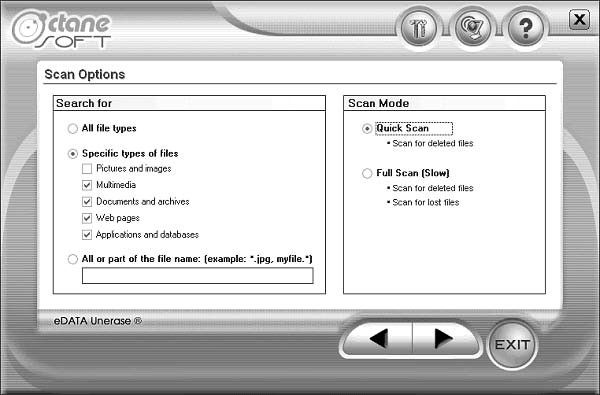
Source:http://www.octanesoft.com/data_recovery.html.Accessed 2/2007.
Figure 4-12This image shows eData Unerase. Notice that you can choose specific file types, and you have a choice of a quick scan or full scan.
It combines two methods to recover a user’s files: Quick Scan (scan for deleted files) and Full Scan (scan for deleted and lost files). It also incorporates a search-specific facility, making file recovery easier and more effective. The following are some of the features of eData Unerase:
Recovers files from FAT12/16/32 and NTFS hard drives, Memory Sticks, USB flash drives, memory cards, removable media, and more
Recovers files that have been removed or emptied from the Recycle Bin or lost due to a power failure or virus attack
Operating**Systems:**
WindowsXP,2000,2003,andNT(canalsorecoverfromdriveswithLinuxpartitions)
File**Types:**
All
Media:
Harddrivesandremovablemedia
Web**Site:**
http://www.easy-undelete.com/index.h
Cost:
$23.00
Full Scan (cluster scan) works on healthy and corrupted hard drives
Easily scans for group of file types, and the deleted file list includes filters for sortingFigure 4-12 shows a screenshot from eData Unerase.
Tool: Easy-Undelete
Easy-Undelete is a powerful and user-friendly data recovery and undelete solution for Windows. It can recover lost files and folders on NTFS and FAT volumes, or on any physical storage device, and can preview images and binary files before recovery.
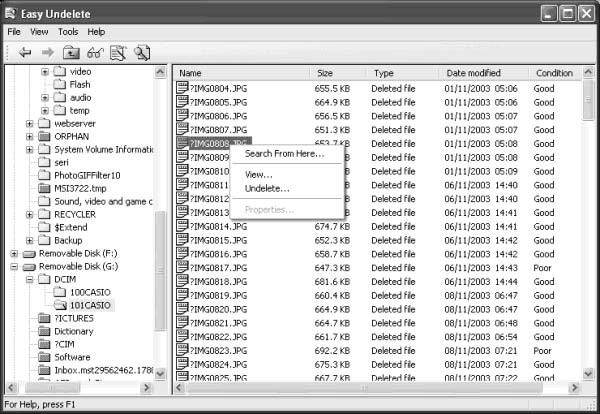
Sour__ce:http://www.easy-undelete.com/index.html.Accessed 2/2007.
Figure 4-13This image shows files that have been recovered using Easy-Undelete.
The following are some of the features of Easy-Undelete:
Recovers lost or accidentally deleted files on any physical storage device, including memory cards, Disk-On-Key drives (thumb drives), Zip disks, reformatted volumes, repartitioned volumes, and drives with non-Windows partitions, such as Linux or OS X partitions
Deleted file and folder recovery from NTFS, FAT32, FAT16, and FAT12 volumes
Runs on any version of Windows, and under Windows XP, 2000, 2003, and NT, Easy-Undelete 3.0 is based on a Unicode (a set of more than 100,000 coded characters that represent text-based systems in various languages) core and can scan and recover files with file names in any language
Uses multiple scanning algorithms to make sure users have the best chances of finding the files or folders they lost
Can preview JPEG, PNG, TIFF, GIF, BMP, ICO, TGA, PCX, WBMP, and PNM graphics files, without having to recover them first
Can preview any other kind of file, in a hexadecimal view
Can be used by advanced users to recover specific clusters; when certain clusters have been lost, Easy-Undelete can preview the contents of the remaining clusters
Runs without installation
Figure 4-13 shows a screenshot from Easy-Undelete.Tool: File Recover
Operating Systems:Windows 2000/XP/Vista
File Types:All
Media:Hard drives
Web Site:http://www.pctools.com/file-recover/
Cost:$39.90
File Recover allows a user to recover documents and files that have been lost by accidental deletion. These files may be lost by the emptying of the Recycle Bin, or by using other deletion actions that bypass the Recycle Bin altogether. Such actions include Windows SHIFT+DELETE, command line deletion, deleting excessively large files, or using applications that delete files without the Recycle Bin.
File Recover identifies the contents of such lost files on the hard drive, and allows the user to recover them. If a file has been partially overwritten, File Recover attempts to reconstruct as much of the file as possible, with the remaining contents. This allows the user to salvage at least part, if not all, of that recovered file to continue using it as required.
It supports hard disks for FAT12/16/32 and NTFS file systems and will recover files on logical and physical hard disks. The programs also support batch file recovery. The following are some of the features of File Recover:
Recovers files instantly from hard drives, floppy drives, and other types of fixed media; if the user is a home user or a network administrator, File Recover fills a critical gap in his or her data protection strategy.
Rapid scan engine; a typical hard drive can be scanned for recoverable files within minutes.
Scans all files and directories on selected hard drives
Searches for a recoverable file by using part, or all, of its file name
Utilizes a nondestructive, read-only file recovery approach; File Recover will not write or make changes to the section of the drive from which it is recovering data.
Batch file recovery (recovers multiple files in one action)
Works around bad-sector diskareas and recovers data where other programs fail
Supports standard IDE/ATA/SCSI hard drives, including drives larger than 8 GB• Supports hard drives formatted with Windows FAT16, FAT32, and NTFS file systems Figure 4-14 shows a screenshot from File Recover.
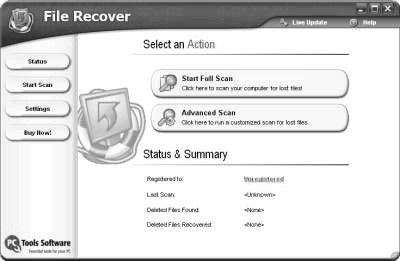
Source:http://www.pctools.com/file-recover/.Accessed 2/2007.
Figure 4-14This image shows the opening screen of the File Recover application.
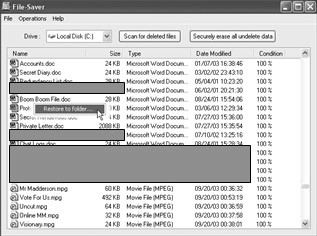
Source:http://www.file-saver.com.Accessed 2/2007.
Figure 4-15This image shows files that can be recovered using the File-Saver application.
Tool: File-Saver
Operating Systems:Windows 95/98/NT/2000/ME/XP/.NET Server
File Types:All
Media:Hard drives and removable media
Web Site:http://www.file-saver.com
Cost:Approximately $34.95
The File-Saver application restores hundreds of files that have been deleted from Windows machines whether they were deleted by another program, or emptied from the Recycle Bin. If it has been deleted, File-Saver can undelete it.
The tool can check whetheror not the data lost can be recovered successfully. This function is helpful for users as they can be ensured of the data that is lost permanently.
This tool supports unlimited file recovery. Additionally, all undelete information related to the system can be erased with the help of this tool. Repeatedly overwriting the reusable areas of the deleted files by random data achieves this.
Figure 4-15 shows a screenshot from File-Saver.Tool: File Scavenger
Operating Systems:Windows NT/2000/XP
File Types:All
Media:Hard drives and removable media
Web Site:http://www.quetek.com/prod02.htm/
Cost:$49.00
File Scavenger is a Windows NT/2000/XP file undelete utility that can recover accidentally deleted files. This includes files that have been removed from the Recycle Bin, DOS shell, network drives, or Windows Explorer. This tool supports file compression, dynamic disks, alternate data streams, sparse files, and so on.
The File Scavenger application supports both basic and dynamic disks. The File Scavenger application can recover files that have been reformatted or are in corrupted volumes by using the Defunct Volume Search, which can scan the entire drive to find traces of defunct or stripped volumes. File Scavenger is equipped with advanced algorithms to transparently handle disks that have many bad sectors or badly corrupted partitions. The software can be installed on a hard drive or run from a floppy disk.
File Scavenger version 3 can recover files that havebeen accidentally deleted (including files removed from the Recycle Bin, in a DOS window, from a network drive, or from Windows Explorer with the Shift key held down), provided that recovery is attempted before the files are permanently overwritten by newdata. File Scavenger supports: basic and dynamic disks, NTFS compression, alternate data streams, and sparse files.
File Scavenger can also recover files from a reformatted or corrupted volume. This is even possible when the volume has been deleted, and its original position and size are unknown. This tool can scan an entire physical hard drive to look for traces of defunct volumes. File Scavenger uses advanced algorithms to transparently handle disks with many bad sectors and badly corrupted partitions. The software can be installed on a hard drive, or run from a portable storage device such as a Memory Stick, removable drive, CD, or floppy disk. To run File Scavenger, a user must log on as a system administrator to the computer where data recovery is intended.
Figure 4-16 shows a screenshot from File Scavenger.
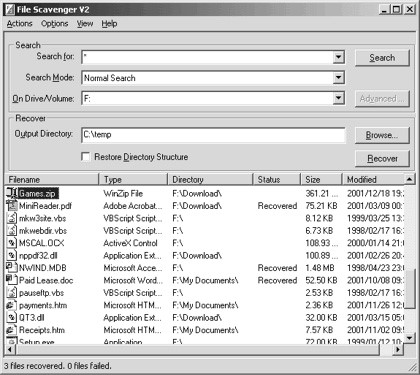
Source:http://www.quetek.com/prod02.htm/.Accessed 2/2007.
Figure 4-16This image shows files that have been recovered by File Scavenger.
Source:http://www.sysinternals.com/Utilities/Fundelete.html.Accessed 2/2007.
Figure 4-17This image shows files that can be undeleted from the C: drive by the Fundelete application.
Tool: Fundelete
Operating Systems:Windows ME/2000/XP
File Types:All
Media:Hard drives
Web Site:http://www.sysinternals.com/Utilities/Fundelete.html
| Operating Systems:Windows 9x/ME/NT/2000/XP/2003/Vista |
|---|
Cost:Free
The Fundelete tool works just like the Recycle Bin in standard Windows. In NT 4.0, the Recycle Bin stores only those files that are deleted from the Explorer GUI, and files deleted from command window, or from other programs deleted permanently. Fundeleteworks as the Recycle Bin in Windows, and stores all the files deleted from any program so that it is easy to restore them. It has the same configuration as the Recycle Bin. Fundelete also has filtering ability so that it does not send certain designated files, based on the file extension, to the Recycle Bin. Files such as editor backup files, and temporary files can be filtered out and directly deleted. Fundelete notes and can recover those files that are deleted after the application’s installation. Figure 4-17 shows a screenshot from Fundelete.
Tool: Handy Recovery
Source:http://www.handyrecovery.com/.Accessed 2/2007.
Figure 4-18This image shows the Handy Recovery tool. Notice how you can set the tool to search for partitions as well as single files.
Handy Recovery is designed to restore files accidentally deleted from hard disks and floppy drives. The program can recover files damaged by virus attacks, power failures, and software faults, or files from deleted and formatted partitions. If some programs do not use the Recycle Bin when deleting files, Handy Recovery can restore such files. It can also recover files moved to RecycleBin after the Recycle Bin has been emptied.
Operating**Systems:**
WindowsXP
File**Types:**
All
Media:
Harddrivesandremovablemedia
Web**Site:**
Cost:
$165
With Handy Recovery, users can browse the contents of their disks like they do in Windows Explorer. The only difference is that they see deleted files and folders along with the regular ones. The program can search for files by name or mask and show the probability of successful recovery for each file. Recovered files can be saved to any disks accessible on your system.
Users can also restore the full branch of the folders tree containing selected files and folders. Along with the main file data, the program can recover alternate data streams that are used on the NTFS file system to store additional information about files.
Handy Recovery supports all Windows file systems for hard and floppy drives including FAT12/16/32, NTFS/NTFS5 and image recovery from CompactFlash, SmartMedia, MultiMedia, and Secure Digital cards. It can recover compressed and encrypted files on NTFS drives.
Figure 4-18 shows a screenshot from Handy Recovery.
Tool: Mycroft
Source:http://www.dibsusa.com.Accessed 2/2007.
Figure 4-19This image shows the Mycroft tool. It can search for incriminating data using keywords. The text in the deleted message in this image highlights the key term:ecstasy.
Mycroft is an efficient, high-speed search engine that is useful for forensic investigators. This tool helps search a suspect’s computer hard disks for evidence at the rate of 5 MB per second. The searches can be started on any PC-based operating system. This tool can help forensic investigators eliminate systems from an investigation without copying, and “sniff out” relevant terms on a suspect computer on-site, when searching for or seizing specific evidence.
When an investigator carries out a search, Mycroft locks the suspect drive to prevent any change in the information in the drive. The investigator then has the freedom to search for the target data, without corrupting the evidence on the drive. The Mycroft application has an added advantage of allowing the investigator to specify up to 460 search items, which can include text files or images. All the search items are saved onto a boot disk and can be entered prior to the search, to save time for the investigation. This application also marks each physical location of a search hit so that it will be able to log it onto the boot disk. The Mycroft tool is used for the following purposes:
Sorting out suspect computers from a given pool before copying the data
Searching unallocated sectors in the disk to map the given information in order to identify stolen computers
Searching for references to specific types of crimes on the suspect systems
Conducting the first high-speed search to test the search attributesFigure 4-19 shows a screenshot from Mycroft.
Tool: O&O UnErase
Operating Systems:Windows NT/2000/XP
File Types:All
Media:Hard drives and removable media, including some digital cameras
Web Site:http://www.oo-software.com/home/en/products/oounerase/Cost:$29.95
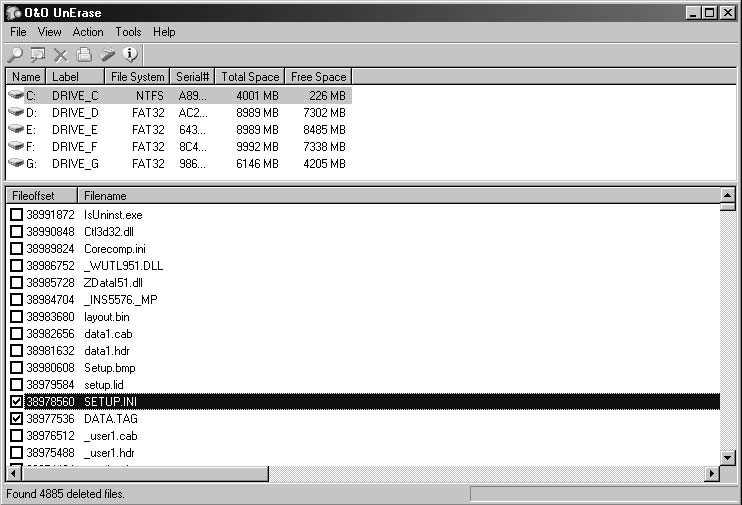
Source:http://www.oo-software.com/home/en/products/oounerase/.Accessed 2/2007.
Figure 4-20This image shows the O&O UnErase tool. Notice that it can search both NTFS and FAT file systems on different drives or partitions at the same time.
With O&O UnErase, investigators can recover data that was deleted from the hard disk due to virus attacks or software problems, or accidentally, by using an innovative algorithm, allowing many files to be restored at one time.
This tool is also equipped with a helpful user interface that enables users to recover deleted files. The GUI is similar to that of Windows Explorer.
Figure 4-20 shows a screenshot from O&O UnErase.
Operating**Systems:**
Windows
File**Types:**
All
Media:
Harddrives
Web**Site:**
http://www.pcinspector.de/Sites/file_recovery/info.htm?languag
Cost:
Free
Tool: PC Inspector File Recovery {#operatingsystems-windowsfiletypes-allmedia-harddriveswebsite-http-www-pcinspector-de-sites-file-recovery-info-htm-language-1cost-freetool-pc-inspector-file-recovery}
When a boot sector is damaged or a file is erased from the system, PC Inspector File Recovery recovers lost files and finds partitions automatically. This utility supports the FAT and NTFS file systems, and enables file recovery with the original time anddate stamp. It can recover files without the header entry and can restore them to the network drive, if required. PC Inspector File Recovery scans drives and automatically adds recovered files to an Explorer-style navigation tree retrieved from the deletedfolder. Figure 4-21 shows a screenshot from PC Inspector File Recovery.
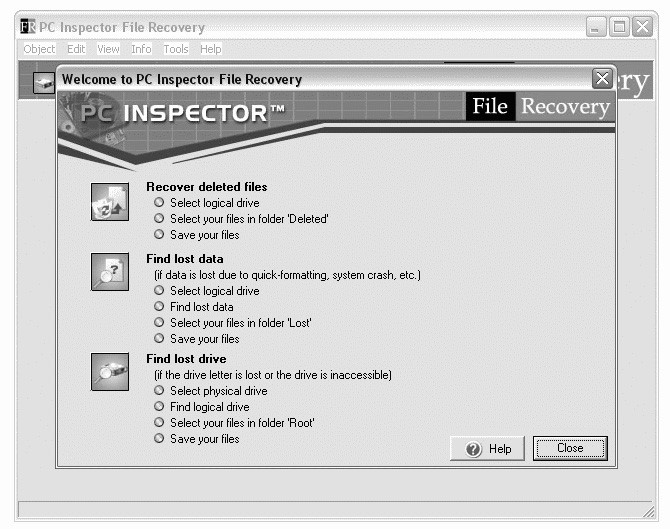
Source:http://www.pcinspector.de/Sites/file_recovery/info.htm?language=1.Accessed 2/2007.
Figu**re 4-21**This image shows the PC Inspector File Recovery tool.
| Operating Systems:Windows 9x, ME, NT, 2000, XP, 2003, and Vista |
|---|
Tool: R-Undelete
R-Undelete is an inexpensive solution for FAT and NTFS file systems. R-Undelete can undelete files on any valid logical disks visible by the host OS. It cannot, however, undelete files on damaged or deleted volumes, or in the case of hard drive repartitioning. R-Undelete 3.0 has a wizard-style interface and additional file recovery algorithm that increases file recovery quality.
The following are some of the features of R-Undelete:
Recovers files that were:
Removed without the Recycle Bin, or when the Recycle Bin has been emptied
Removed by virus attack or power failure
Undeletes lost files from FAT (FAT12, FAT16, FAT32), NTFS, and NTFS5
Recovers NTFS compressed, encrypted files, and alternative data streams
Recovers files on damaged or deleted partitions
Reconstructs damaged RAID
Figure 4-22 shows a screenshot from R-Undelete.
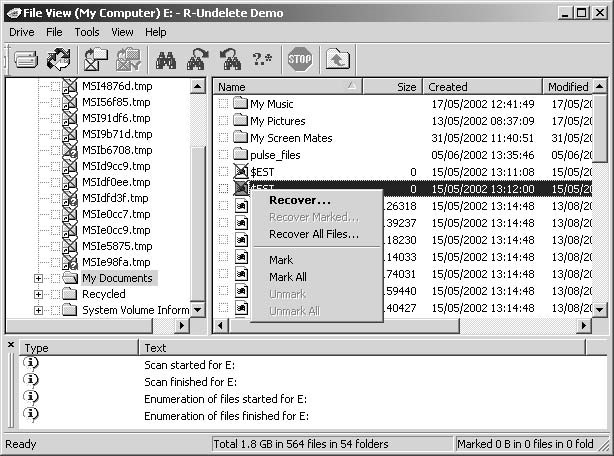
Source:http://www.r-undelete.com/.Accessed 2/2007.
Figure 4-22This image shows the R-Undelete tool.
Tool: Recover My Files
Operating**Systems:**
Windows
File**Types:**
All
Media:
Harddrives
Web**Site:**
Cost:
$99.95
Recover My Files data recovery software will recover deleted files emptied from the Windows Recycle Bin, or files lost due to the format or corruption of a hard drive, virus or Trojan infection, unexpected system shutdown, or software failure.
The following are some of the features of Recover My Files:
Recovers deleted files, even if emptied from the Recycle Bin
Recovers formatted hard drives, even if the user has reinstalled Windows
Recovers a user’s files after a hard disk crash
Retrieves files after a partitioning error
Recovers documents, photos, video, music, and e-mail
Recovers files from hard drive, camera card, USB, Zip, floppy disk, or other media
Recover My Files is compatible with Windows XP and works with FAT12, FAT16, FAT32, NTFS, and NTFS5 filesystems
Figure 4-23 shows a screenshot from Recover My Files.
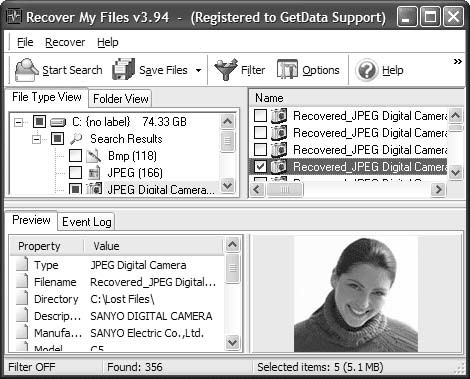
Source:http://www.recovermyfiles.com/.Accessed 2/2007.
Figure 4-23This image shows the Recover My Files tool. Notice that it can preview image files before recovering them.
| Operating Systems:Windows Vista/XP/2000/NT/ME/98/95 |
|---|
Tool: Recover4all Professional
With Recover4all Professional software, a user can recover files that were accidentally deleted in Windows. It does not matter if the files went through the Recycle Bin, and have been lost since the bin was emptied, or were directly deleted. To prevent files that were already deleted from becoming overwritten, Recover4all does not require installation, and can run directly from a floppy disk.
The following are some of the features of Recover4all Professional:
Supports all file types including documents, images, movies, and music
Can recover from formatted drives and within deleted folders
Supports all NTFS and FAT file systems, all kinds of compressed drives and files, Windows ME/XP protected files, all RAID levels, and all third-party encrypted drives not encrypted by Windows
Supports long file names in all languages
Supports drives recognized by Windows with IDE, SCSI, USB, PCMCIA, and otherinterfaces
Supports local internal and external drives, such as hard disks; removable drives, like Zip drives, floppy disks, and magneto-optical discs, and all memory cards like CompactFlash, SmartMedia, Secure Digital, and Memory Stick
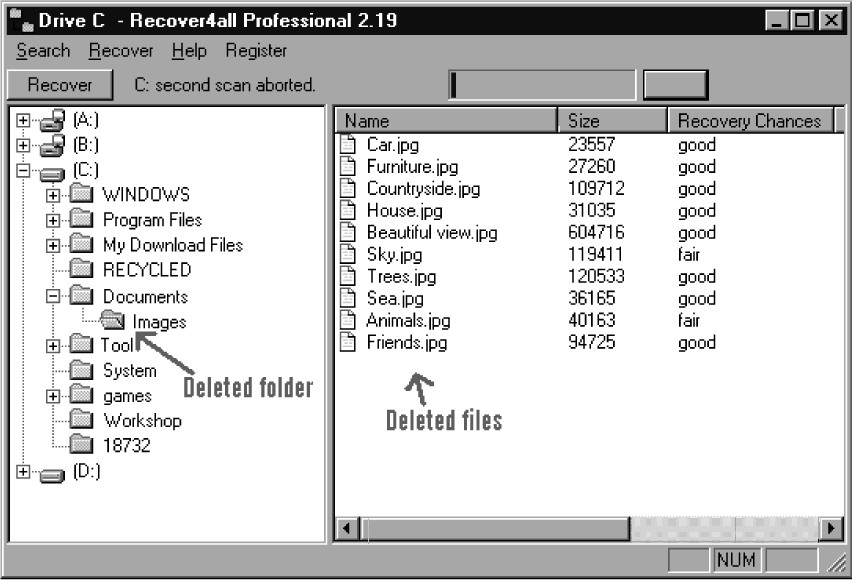
Source:http://www.recover4all.com/.Accessed 2/2007.
Figure 4-24This image shows the Recover4all tool.
Multithreaded on FAT drives: a user can browse and recover while the program still searches deleted files
Does not require installation to protect already deleted files from becoming overwritten
Does not recover files to the drive where they were deleted from, in order to protect them from becom-ing overwritten
Figure 4-24 shows a screenshot from Recover4all Professional.
Operating**Systems:**
Windows
File**Types:**
All,includingcompressedfiles
Media:
Harddrives,includingRAIDsystems,andremovablemedia
Web**Site:**
Cost:
$29.95
Tool: Restorer2000 {#operatingsystems-windowsfiletypes-all-includingcompressedfilesmedia-harddrives-includingraidsystems-andremovablemediawebsite-http-www-restorer2000-com-cost-29-95tool-restorer2000}
Restorer2000 can recover data in NTFS or FAT partitions that has been deleted, erased, or reformatted due to the following reasons:
The Recycle Bin is emptied or files are deleted using the Shift+Delete key combination.
The file was deleted due to hardware/software misconfiguration, power failure, or virus attack.
The hard drive has been accidentally formatted.
There were problems during boot up.
The Restorer2000 application can recover files with foreign language file names, long file names, NTFScompressed file names, and alternative data streams, such as Windows 2000 file information. The software has adjustable parameters that give the forensicinvestigator full control over the recovery procedure. Drive image creation is also a feature of this tool, as long as the system’s hardware is fully functional. Figure 4-25 shows a screenshot from Restorer2000.
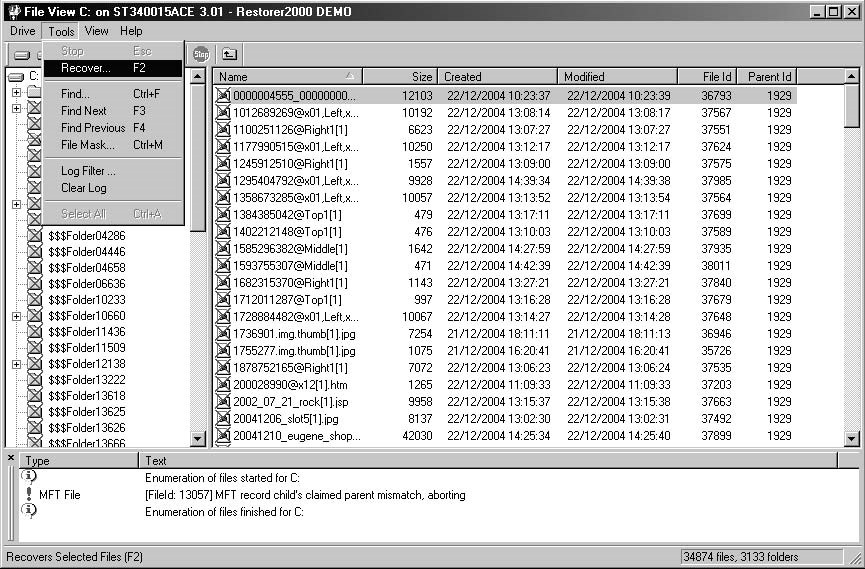
Source:http://www.restorer2000.com/.Accessed 2/2007.
Figure 4-25This image shows the Restorer2000 tool.
Tool: Search and Recover
Operating Systems:Windows
File Types:All, including e-mail messages
Media:All hard drives and removable media
Web Site:http://www.iolo.com/
Cost:$29.95 (shareware)
Search and Recover combines powerful technology with intuitive features to rescue data from a user’s drives or devices. Search and Recover allows the investigator to quickly recover deleted or destroyed files, folders, songs, pictures, videos, programs, critical system components, Web pages, and e-mail messages in Microsoft Outlook and Outlook Express, Netscape, and Eudora.
The following are some of the featuresand advantages of Search and Recover:
Recovers data to optical media:Saves recovered data directly to CD or DVD to keep it safe from further harm
Immediate recovery: Runs rescue tools directly from a CD to prevent further data loss and ensure recovery results
Source:http://www.iolo.com/.Accessed 2/2007.
Figure 4-26This image shows the Search and Recover tool. This application allows users to recover files as well as e-mail messages.
Disk imaging: Makes data recovery easy by creating mirror copies of entire drives prior to or after a d isaster
Virtual drives: Keeps data safe by creating virtual, or logical, drives that work just like a normal hard drive, CD, or DVD
Secure file deletion: Permanently erases sensitive information from a user’s PC or digital device
Extended Outlook recovery: Recovers deleted tasks, notes, journals, contacts, and more from Microsoft Outlook
Figure 4-26 shows a screenshot from Search and Recover.
Operating**Systems:**
Windows98,98SE,ME,2000,andXP
File**Types:**
All
Media:
Harddrivesandremovablemedia
Web**Site:**
Cost:
$29.95
Tool: SUPERFileRecover {#operatingsystems-windows98-98se-me-2000-andxpfiletypes-allmedia-harddrivesandremovablemediawebsite-http-www-superfilerecover-com-cost-29-95tool-superfilerecover}
SUPERFileRecover can recover deleted files, such as documents, spreadsheets, pictures, and movies. The following are some of the features of SUPERFileRecover:
Utilizes read-only scanning, so that the data on a user’s drive remains intact no matter how manytimes he or she scans and attempts recovery
Searches most drives in less than one minute; search time varies depending on search criteria and the number of deleted files on the drive
Previews text documents and pictures to find the specific file a user may have deletedFigure 4-27 shows a screenshot of SUPERFileRecover.
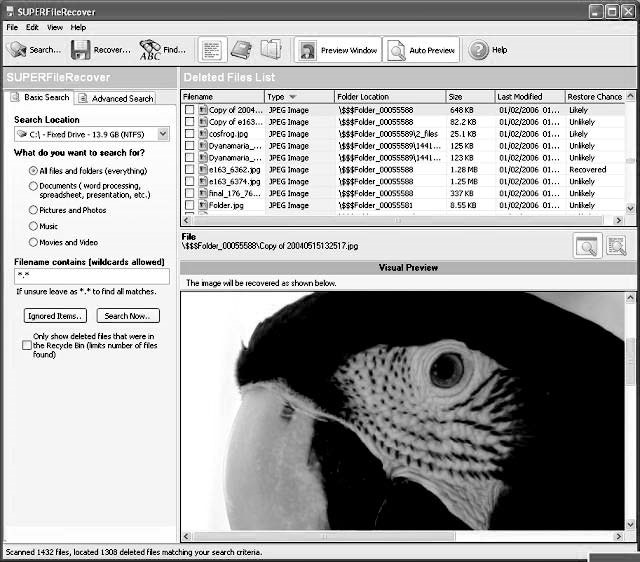
Source:http://www.superfilerecover.com/.Accessed 2/2007.
Figur**e 4-27**This image shows the SUPERFileRecover tool. This application previews images before they are recovered.
| Operating Systems:Windows NT 4.0 Workstation, 2000 Professional, XP Home Edition, |
|---|
Tool: Undelete
Undelete replaces the Windows Recycle Bin with a “Recovery Bin” that intercepts all deleted files, no matter how they were deleted. Undelete supports NTFS and 16/32-bit FAT file systems, but not the 12-bit FAT file system. (The 12-bit FAT file system is used on FAT volumes smaller then 16 MB in size, such as 1.44-MB floppy diskettes.) Right-click the file, selectRecover, and the file is back. Undelete 5 includes Emergency Undelete, which can recover files deleted before Undelete was installed, provided they haven’t been overwritten on the user’s hard drive, and SecureDelete, an electronic shredder to completely erase confidential files.
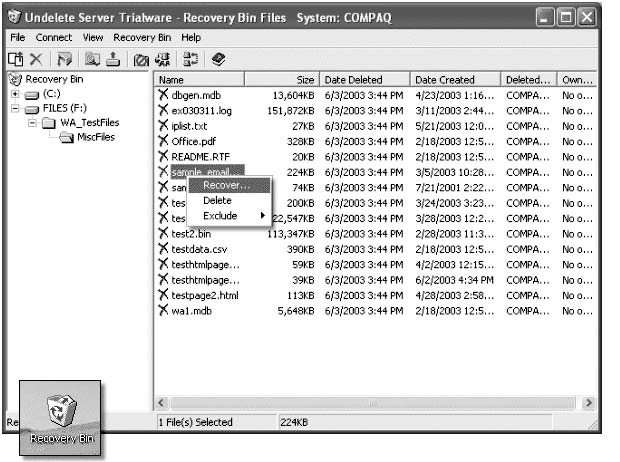
Source:
http://www.undelete.com/file-recovery.asp
Accessed 2/2007.
Figure 4-28This image shows the Undelete tool. Notice the Recovery Bin feature in this image.
The following are some of the features of Undelete:
Undelete automatically captures old versions of Microsoft Office files (Word, Excel, and PowerPoint), allowing for the recovery of earlier versions that have been saved over.
The Recovery Bin mimics the directory structure of the user’s disk, and includes a powerful search func-tion, making it easy to find and recover files.
The Undelete Professional Edition can connect to the Undelete Server Edition Recovery Bins installed on the network file servers. Ifa user deletes a file on a network share, he or she can recover it remotely from the system he or she is using.
Figure 4-28 shows a screenshot from Undelete.
Operating**Systems:**
Windows/MacOS9.xandX
File**Types:**
All
Media:
Harddrivesandremovablemedia
Web**Site:**
Cost:
$39.95(Windows);$129.95(Mac)
Tool: VirtualLab {#operatingsystems-windows-macos9-xandxfiletypes-allmedia-harddrivesandremovablemediawebsite-http-www-binarybiz-com-vlab-cost-39-95-windows-129-95-mac-tool-virtuallab}
VirtualLab recovers deleted files from removable drive formats and digital camera media. It recovers files from disks no longer recognized by the operating system. The VirtualLab application also undeletes files thrown in thetrash or deleted by a virus. It recovers deleted files and ghosted or damaged partitions. The program also recovers files after a format or restore from original system disks. It recovers damaged RAID servers and failed rebuilds. The X1 application quickly locates e-mails, files on the hard disk, and Web pages. Figure 4-29 shows a screenshot of the columns generated by X1.
Source:http://www.binarybiz.com/vlab/.Accessed 2/2007.
Figure 4-29This image shows the VirtualLab X1 tool.
Tool: WinUndelete
WinUndelete is part of the WinRecovery suite of applications. It can recover deleted files from hard drives, floppy disks, Zip drives, USB external drives, digital camera cards, and more. WinUndelete recovers deleted files after emptying the Recycle Bin, or using other deletion actions that bypass the Recycle Bin. WinUndelete can recover data from both FAT and NTFS, file systems.
| Operating Systems:Windows 98/NT/2000/ME/XP/2003 |
|---|
The following are some of the features of WinUndelete:
Supports FAT12/16/32, NTFS, and NTFS5 file systems
Performs nondestructive and read-only scan and file recovery
Sorts files by name, type, size, date, and more
Displays a list of files or shows the entire folder structure
Restores original create and modified file dates
Supports non-English languages
Filters files by extension and file type
Bypasses temporary Internet files and zero-length files
Enables partial file name and path name search
Enables saving deleted files to WinUndelete image file before recovery
Recovers NTFS compressed data streams
Previewsimages, plain text, and Microsoft Office documents before recovery
Recovers files deleted even after the user has emptied the Recycle Bin, files deleted accidentally from a network share, files deleted from the DOS command prompt, and files deleted in other applications, or by viruses
Figure 4-30 shows a screenshot from WinUndelete.
Source:http://www.winundelete.com/.Accessed 2/2007.
Figure 4-30This image shows the WinUndelete tool.
Operating**Systems:**
WindowsNT/2000/XP/2003/Vista
File**Types:**
All
Media:
Harddrives,includingRAIDarrays,andremovablemedia
Website:
Cost:
$49.95
Tool: Zero Assumption Recovery {#operatingsystems-windowsnt-2000-xp-2003-vistafiletypes-allmedia-harddrives-includingraidarrays-andremovablemediawebsite-http-www-z-a-recovery-com-cost-49-95tool-zero-assumption-recovery}
Zero Assumption Recovery provides a suite of highly effective and thorough data recovery software for Microsoft Windows operating systems. It recovers data lost due to accidental reformatting, power spikes, virus attacks, and hardware malfunctions. ZAR isa data recovery solution for FAT16/FAT32/NTFS file systems. The following are some of the features of Zero Assumption Recovery:
Runs on Windows NT/2000/XP/2003/Vista
Supports FAT16, FAT32, and NTFS (all versions) file systems
Provides limited ext2 (Linux file system) support
Supports partition recovery
Source:http://www.z-a-recovery.com/.Accessed 2/2007.
Figure 4-31This image shows the Zero Assumption Recovery tool. This screen shows files that can be recovered.
Supports hardware RAID 0 and RAID 5 recovery
Supports long and international file names
Supports native NTFS compression
Figure 4-31 shows a screenshot fromZero Assumption Recovery.
Tools for Use with UNIX-Based Systems
Tool: e2undel
Operating Systems:Linux ext2 only
Web Site:http://e2undel.sourceforge.net/
Cost:Free
The e2undel tool supports Linux systems with the ext2 file system. It includes a library that can recover deleted files by the file name.
Ext2 is an old UNIX file system. When a file is recovered in a medium, three parts of the file should be checked: filecontent; metadata that contains creation time, date, owner and user rights of the file; and the file name. This tool does not manipulate the internal ext2 structure. It requires only read access to the file system.
This tool is not compatible with other Linux file systems, such as ext3, ReiserFS, XFS, and JFS. Figure 4-32 shows a screenshot from e2undel.
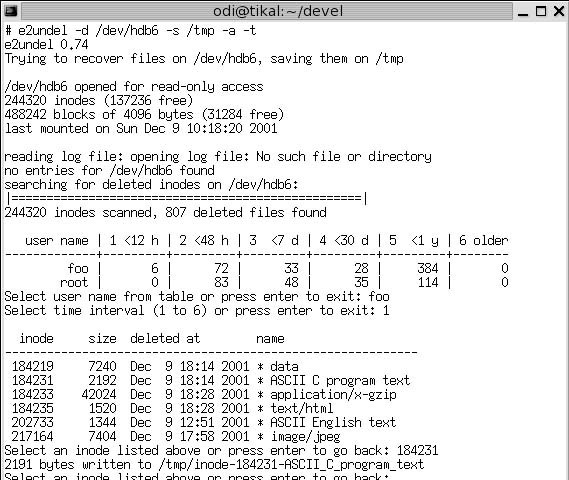
Source:http://e2undel.sourceforge.net/.Accessed 2/2007.
Figure 4-32This image shows the e2undel tool.
Operating**Systems:**
RecoversLinuxext2filesystem;HostOS:Windows9
x
/ME/NT/2000/XP
File**Types:**
All
Media:**L**
ogicalandphysicaldisks,includingnetworkdrivesandremovablemedia
Web**Site:**
Cost:
Free
Tool: R-Linux {#operatingsystems-recoverslinuxext2filesystem-hostos-windows9x-me-nt-2000-xpfiletypes-allmedia-logicalandphysicaldisks-includingnetworkdrivesandremovablemediawebsite-http-www-r-tt-com-cost-freetool-r-linux}
R-Linux is a free data recovery tool that supports the ext2 file system in Linux and other UNIX versions. Files from logical disks are recovered, even if the records are lost. It creates image files for the entire disk/partition, or for a part of it. Suchimage files can be processed like regular disks. The application recognizes localized names.
R-Linux can also recover files that can be saved on any disks accessible by the host operating system.
R-Linux uses a unique IntelligentScan technology and a flexible parameter setting that gives the investigator control over the data recovery. It recovers files from existing logical disks even when file records are lost. R-Linux is a “lite” version of a more powerful file recover utility, R-Studio. R-Studio utilizes the IntelligentScan technology to its full extent, and can recover data from partitions with broken file systems. Also, R-Studio can recover data over a network.
The following are some of the features of R-Linux:
Standard Windows Explorer–style interface
Can save recovered files on any disks visible to the host operating system
Recovers files from disks with bad sectors
Figure 4-33 shows a screenshot from R-Linux.








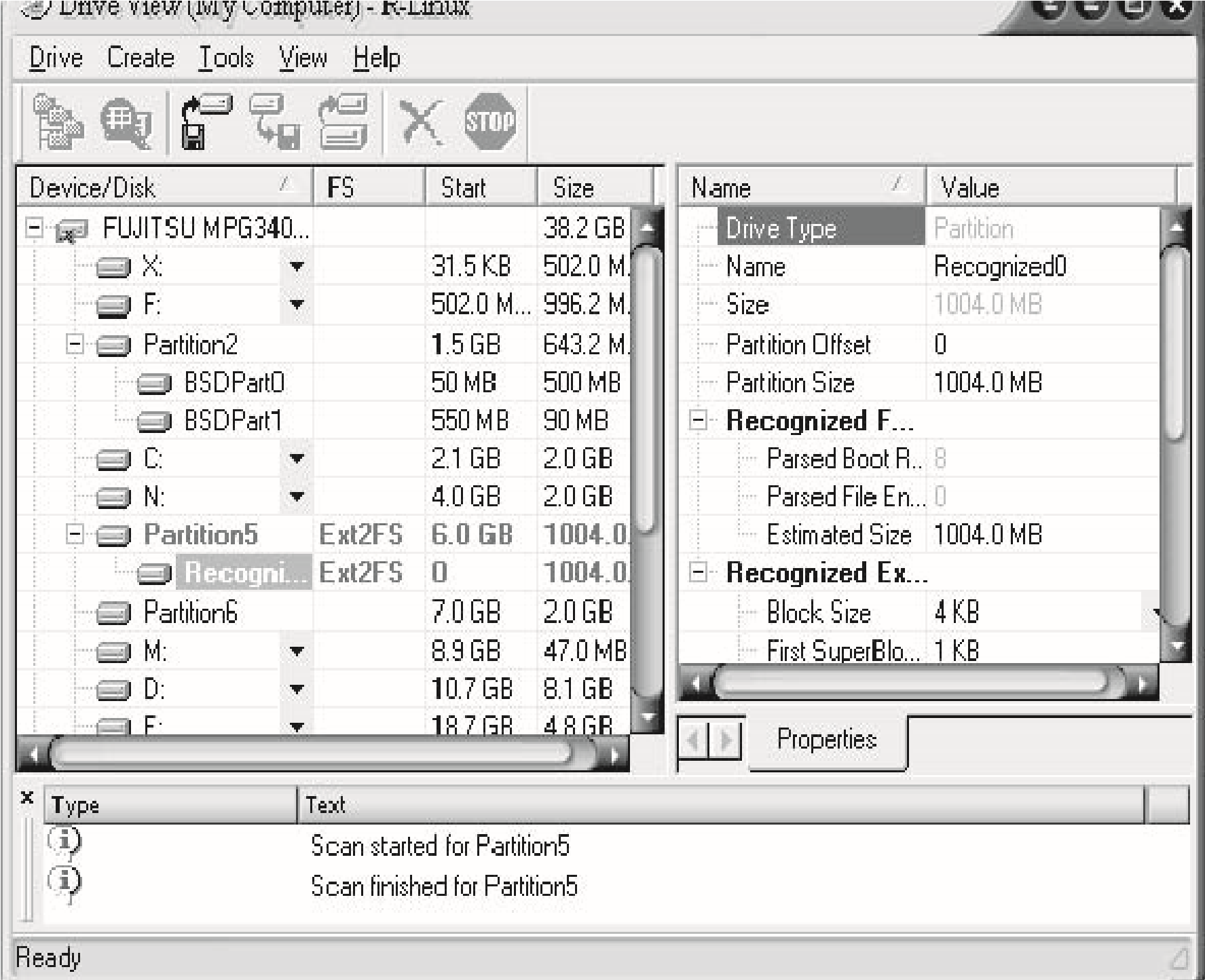
Source:http://www.r-tt.com/.Accessed 2/2007.
Fi**gure 4-33**This image shows the R-Linux tool. Notice that different partitions can be scanned and recovered.
Tool: Stellar Phoenix
Operating Systems:Linux ext2 and ext3; Macintosh OS version available
File Types:All
Media:Hard drives and removable media
Web Site:http://www.stellarinfo.com/
Cost:$129.00
Stellar Phoenix is fully automated data recovery software for Linux and supports the ext2 and ext3 file systems. An automated wizard walks the investigatorthrough three steps: Evaluate, Analysis, and Recover. During the scan, the tool automatically recognizes lost partitions, files, and folders for recovering data.
The tool has read-only functions. The recovered data is copied to another removable drive, other functional partition, or other hard drive/floppy disk/network volume.
Stellar Phoenix has different versions for different file systems. It allows for the recovering of data from hard drives that are damaged for any reason, such as accidental format, partition loss, or corruption due to a virus attack or directory deletion.
Figure 4-34 shows a screenshot from Stellar Phoenix.
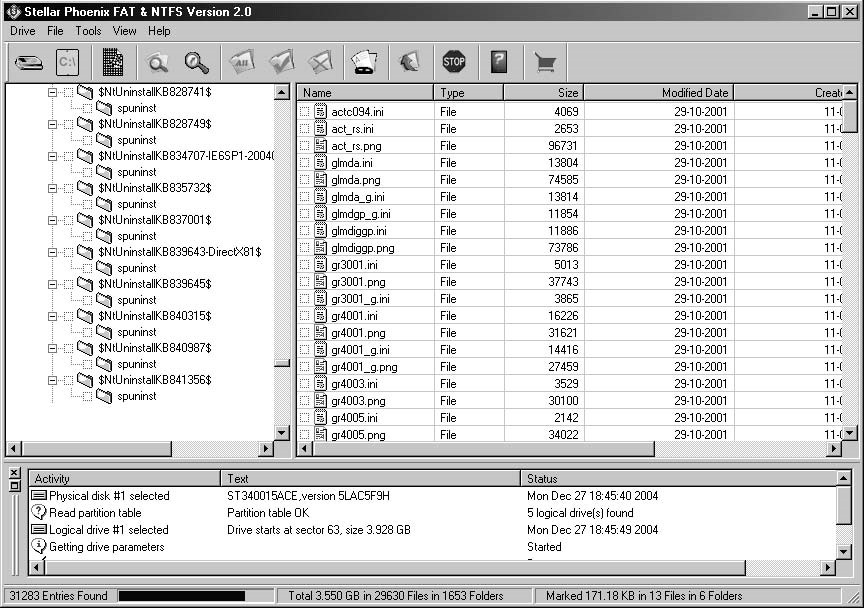
Source:http://www.stellarinfo.com/.Accessed 2/2007.
Figure 4-34This image shows the Stellar Phoenix tool.
Operating**Systems:**
WindowsandMacOS
File**Types:**
MicrosoftOfficefilesonly
Media:
N/A
Web**Site:**
Cost:
$39.50
Tool: OfficeFIX {#operatingsystems-windowsandmacosfiletypes-microsoftofficefilesonlymedia-n-awebsite-http-www-cimaware-com-cost-39-50tool-officefix}
OfficeFIX is a Microsoft Office recovery suite. OfficeFIX recovers the information from a damaged or corrupted file, and stores itinto a new file. It includes data recovery from ExcelFIX, AccesssFIX, and WordFIX. The following are some of the features of OfficeFIX:
It recovers data from MS Access 95/97/2000/XP.
It supports all versions of MS Excel.
It also recovers data from all versions of MS Word documents, including Word for Macintosh.
The following are some of the limitations of OfficeFIX:
It does not recover Excel sheets with:
Password-protected files
Visual Basic and macros
Array formulas
Pivottables (only cell values are recovered)
Source:http://www.cimaware.com/.Accessed 2/2007.
Figure 4-35AccessFIX and WordFIX are two tools that are included in the OfficeFIX suite.
- It does not recover password-protected access files if thesecurity fileoption is set.
| Operating Systems:Windows 9x/ME/2000/XP/2003 |
|---|
It does not recover password-protected Word files.
It recovers text data, table data, and basic formatting in a document.
It does not recover Japanese or Chinese characters.
WordFIX cannot currently repair embedded OLE objects in Word documents, such as Excel spread-sheets and Microsoft Visio diagrams, or audio or video files, ActiveX controls, or macros.
Figure 4-35 shows a screenshot from OfficeFIX.
Tool: Repair My Excel
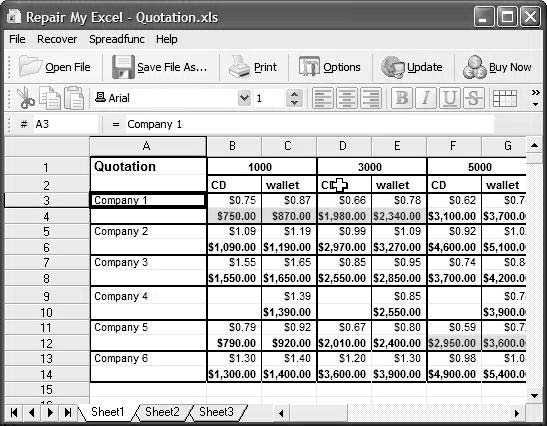
Source:http://www.repairmyexcel.com/.Accessed 2/2007.
Figure 4-36Repair My Excel is a very simple and limited freeware tool.
Repair My Excel is a Microsoft Excel file recovery software capable of restoring damaged or corrupt files that cannot be opened. Repair My Excel works with all versions of Microsoft Excel including 95, 97, 2000, XP, and 2003. It repairs Excel files, extracts the content of the damaged Excel file, and creates a new errorfree file.
It fixes errors like:
Operating**Systems:**
Windows
File**Types:**
Imagefiles
Media:
Harddrivesandremovablemedia
Web**Site:**
Cost:
$34.95
“Unable to read file”
“The document is corrupt and cannot be opened...”
The following are some of the key features of Repair My Excel:
Recovers all Excel versions, including Excel 97, 2000, 2002, XP, and 2003
Recovers the names of worksheets and Excel formulas
Repairs Excel formatting, including font, color, hyperlinks, and URLs• Offers a full preview of the recovered file when running the evaluation version Figure 4-36 shows a screenshot from Repair My Excel.
Tool: RecoverPlus Pro
RecoverPlus Pro is a data recovery tool that recovers deleted images from hard drives. It supports media recovery, photo recovery, card recovery, and file recovery. It scans the user’s card, stick, drive, CD, DVD, digital camera connection, reader, or anything with a drive letter, and usesSave Allfor saving to the directory the user wants. It supports more than 40 file types by default, and new formats can be added.
The following are some of the features of RecoverPlus Pro:
Supports picture recovery for JPG, JPE, JPEG, TIF, TIFF, GIF, BMP, PNG, PSD, EPS, PCX, raw CRW, CR2, NEF, ARW, MRW, DCR, FOVb, PEF, ORF, RAF, X3F, RDC, DNG, and RAW
Recovers RAW files from Canon, Nikon, Sony, Konica, Minolta, Rollei, Leica, Hasselblad, Kodak, Fuji, Olympus, Panasonic, Pentax, Sigma, Samsung, Adobe, and Foveon
Displays full-screen versions of recovered photos
Supports any connection with a drive letter, such as a hard or removable disk, reader, camera, card, stick, iPod, Image Tank, or CD/DVD via connections such as USB, PCMCIA, Firewire, and others
Figure 4-37 shows a screenshot from RecoverPlus Pro.
Source:http://www.arcksoft.com/.Accessed 2/2007.
Figure 4-37RecoverPlus Pro is a robust tool to recover image files.
Tool: ImageRecall
ImageRecall is digital photo recovery software. It recovers lost data and digitalimages from memory cards, hard drives, and all other media. It supports all popular images, including RAW, audio, video, and data files. The recovered files can be previewed (JPEG) and saved to a folder on the user’s hard drive, or burned directly to CD.The following are some of the features of ImageRecall:
Recovers faster (60% faster than previous versions)
Rebuilds corrupt image files
Scans cards for damage
Views photos during the recovery process
Backs up corrupted cards on a hard drive
Selects specific file types for recovery
Retrieves images from corrupt CDs
Saves recovered images directly to PC or CD
Operating**Systems:**
Windows9
x
/ME/NT4/2000/XPoranyMacOS9.1+,includingMacOSX
(
except
10.3.9)
File**Types:**
Imageandmediafiles
Media:
Harddrivesandremovablemedia
Web**Site:**
http://www.flashfixers.com/softwa
Cost:
$39.95
Figure 4-38 shows a screenshot from ImageRecall.
Source:http://www.flashfixers.com/software/.Accessed 2/2007.
Figure 4-38ImageRecall is a tool for recovering image files.
Tool: eIMAGE Recovery
eIMAGE Recovery can help a user recover digital images and media files lost on corrupted, erased, or damaged memory cards. It can also recover files lost due to a virus attack or electronic failure. Memory cards supported include, CompactFlash, SmartMedia,Memory Sticks, mmd, XD, multimedia, or Secure Digital memory cards. It supports file formats: BMP, JPG, JPEG, GIF, PNG, TIF, TIFF, Fuji Raw File (RAF), Kodak Raw File (DCR), Zigma Raw File (X3F), RIFF, AVI, MID, MIDI, MOV, MPG, MPEG, and WAV.
| Operating S**ystem:**Windows ME/NT/2000/XP/2003 |
|---|
Figure 4-39 shows a screenshot of eIMAGE Recovery.
Source:http://www.octanesoft.com/photo_recovery.html.Accessed 2/2007.
Figure 4-39eIMAGE Recovery includes a wizard that walks you through file recovery.
Tool: Word Repair
Word Repair is a data recovery program for Microsoft Word documents. It is designed to recover text from damaged or corrupt Word files (.doc files) that will not open normally. The recovered text can then be saved as an error-free Microsoft Word document.
Some common error messages that can prevent a user opening a Microsoft Word document include:
“The document name or path is not valid. Try these suggestions. Check the file permissions for the doc-ument or drive. Use the File Open dialog box to locate the document.”
“Word cannot open the document.”
“Word cannot open the document: user does not have access privileges.”
When a user attempts to open a Microsoft Word 97 document in Microsoft Word version
6.x_or 7._x, the document contains garbage characters.
Word Repair will allow the user to obtain access to the contents of corrupt word documents. It will repair Microsoft Word 6.0, 95, 97, 2000, XP, and 2003 for Windows and is simple to use. Open the corrupt Word file, preview the recoverable text in the preview window, and save this text to a new error-free Word file.
Operating**Systems:**
Windows
File**Types:**
MicrosoftWord6.0,Word95,97,2000,XP,and2003forWindowsfiles
Media:
Harddrives
Web**Site:**
Cost:
Free
Figure 4-40 shows a screenshot from Word Repair.

Source:http://www.repairmyword.com/.Accessed 2/2007.
Figure 4-40Word Repair can recover many different versions of Microsoft Word files.
Tool: Zip Repair Pro
Operating Systems:Windows
File Types:Compressed files (.zip)
Media:N/A
Web Site:http://www.ziprepair.com/
Cost:$29.95
Zip Repair Pro is a utility that will repair corrupt Zip files. Usually a corrupt Zip file gives the error message:
“Cannot open file: it does not appear to be a valid archive.” The following are some of the features of Zip Repair Pro:
Creates an error-free backup of a user’s original file for instant access
Fixes CRC errors in .zip files so that data can still be uncompressed
Supports spanned Zip volumes, including the Zip64 format; a user can now repair and extract from a spanned Zip set, even if part ofthe set is missing.
Supports huge file sizes 2 GB (as long as there is enough disk space)
Type
Tool: CD Data Rescue
Operating Systems:Windows
File Types:All
Media:CDs and DVDs
Web Site:http://www.naltech.com/cddr.htm
Cost:$19.95
CD Data Rescue recovers files from damaged, scratched, or defective CD-ROM, CD-R, and CD-RW discs. It also supports Mount Rainier/Easy Write MRW discs. With this product, a user can easily recover files, folders, or deleted files from CDs. It also can recover files from quick-formatted CD-RW discs.
CD Data Rescue recovers unreadable and deleted files from CDs recorded by common CD writing software in ISO and UDF formats. It features full real UDF recovery supported for UDF packet-writing software (mode B): DirectCD (including old versions and compressed CDs), InCD, packetCD, etc. The tool also supports discs recorded by Sony digital cameras.
The following are some of the features of CD Data Rescue:
Updated Recovery Wizard
Automatically detects and renames unnamed files with the correct file type
Complete UDF file system recovery
Uses exclusive recovery technology that allows a user to achieve the best performance recovering data
Can recover data fromCDs and DVDs recorded in the ISO 9660 format and UDF formatFigure 4-41 shows a screenshot from CD Data Rescue.
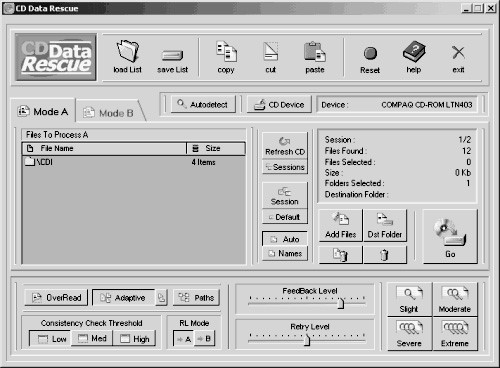
Source:http://www.naltech.com/cddr.htm.Accessed 2/2007.
Figure 4-41This image shows theCD Data Rescue screen.
Operating**Systems:**
Windows95/98/ME/2000/XP
File**Types:**
All
Media:
CDsandDVDs
Web**Site:**
Cost:
$39.00
Tool: CDRoller {#operatingsystems-windows95-98-me-2000-xpfiletypes-allmedia-cdsanddvdswebsite-http-www-cdroller-com-cost-39-00tool-cdroller}
CDRoller supports the industry-standard ISO 9660 file system, including Microsoft’s extensions for long file names support, and so-called Joliet extensions. CDRoller also supports discs formatted in the UDF file system, including versions 1.02, 1.50, 2.0, 2.01, and also the UDF bridge format. The following are some of the features of CDRoller:
- Includes support for a wide set of CD and DVD formats such as CD-DA, CD-ROM, CD-WO,
CD-ROM XA and Mixed-Mode CD, stamped multisession CD, CD-MRW (Mt. Rainier CD-RW),
DVD-ROM, DVD-R, DVD-RW, DVDR, DVDRW, and DVD-RAM
Effectively retrieves the data off discs created by drag-and-drop CD/DVD writing software
Recovers CD and DVD data created by standalone devices that record directly onto discs
Includes a built-in video splitter that splits the recovered VOB or VRO files into a several clips (scenes), automatically converting a “raw” DVD-video into MPEG files without the loss of quality; specially tested on the discs created by Hitachi DVD camcorders
Retrieves backup files from discs recorded in several stages (multisession discs)
Source:http://www.cdroller.com/.Accessed 2/2007.
Figure 4-42CDRoller can recover data from many DVD and CD formats.
Includes a built-in UDF reader; there is no need to install third-party software, for example, the Roxio (Adaptec) UDF reader driver
Finds and retrieves the lost files on UDF discs, including accidentally deleted files, files on quick- formatted discs, files on incorrectly closed discs
Identifies the lost files on ISO/Joliet discs with a damaged file system (volume descriptors, path tables, and directories), using raw data only
Rescues the data from scratched, damaged, or defective discs
Provides direct accessto the hardware, bypassing the Windows file system, and looks for lost tracks (sessions) every time a user inserts a new disc into the drive Figure 4-42 shows a screenshot from CDRoller.
Tool: DiskInternals Flash Recovery
Operating Systems:Windows 95, 98,ME, NT, 2000, XP, and 2003 Server
File Types:All
Media:Flash memory devices
Web Site:http://www.diskinternals.com/flash-recovery/features.shtmlCost:$39.95
DiskInternals Flash Recovery is a flash memory file recovery tool that restores corrupted and deleted photographs, or ones lost due to hardware malfunctions. This utility works even if a memory card was reformatted. The program recovers images from hard drives, external drives, cameras, and flash memory devices such as SmartMedia, CompactFlash, Memory Stick, MicroDrive, xD Picture Card, Flash Card, PC Card, Multimedia Card, Secure Digital Card, and many others.
The following are some of the features of DiskInternals Flash Recovery:
Easy Recovery Wizard
Can preview and recover JPEG, JPG, TIFF, BMP, PNG, GIF, TGA, and other images
Supports FAT12, FAT16, FAT32, NTFS (NT 4), and NTFS5 (2000, XP) file systems
Source:http://www.diskinternals.com/flash-recovery/features.shtml.Accessed 2/2007.
Figure 4-43Flash Recovery can restore most deleted or damaged photograph files.
Can save recovered files on any (including network) disks visible to the host operating system
Creates recovery snapshot files for logical drives; these files can be processed like regular disks.
Recovers pictures deleted by accident
Recovers photos from erased or formatted media or deleted from digital cameras or the Recycle Bin
Allows a user to preview recoverable images before purchasing the programFigure 4-43 shows a screenshot from DiskInternals Flash Recovery.
Operating**Systems:**
Windows
File**T**ypes:
All
Media:
CDsandDVDs
Web**Site:**
http://www.diskinternals.com/cd-dvd-recove
Cost:
$39.95
Tool: DiskInternals CD and DVD Recovery {#operatingsystems-windowsfiletypes-allmedia-cdsanddvdswebsite-http-www-diskinternals-com-cd-dvd-recovery-cost-39-95tool-diskinternals-cd-and-dvd-recovery}
DiskInternals CD and DVD Recovery is a software solution capable of recovering data from CDs and DVDs, including multisession discs. It supports the following discs: CD-R, CD-RW, DVD-R, DVRR, DVD-RW, DVRRW, DVDR DL, DVD-R DL, and DVD-RAM.
The program recovers any type of files (data, pictures, video, and music) and processes ISO 9660, Joliet, and UDF file systems. The program uses a smart file recovery algorithm that skips bad sectors.
Source:http://www.diskinternals.com/cd-dvd-recovery/.Accessed 2/2007.
Figure 4-44CD and DVD Recovery includes a wizard to walk you through the restoration process. The program shows every file that can be recovered. You can choose files to restore.
The process of recovery is straightforward. The program starts working automatically, and doesn’t require the additional setup changes. Advanced users can use a manual recover process that allows them to isolate each session or track, and choose the appropriate file system per session.
Figure 4-44 shows a screenshot from DiskInternals CD and DVD Recovery.
| Operating Systems:Windows 98/ME/NT/2000/XP/2003 |
|---|
Tool: inDisc Recovery
inDisc Recovery is CD/DVD data recovery software. It is specifically designed to recover any type of deleted, lost, or unreadable files and folders from damaged, scratched, or defective CDs and DVDs created by CD/DVD writing software in ISO 9660 and UDF formats, as well as Microsoft’s extensions for long file names support and Joliet extensions. CD-R, CD-RW, DVD-R, DVRR, DVD-RW, DVRRW, DVD1R DL, DVD-R DL, and DVD-RAM discs are supported.
The user can access all tracks and sessions located on the damaged disc. The following are some of the features of inDisc Recovery:
Effectively recovers lost data from CD and DVD discs created by common CD/DVD writing software in ISO, UDF, and Joliet formats
Finds and recovers deleted files from RW discs that have been deleted through Quick Format mode
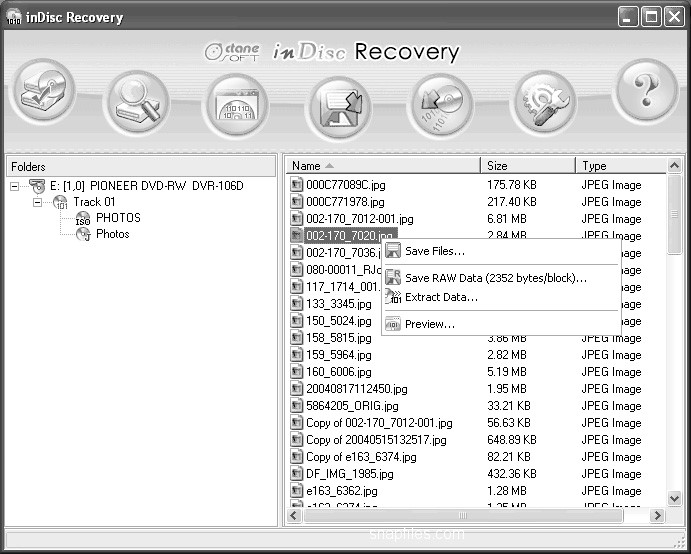
Source:http://www.octanesoft.com/.Accessed 2/2007.
Figure 4-45inDisc Recovery can recover files from CDs andDVDs.
Supports CD-ROM, CD-R, CD-RW, DVD-ROM, DVD-R, DVD-RW, DVDR, DVDRW, and DVD-RAM
Supports multisession media
Ability to preview image, ASCII, and hex data
Figure 4-45 shows a screenshot from inDisc Recovery.
Operating**Systems:**
Windows(butworksonMac-formatteddiscs)
File**Types:**
All
Media:
CDsandDVDs
Web**Site:**
http://www.isobuster.com/isobuster.
Cost:
$29.95
Tool: IsoBuster {#operatingsystems-windows-butworksonmac-formatteddiscs-filetypes-allmedia-cdsanddvdswebsite-http-www-isobuster-com-isobuster-phpcost-29-95tool-isobuster}
IsoBuster is a highly specialized, yet easy-to-use, CD and DVD data recovery tool. It supports all CD and DVD formats, and common CD and DVD file systems. Start upIsoBuster, insert a CD or DVD, select the drive (if not selected already), and let IsoBuster compile the media. IsoBuster immediately shows the user all the tracks and sessions located on the media, combined with all file systems that are present. This way, the user gets access to all the files and folders per file system instead of being limited to one file system. The user can access data from older sessions and data that Windows does not see or hides from view.
The following are some of the features of IsoBuster:
- Recovers data from all possible CD and DVD formats:
CD-i, VCD, SVCD, SACD, CD-ROM, CD-ROM XA, CD-R, CD-RW, CD-MRW, DVD-ROM, DVCD, DVD-RAM, DVD-R, DVD-RW, DVDR, DVDRW, DVDMRW, DVDR Dual Layer, DVD-R Dual
Layer, DVDRW Dual Layer, DVDVR, DVDVRW, DVD-VR, and DVD-VM
Exclusively provides all device access, media access, data gathering, and interpretation; it does not rely on Windows to provide or interpret the data, and so can work completely independently from Windows’ limitations.
Uses primary and secondary file systems to get to the data and/or make use of file system data that might be ignored or forgotten by the operating system
Supports mounting several virtual sessions inside a single DVDRW or DVD-RW track
Reads and extracts files, CD/DVD images, tracks, and sessions from all optical media
Scans for lost UDF files and folders, and for lost ISO 9660/Joliet sessions
Finds lost data on CDs or DVDs created with integrated drag-and-drop applications, otherwise known as packet-writing software; optimized, but not exclusively, for Roxio Direct CD, Roxio Dragto-Disc, Ahead/Nero InCD, Prassi/Veritas/Sonic DLA, VOB/Pinnacle Instant-Write, and CeQuadrat Packet CD
Supports direct CD compressed files
Built-in UDF reader,UDF 1.02 (e.g., DVDs), UDF 1.5 (e.g., packet writing on CD-R, DVD+R, DVD-R, CD-RW, DVD+RW, and DVD-RW), and UDF 2.01, 2.50
Finds lost pictures created and saved to CD or DVD with Sony Mavica, other digital cameras, or other devices with embedded UDF writefunctionality
Finds lost movies created and saved to CD or DVD with Hitachi, other digital cameras, or other devices with embedded UDF write functionality
Automatically finds extensions based on file content to try to give an appropriate name to an orphaned file; this built-in file identifier assigns the proper extension to the file so that Windows applications can open the file. Only needed for orphaned files without a name.
Has transparent built-in support for Mac Resource Fork extensions in the UDF filesystemFigure 4-46 shows a screenshot from IsoBuster.
Tool: PC Inspector Smart Recovery
Operating Systems:Windows 9x/ME/NT 4.0/XP/2000
File Types:Media and image files
Media:Flash drives, digital cameras
Web Site:http://www.pcinspector.de/smart_media_recovery/uk/welcome.htm
Cost:Free (sometimes bundled with digital cameras)
PC Inspector Smart Recovery recovers data from data devices, such as CompactFlash cards, SmartMedia, and digital cameras. It recovers accidentally deleted files, videos, and pictures from media devices. The following are some of the features of PC Inspector Smart Recovery:
Recovers data from CONVAR for CompactFlash cards, SmartMedia, Sony Memory Sticks, IBM Micro Drives, Multimedia Cards, Secure Digital cards, or any other data carrier for digital cameras
Supports the following picture formats: .jpg, .amr,.tif, .bmp, .gif, Canon .crw, Fuji .raf, RICOH .raw, Olympus .orf (E-XX), Olympus .orf (C5050), Nokia 3gp, Kodak .dcr, Minolta .mrw, Nikon .nef (D1H/
D1X), Nikon .nef (D2H/D2X), Nikon .nef (E5000/E5700), Sigma/Foveon .x3f, mp4, QuickTime .mov
(Konica Minolta), Video files in .avi, and audio files in .wav, and .dss format Figure 4-47 shows a screenshot from PC Inspector Smart Recovery.
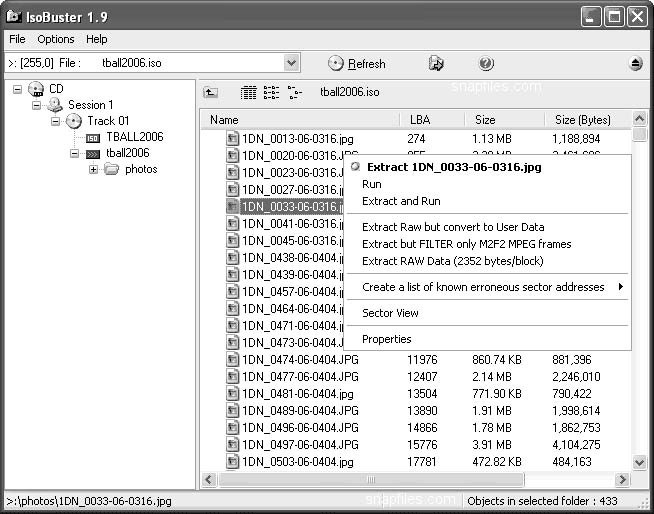
Source:http://www.isobuster.com/isobuster.php.Accessed 2/2007.
Figure 4-46IsoBuster includes a variety of formats for extraction.
Source:http://www.pcinspector.de/smart_media_recovery/uk/welcome.htm.Accessed 2/2007.
Figure 4-47A user can recover many different types of media files using PC Inspector Smart Recovery.
Recovering Deleted Partitions
Deletion of a Partition
In Windows systems, a user can delete a partition by:
Using the Windows interface
Using a command line
What Happens When a Partition Is Deleted?
When a user deletes a partition on any logical drive, all the data on that drive is lost.
If a user deletes a partition on a dynamic disk, all dynamic volumes on the disk are deleted, thus cor-rupting the disk.
Deletion of a Partition Using the Windows Interface
Use the following procedure to delete a partition using the Windows interface:
Open Computer Management:
ClickStartControl Panel.
Double-clickAdministrative ToolsComputer Management.
In the console tree:
ClickComputer Management (Local)StorageDisk Management.
Right-click the partition, logical drive, or basic volume you want to delete, and then clickDelete Partition.
Figure 4-48 shows deletion of a partition using Computer Management.
Deletion of a Partition Using the Command Line
Use the following steps to delete a partition using the command line:
At the command prompt, typediskpart.
At the DiskPart prompt:
Typelist disk:
Note the disk number of the disk from which the partition isto be deleted.
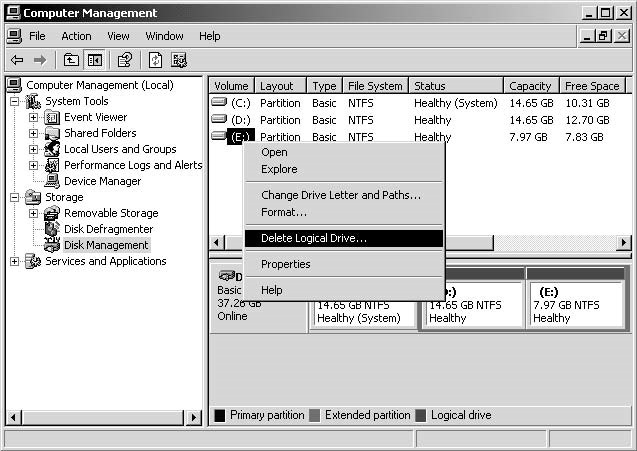
Figure 4-48This image shows deletion of a partition using the Computer Management utility.
Typeselect disk n:
Selects disk numbern.
Typelist partition:
Note the number of partitions.
Typeselect partition n:
Selects partitionn.
List disk:It gives the list of disks and information about the each disk, such as its size, free space available, whether the disk is basic or dynamic, and if the disk uses either a master boot record (MBR) or GUID partition table (GPT) partition.
Select**disk:**It selects the specified disk;_n_denotes the disk number.
List partition:It shows the list of partitions in the partition table of the current disk.
Select partition:It selects the specified partition n that denotes the partition number. If the partition is not provided, the select command lists the current partition.

Common**Terms**
Delete partition:It deletes the partition. Partitions such as a system partition orboot partition, which contains an active paging file or crash dump, cannot be deleted.
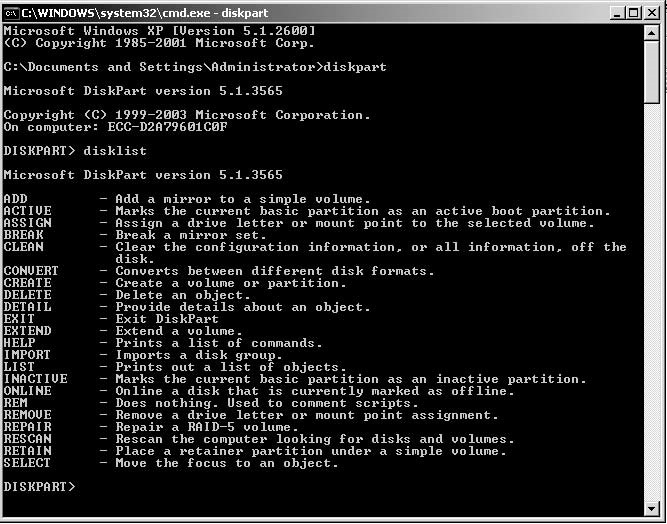
Figure 4-49Image shows the available switches that can be used with the DiskPart command
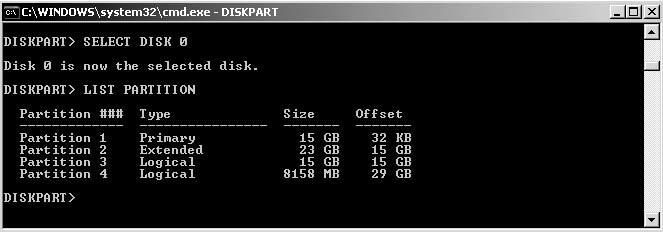
Figure 4-50Notice the four different partitions. Different partitions can have different types, such as Primary or Extended with logical drives being part of the extended partition.
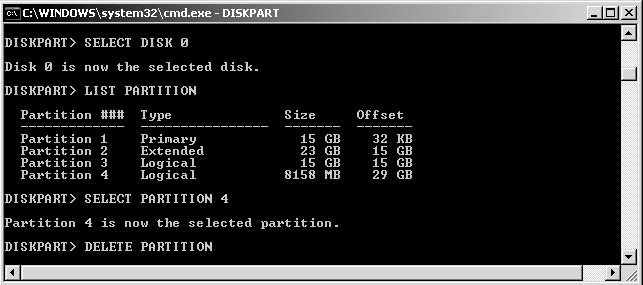
Figure 4-51The command Delete Partition will remove the information from partition4. The data will still be stored, but it will be unavailable to the user, as the space will be listed in the OS as free space and may be overwritten as new information is stored.
Typedelete partition:
Deletes the partition.
Figures 4-49, 4-50, and 4-51 show screenshots from DiskPart.
Recovery of Deleted Partitions
The recovery of deleted partitions is the process by which a user can evaluate and extract deleted partitions. The partition recovery process is important in case of data recovery. This recoveryhelps in recovering the partitions that are lost accidentally, or due to virus, software malfunction, or even sabotage. There are some tools available for the recovery of deleted partitions.
Tools to Recover Deleted and Damaged Partitions
Table 4-5 lists tools used to recover partitions:
| Acronis Recovery Expert | GetDataBack | Recover It All! |
|---|---|---|
| Active@ Disk Image | Deleted NTFS Partition Recovery | Scaven |
| Active@ Partition Recovery | Partition Table Doctor | TestDisk |
| DiskInternals Partition Recovery |
Table 4-5**These tools are used to recover deleted or damaged partitions**
Tool: Acronis Recovery Expert
Acronis Recovery Expert, included in the Acronis Disk Director Suite 10.0, completely protects a user’s data, allowing him or her to recover deleted or lost partitions. It also protects the user’s system from hardware or software failure, virus attack, orhacker intrusion.
If a user’s PC becomes unbootable after a power outage or a system error, he or she can recover it with Acronis Recovery Expert.
The following are some of the key features of Acronis Recovery Expert:
Supports the following file systems: FAT16, FAT32, NTFS, HPFS (OS/2); ext2, ext3, ReiserFS, Swap (Linux)
Provides automatic and manual recovery modes
Independently works from bootable CDs or diskettes, enabling a user to recover partitions even if his or her operating system fails to boot
Supports large disks over 180 GB
Provides a Windows XP–like wizard-style interface for superior usability and ease of useFigure 4-52 shows a screenshot from Acronis Recovery Expert.
Tool: Active@ Disk Image
Active@ Disk Image is a DOS-based solution designed for complete backup and restoration of the whole HDD, as well as the particular FAT/NTFS partitions and logical drives.
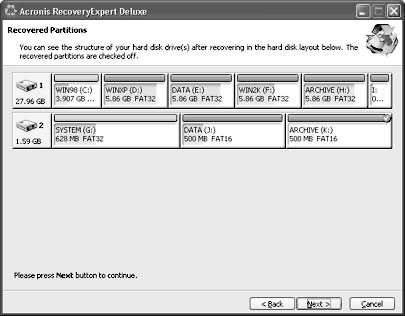
Source:http://www.acronis.com/.Accessed 2/2007.
Figu**re 4-52**You can see from this image that each of these physical hard drives has several partitions. Note the partitions that were recovered are checked off.
Users can create compressed and noncompressed raw images (containing all of a drive’s data—a mirrorof a drive’s surface stored in one or a set of files), as well as compressed data images (containing only the drive’s used clusters, saving users space and increasing speed).
A unique feature of Active@ Disk Image is the ability to open disk images and preview files and folders inside, before image restoration. Users can even copy specific files or folders from the image to another location.
To restore accidentally deleted files, use Active@ Disk Image to make an image of the disk (snapshot), from which users can later try to restore deleted files without the risk of overwriting important data on original disk. If the disk shows bad clusters, users can effectively stop this process to preserve whatever is still readable as an image, and try to restore datalater.
The following are some of the features of Active@ Disk Image:
Can be run from a DOS bootable floppy or CD-ROM
Displays complete HDD, partition, and disk image information
Creates compressed and noncompressed raw images for the physical drive (HDD)
Restores compressed and noncompressed raw images back to the physical drive or partition
Creates compressed data images for any partition on the HDD
Displays contents of any physical sector on the drive or within the disk image
Allows viewing of all filesand folders inside disk image before restoration using the preview mode
Allows the copying of specific files and folders from the image to another location
Supports IDE/ATA/SCSI/USB drives
Supports large (more than 128 GB) hard disk drives and partitions
Supports FAT12, FAT16, FAT32, NTFS, and NTFS5 file systems
Supports partitions created in MS-DOS, Windows 95/98/ME/NT/2000/XP/2003/XP Professional x64/XP Home x64/2003/2003 Server x64
Figures 4-53 and 4-54 are screenshots from Active@ Disk Image, showing anexample of the recovery process after scanning unallocated space on the hard drive.
Tool: Active@ Partition Recovery
Active@ Partition Recovery for DOS can recover deleted partitions only if its location on a hard disk drive has not already been overwritten. If an MBR backup was created by using Active@ Partition Recovery, users can always restore MBR and partition information.
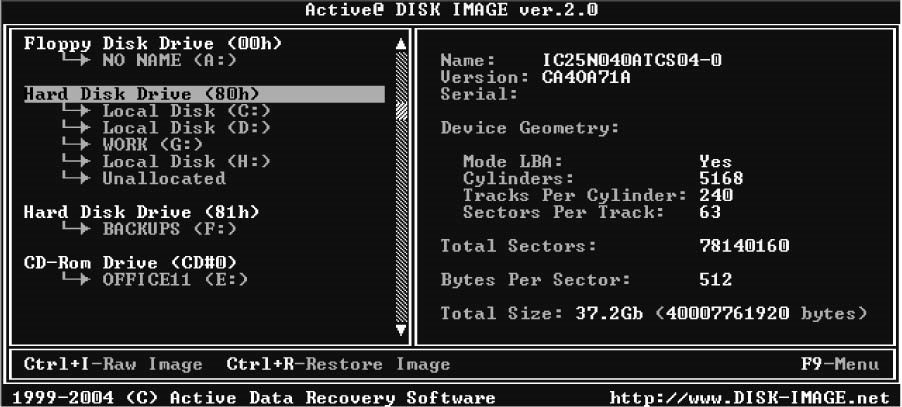
_Source:_www.disk-image.net. Accessed 2/2007.
Figure 4-53Using Active@ Disk Image, a user can look at the properties of all the storage devices in a system.
Source:http://www.disk-image.net.Accessed 2/2007.
Figure 4-54Users can create images of particular partitions using Active@ Disk Image.
Active@ Partition Recovery for Windows will help if a nonsystem partition is lost (i.e., users can boot Windows, install, and run the software from under the Windows operating system to recover deleted or damaged partitions located on data volumes). BOOT.INI is corrected automatically (if needed) to keep the system bootable, and damaged volume boot sectors are corrected to maintain integrity of the partition. The software can repair the MBR and delete invalid partitions. Active@ Partition Recovery can:
Recover deleted partitions (FAT, FAT32, and NTFS)
Restore deleted FAT and NTFS logical drives
Create drive images for backup purposes
Scan hard drives and detect deleted FAT and NTFS partitions and/or logical drives
Preview filesand folders on deleted partition or drive, to recover proper data
Backup MBR (master boot record), partition table, and boot sectors
Restore MBRs, partition tables, and boot sectors from backup if damaged
Undelete partitions (primary and extended)
Be stored on a bootable floppy disk due to its small size
Display complete physical and logical drive information
Be used with ease: controlled by only arrow, Enter, and Esc keys
Figures 4-55 and 4-56 show screenshots from Active@ Partition Recovery.
Tool: DiskInternals Partition Recovery
DiskInternals Partition Recovery is intended for users who need to recover data or lost partitions. DiskInternals Partition Recovery includes a step-by-step wizard and requires no special skills to operate. This product includes DiskInternals NTFS and DiskInternals FAT recovery products.
DiskInternals Partition Recovery recovers data from damaged, deleted, lost, or reformatted partitions, image files, or important documents. The software includes a Partition Recovery Wizard, NTFS Recovery Wizard, and a FAT Recovery Wizard.
DiskInternals Partition Recovery supports a multitude of file systems, including:
FAT12, FAT16, FAT32, and VFAT
NTFS, NTFS4, and NTFS5
The tool scans every disk sector for recoverable data. DiskInternals Partition Recovery repairs data from virtual disks, and it does not matter if these files or folders were deleted before recovery or not. Figure 4-57 shows a screenshot from DiskInternals Partition Recovery.
_Source:_www.partition-recovery.com. Accessed 2/2007.
Figure 4-55Active@ Partition Recovery can scan a drive to find deleted partitions.
_Source:_www.partition-recovery.com. Accessed 2/2007.
Figure 4-56This screenshot shows that the software will create an image of the deleted partition on the selected drive.
Tool: GetDataBack
GetDataBack will recover data from a lost, deleted, damaged, formatted or reformatted, or crashed hard drive’s partition table, boot record, FAT/MFT, or root directory. GetDataBack also recovers files over a user’s local network or over a serial cable; this feature enables the user to run GetDataBack on one computer while accessing the drives of another computer. It also recovers data from removable drives and logical drives.
GetDataBack supports Unicode, which allows the recovery of files with names encoded in nonstandard character sets. This includes all Unicode character sets, such as Japanese, Chinese, Korean, Russian, and Greek. It is recommended to perform the data recovery on an NT/XP computer because Windows 9x/ME does not fully support Unicode.
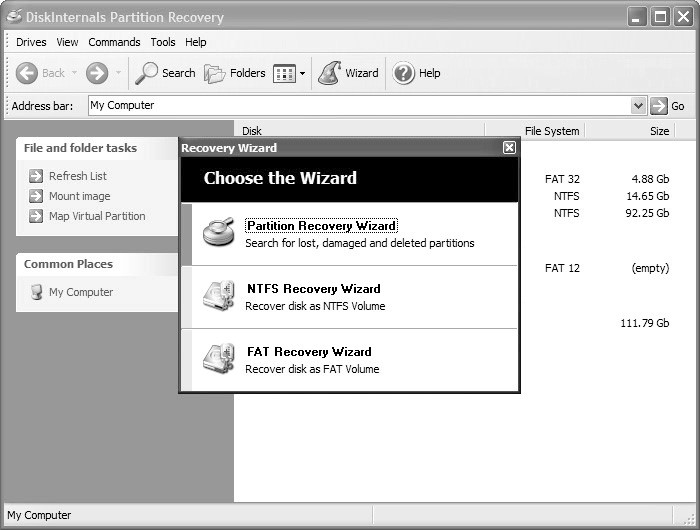
Figure 4-57This image shows that the software will create an image of the deleted partition on the selected drive.
GetDataBack can be used for FAT and NTFS to recover files from drives with their respective file system.
GetDataBack for FAT and NTFS can run under Windows 95/98/ME/NT/2000/XP.
Figures 4-58 and 4-59 show screenshots from GetDataBack for NTFS and FAT.
Tool: Deleted NTFSPartition Data Recovery
Deleted NTFS Data Recovery software has been designed and developed to recover data from Windows NT/2000/2003/XP operating systems. It retrieves data files and folders lost due to formatted/damaged/overwritten/ deleted/corrupted partitions from NTFS-basedoperating systems, such as Windows NT/2000/XP/2003, from the hard disk. It also recovers data from storage media such as Zip drives, digital cameras, Pen drives, key chain drives, Memory Cards, and Flash memory.
The software provides an effective graphicaluser interface with built-in user-friendly support, providing the fastest and safest data retrieval facilities. The software is also helpful in computer forensics. The following are some of the key features of Deleted NTFS Partition Data Recovery:
Is easy, safe, read-only, and nondestructive
Recovers data lost due to overwritten, damaged, or corrupted partitions in all logical drives or if the user’s drive is accidentally formatted
Recovers data from previously existing partitions in the user’s drive and from bad sectors affected by storage media or drives
Recognizes and keeps long file names when restoring files and folders.
Provides recovery of deleted files and folders, even after the Recycle Bin has been emptied, or use of the Shift+Delete key combination has happened
Recovers data even if the “Drive Not Formatted” message is displayed on the user’s computer screen
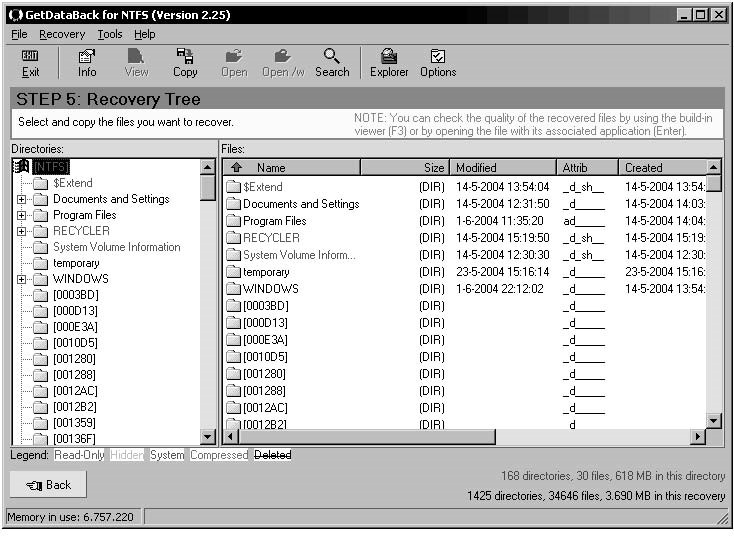
Figure4-58This image shows GetDataBack for an NTFS drive. System files are shown in red.
Tool: Partition Table Doctor
The Partition Table Doctor will recover a user’s data if the partition table, or boot sector, on a hard disk is lost or damaged due to a virusattack, software failure, Fdisk or PartitionMagic misapplication, and so on. The Partition Table Doctor can recover partitions.
The Partition Table Doctor only modifies a partition table or boot sector, which means that the software will never attempt towrite to the data area of the drive that a user wants to recover.
Partition Recovery tools provide a graphical user interface (GUI), and it is easy to create an emergency floppy disk or bootable CD. Though the software is easy to follow, advanced users canimprove the results by analyzing the reports, examining the file system details, and selecting specific sectors to modify.
Figure 4-60 shows a screenshot from Partition Table Doctor.
Tool: Recover It All!
Recover It All! recovers and restores deleted or damaged partitions or boot sectors. It is designed for FAT16, FAT32, and Windows 2000. The software performs all functions, including partition recovery in memory first, eliminating the need for recovery atthe file level.
The following are some of the features of Recover It All!:
Recovers data and partition tables lost due to formatting, Fdisk, virus attack, deletion, and many other scenarios
Provides true 32-bit recovery without truncating files, and keepslong file names intact
Works with most RAIDs
Recovers entire directories
Repairs partitions and boot sectors even from virus attacks or accidental use of Fdisk, and restores lost partitions and corrupt partitions
Is safe because all recovery functions areperformed in memory first
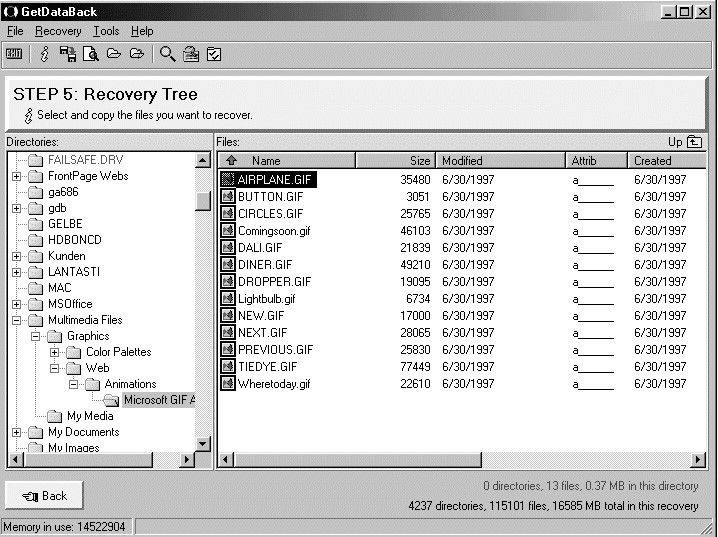
Figure 4-59This image shows GetDataBack for FAT. Files to the right can be recovered individually.
Is easy to use, powerful, and quick
Recovers deleted files
Tool: Scaven
Scaven is a microtool for data recovery. It was designedto perform unattended multisession searches through large hard drives. It records the position of matches found to the output text file in a sector: offset: match format (fixed size column).
Scaven is an effective tool and time saver in recovering data from:
Files permanently deleted
Files lost through overwrite
Accidentally formatted drives
Drives with damaged MBR/lost partitions
Drives with corrupted FATs
Drives that have developed bad sectors
The following are some of the features of Scaven:
Performs a multiple-string search in a single pass
Works with any size LBA hard drive (up to 138 GB)
Automatically detects drive geometry (CHS and LBA)
Can access drives invisible on DOS
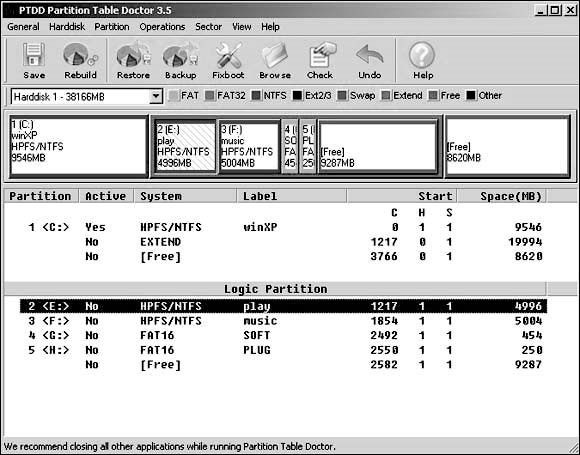
Figure 4-60This image shows Partition Table Doctor. Notice that different partitions can be recovered at the same time.
Fits on a single floppy and leaves plenty of room (size
Records the position of matches found as sector number: offset
Records the location of bad sectors as a sector number
Uses standard text files for input/output
Was written in a plain assembler for the sake of size/speed
Tool: TestDisk
TestDisk is free data-recovery software. It was primarily designed to help recover lost partitions and/or make nonbooting disks bootable when these symptoms are caused by faulty software, certain types of viruses, or human error (such as accidentally deleting the partition table). TestDisk supports the following operating systems:
DOS (either real or in a Windows 9_x_DOS box)
Windows (NT4, 2000, XP, 2003)
Linux
FreeBSD, NetBSD, and OpenBSD
SunOS
Mac OS
TestDisk can find lost partitions for the following filesystems:
BeFS (BeOS)
BSD disklabel (FreeBSD/OpenBSD/Net BSD)
CramFS, Compressed File System
DOS/Windows FAT12, FAT16, and FAT32
HFS and HFS
JFS, IBM’s Journaled File System
Linux ext2 and ext3
Linux Raid
TestDisk queries the BIOS or the OS in order to find the hard disks and their characteristics (LBA size and CHS geometry). TestDisk does a quick check of the user’s disk’s structure, and compares it with the user’s partition table for entry errors. If the partition table has entry errors, TestDisk can repair them. If the user has missing partitions, or a completely empty partition table, TestDisk can search for partitions and create a new table, or even a new MBR, if necessary.
However, it is up to the user to look over the list of possible partitions foundby TestDisk and to select the one(s) that were being used just before the drive failed to boot or the partition(s) were lost. In some cases, especially after initiating a detailed search for lost partitions, TestDisk may show partition data that is simplythe remnants of a partition that had been deleted and overwritten long ago.
TestDisk has features for both novices and experts. For those who know little or nothing about data recovery techniques, TestDisk can be used to collect detailed information abouta nonbooting drive, which can then be sent to a tech for further analysis. Those more familiar with such procedures should find TestDisk a handy tool in performing on-site recovery.
Figures 4-61, 4-62, and 4-63 show screenshots from TestDisk.
Figure 4-61These images show the TestDisk application being used to recover lost partitions.
Figures 4-62These images show the TestDisk application being used to recover lost partitions.
Figures 4-63These images show the TestDisk application beingused to recover lost partitions.
Chapter Summary
■In Windows, files in the Recycle Bin are stored in the C:\RECYCLED folder on FAT file systems, and in the C:\RECYCLER folder on NTFS file systems.
■Damaged files in the Recycled folder do not appear in the Recycle Bin.
■In Linux, files that are deleted using/bin/rmremain on the disk.
■Files or folders deleted from removable media are not stored in the Recycle Bin.
■Deleting a partition on a dynamic disk can delete all dynamic volumes on the disk, thus leaving the disk in a corrupt state.
■Recovery of deleted partitions is the process by which the investigator evaluates and extracts deleted partitions.
Review Questions
- What happens when a file is deleted in Windows?
- How does the Recycle Bin work in Windows?
- Why are the Recycle Bin folders differently named on NTFS and FAT file systems?
Explain the following:
Damaged or deleted INFO2 file
Damaged Recycled folder
- Describe the data recovery process in Linux.
- How can you delete a partition using the command line?
- Write down the steps to delete a partition using the Windows interface.
- Name three events that can cause data loss in files, folders, or file structures.
- Which tools recover deleted files in Linux?
- Which tool would you use to recover a BeOS formatted partition? Why?
Review Questions
Hands-On Projects
 Run the R-Linux tool and recover deleted files from Linux.
Run the R-Linux tool and recover deleted files from Linux.Download Recover My Files fromhttp://www.recovermyfiles.com/,run, and see the result.
Run the CDRoller tool and try to recover deleted data from a CD and DVD.
Run the Partition Table Doctor tool and recover deleted partitions.
Run the PC Inspector Smart Recovery tool and try to recover the deleted images from a
digital camera.
This page intentionally left blank
Objectives
After completing this chapter, youshould be able to:
Recognize graphic image files
Explain data compression
Locate and recover graphic image files
Analyze graphic image file headers
Reconstruct file fragments
Identify and use tools for viewing graphic images
Understand steganography in graphic image files
Perform steganalysis in graphic image files
Identify and use graphic image file forensic tools
Key Terms

Image**File**Forensics
Chapter
5
Bitmap (BMP)a raster-based image format closely associated with Microsoft and many Microsoft image programs save files as BMPs by default. BMP files typically do not compress well, and so are larger than other compressed formats.
CMYKa color model that stands forCyan,Magenta,Yellow, andKey (black); also known as the fourcolor model, CMYK works by subtracting some colors from white (all colors), leaving the resulting hue. CMYK is a model used by commercial printers and is capable of rendering millions of colors.
Carving_see_salvaging
Ditheringa method used to create the illusion of greater color depth by blending a smaller number of colored dots together
Graphic Interchange Format (GIF)an 8-bit RGB bitmap format for images with up to 256 distinct colors per frame
5-1
Grayscaleimages in grayscale only include intensity information. Only shades of black and white (or gray) are rendered.
Huffman Coding Algorithma variable-to-fixed lossless compression algorithm
Indexed colora color system in which every color is coded to a specific number (or index)
Interlacinga mechanism that makes images appear faster on-screen by first displaying a low-resolution version of the image and gradually showing the full version
Joint Photographic Experts Group (JPEG) file formata raster image compression format
Lempel-Ziv-Welch (LZW) algorithma variable-to-fixed compression algorithm used in GIF files
Limited color paletteeach color in the GIF color table is described in RGB values, with each value having a range between zero and 255
Linear discriminant ana**lysis**a method of classification by comparing two or more samples; in Stegdetect software, it identifies the steganography by comparing the two images.
Lossless compressiondescribes a compression algorithm that maintains data integrity
Lossy compressi**on**describes a compression algorithm that does not maintain data integrity, leading to possible loss of data
Pixelshort forpicture element, a pixel is a single point in a graphic image. On monitors, pixels are arranged in rows and columns to displaypictures and text. To display a picture, pixels on the screen are closely connected.
Portable Network Graphics (PNG)a lossless, well-compressed format for displaying raster graphics; PNGs were created to replace GIFs. They support alpha channels and generally have smaller file sizes than the older GIF format.
RGB (Red-Green-Blue) color modelthe representation of colors based on combinations of red, green, and blue; this model is generally used in monitors, cameras, and televisions and is less likely in print production.
Raster imagea file in which the information is converted into pixels; raster images are nonscalable.Salvagingreconstructing an image file that was accidentally or deliberately destroyed using file fragments; synonymous withcarvi__ng
Steganalysisretrieving information hidden in image files
Tagged Image File Format (TIFF)a flexible raster image file format, commonly used in desktop publishing and photography, that allows for multiple modes of compression and color depths
Vector imageimages in which information is stored as mathematical expressions rather than pixels; because the calculations can be done for any given space, vector images are scalable.
Vector quantizationa lossy data compression technique in which vectors are used to compress the file
Zone Information Protocol (ZIP)a method of compressing computer data or files to save space
Case Example 1
Assistant Attorney General Alice S. Fisher, of the Criminal Division, and U.S. Attorney Chuck Rosenberg, of the Eastern District of Virginia, announced in Federal Court on September 8, 2006, the sentencing of Nathan L. Peterson, of Antelope Acres, California, to 87 months imprisonment.
Peterson was accused of stealing intellectual property of various software companies, such as Adobe Systems Inc., Macromedia Inc., Microsoft Corporation, Sonic Solutions, and Symantec Corporation. Peterson ran a Web site,http://www.ibackups.netand sold illegal copies of copyrighted software products at a price lower than the suggested retail price. The software was reproduced and distributed through an instantaneous computer download of an electronic copy, and/or by shipment through the mail onCDs.
As of February 2005, Peterson had made illegal sales of over $5.4 million of copyrighted software, which resulted in a loss of approximately $20 million to the owners. With this money, Peterson led a lavish lifestyle that included multiple homes and aboat. He also maintained numerous assets, such as bank accounts and a garage full of stylish cars.
After receiving complaints from copyright holders, an FBI undercover agent, posing as a customer, made purchases from the Web site. As a result of this investigation, the Web site was discontinued in February 2005. On December 13 of the same year, Peterson pleaded guilty to two counts of criminal copyright infringement for selling pirated software. The court also forfeited the proceeds of his illegal conductand ordered him to pay restitution of more than $5.4 million.
Case Example 2
Most e-mail applications include a spam-detection component to identify keywords and strings of language contained in known spam. This reduces unwanted advertisements in the end users’ mailboxes. To combat this, some spammers embed spammed ads in graphics files, so the messages go through undetected by the software and land in users’ mailboxes. This has triggered the use of images in spam by spammers around the globe. Spammers target zombie machines to send images spam to various recipients around the globe.
The antispam e-mail vendor Vircom, released an upgrade to its antispam engine. Modus 4.35, released in May 2006, has the capability to detect image-based spam with a 95% successrate. Most of the antispam engines available in the world do not have protection for image spam. Modus 4.35 can detect patterns and keywords within the image and return the information to the e-mail software to classify or not classify the e-mail as junk.
Introduction to Image File Forensics
This chapter covers the various methods in which a forensic investigator can go about recovering graphics files. This chapter mainly deals with understanding the basic concept of recovering graphics files. The chapter also highlights the various image recovery, steganalysis, and viewing tools that are used and the salient features of these tools.
Introduction to Image Files
An image is an artifact that reproduces the likeness of some object. Photographs, faxes, photocopies, reflections, and views from microscopes and telescopes are all images. Computer forensics, with regard to recovering graphic image files, is of prime importance to many corporate organizations. A large number of computer forensics investigations include graphic images, typically downloaded from the Internet and sent through e-mails by employees of the company. In order to examine and recover these deleted files, a computer investigator needs to know the basics of image file graphics, including:
Features of graphic image files
Common image file formats
Compression methods used by image files
Computer forensic investigators need to identify image file fragments and repair damaged image file headers. There are many tools in a computer forensic investigator’s arsenal to recover image files.Examiners also give importance to the process of steganography, in which data is hidden inside files and images. They also analyze image file headers from unknown image file formats, a painstaking process. It is important to properly recover image files inorder to use the hidden data as evidence.
There are four different kinds that can be used in an image. TheCMYKscale is best for print production. The colors used in a CMYK image are percentages of cyan (blue), magenta (reddish-pink), yellow, and black.These result in millions of possible color combinations. Another scale isRGB(red, green, blue), which results in 256 possible colors.Indexed colorcontains the colors in RGB, but only the colors used by the image. Images can also begrayscale, which only shows shades of the colors black and white.
There are several different kinds of image file formats. Image formats can differ in color, ease of use, and size during the reproduction process. They also have specific internal structures that are importantto an investigator analyzing or repairing files.
Images can be broadly categorized into vector images and raster images.
Understanding Vector Images
Vector imagesuse geometrical shapes and primitives, such as points, lines, curves, and polygons, based upon mathematical equations, in order to represent images in a computer. Because each image is basically an equation, it is easy to move, scale, rotate, and fill a completed image. The file size of a vector image is relatively small, because it stores only the mathematical calculations, not the images, of the pictures included. Vector images can be easily embedded into another program without bloating the host file size.
It is possible to enlarge a vector image without affecting the quality of the image; the graphic program simply multiplies the existing pixels on the image file by the magnification you select. When investigators examine images in forensic investigations, they can enlarge elements greatly to examine them better.
Vector files can be converted into raster files, as long as there are no other images, such as digital photography or scanned photographs, in the vector file format.
Copyright © by

All rights reserved.
Reproduction is strictly prohibited
Figure 5-1A metafile contains both vector and raster elements.
Understanding Raster Images
Unlike vector images,raster imagesare composed of a collection of pixels. Apixelis a single point in a graphic image. The quality of raster images is specified by the number of pixels present and information present in each pixel. Because the number of pixels is fixed when the image is set, if you enlarge the image, it loses its quality. (Imagine a photograph. When you enlarge the photograph, the picture becomes blurry, and it is harder to see specific elements.)
In every raster image, pixels are associated with three 8-bit color values (0–255 values) that define the amount of each of the three colors (red, green, and blue) in each pixel. Images that have less color require less information per pixel. Images that have only black and white pixels contain only a single bit for each piece of information.
File formats such as BMP, JPEG, and GIF are examples of the raster image. In a raster image, the pixels are arranged in rows that make the image file easier to print.When any type of image is printed, it has to be converted to a raster image first to print the pixels line by line, in order to finish the complete set of pixels.
Metafile Graphics
Metafile graphics include both raster and vector images. When a metafile isenlarged, some parts of the image show a lower resolution, thereby giving the image a shady appearance. An example of a metafile is a photograph of an image file with arrows superimposed on the photograph. If a metafile is enlarged, the area created witha raster format loses some resolution, and the quality of the file will be low. However, the formatted area of the vector will remain sharp and clear without any loss to compression. Figure 5-1 shows a standard metafile graphic.
Understanding Image File Formats
A file format is a way to encode information to be stored in a computer file. Graphical editors that can save image file formats include Microsoft Paint, Macromedia Freehand, Adobe Photoshop, and GIMP for Linux. Many of these graphic editors are especially optimized for one particular file format. For example, Microsoft Paint
| File Format | File Extension |
|---|---|
| Graphics Interchange Format (GIF) | .gif |
| Joint Photographic Experts Group (JPEG) | .jpg |
| Tagged Image File Format (TIFF) | .tif |
| Windows Bitmap (BMP) | .bmp |
| JPEG 2000 | .jp2 |
| Portable Network Graphics (PNG) | .png |
Table 5-1This table shows popular standard image formats and file extensions
can be used to work on only bitmap images. Macromedia Freehand generates and reads vector shapes. Forensic investigators usually use Adobe Photoshop, as it works on both bitmap images as well as vector graphics.
Many graphic-editing applications allow theexaminer to create and save files in one or more of the standard image file formats. Table 5-1 shows commonly used image file formats.
GIF (Graphics Interchange Format)
GIFis a file format that contains 8 bits per pixel and displays 256 colors per frame.CompuServe generated the GIF format in 1987. GIF uses lossless data compression techniques, which maintain the visual quality of the image.
Features of GIF are as follows:
Limited color palette: GIF image file consists of a color table, which stores the image consisting of 2, 4, 8, 16, 32, 64, 128, or 256 colors. Each color in this table contains an RGB (Red, Green, Blue) value within a range of zero to 255. GIF does not support the CMYK (Cyan, Magenta, Yellow, Key (Black)) color combination.
Dithering: The size of the GIF file depends on the number of colors used. For example, if 256 colors are used, then it becomes 9.5 Kb. For 32 colors, it becomes 4.4 Kb, and for 16 colors, it is 1.9 Kb.Ditheringis used to limit the size file. It combines smaller color dots together to form the grater color depth. Dithering adds noise to the image and it decreases the sharpness of the image.
LZW compression: GIF uses the LZW (Lempel-Ziv-Welch) compression technique. This lossless data compression algorithm combinesthe string of same byte values into the single code word. It reduces the size of the 8-bit pixel data by about 40% or greater.
Interlacing: GIF has a Web-specific feature known asinterlacing. It helps to display the image quickly on the screen. This feature first shows the low-resolution version of the image and gradually displays the full version of the image. Table 5-2 shows the pattern of the lines of pixels displayed in an interlaced GIF.
| Pass | Interval | Line numbers |
|---|---|---|
| 1 | 8 | 1, 9, 17, 25, 33. . . |
| 2 | 8 | 5, 13, 21, 29, 37. . . |
| 3 | 4 | 3, 7, 11, 15, 19. . . |
| 4 | 2 | (all even rows) 2, 4, 6, 8, 10. . . |
Table 5-2This table shows the pattern of pixels displayed in an interlaced GIF
GIF File StructureA GIF file, consists of the following elements:
- Header: The GIF file starts with a 6-byte header, which identifies the type of GIF image. The first three bytes identify the file as the GIF format. The second three bytes tell the version of GIF format: 87a or 89a.
typedef struct _GifHeader
{
// Header
BYTE Signature[3]; / Header Signature (always “GIF”) /
BYTE Version[3]; / GIF format version (“87a” or “89a”) /
}
Logical screen descriptor: The logical screen descriptor contains data about the screen and color, which helps to display the GIF image. It describes the ScreenHeight and ScreenWidth fields, as well as screen resolution.
Global color table: The logical screen descriptor is followed by the global color table. The size of the table depends upon the number of colors chosen for the image. All GIF images include three colors: red, green, and blue. There are 256 possible combinations of these three colors that can create a spectrum of colors accessible to the user. When saving an image, the user selects amaximum amount of colors in the final image, always in the power of two (i.e., 2, 4, 8, 16, 32 . . . 256). The more colors selected, the larger the file.
typedef struct _GifColorTable
{
BYTE Red; / Red Color Element/
BYTE Green; / Green Color Element /
BYTE Blue; / Blue Color Element /
} GIF COLORTABLE;
- Local image descriptor: Each image has a local image descriptor before the image data. The structure of the local image descriptor is as follows:
typedef struct _GifImageDescriptor
{
BYTE Separator; / Image Descriptor identifier /
WORD Left; / X position of image on the display /
WORD Top; / Y position of image on the display /
WORD Width; / Width of the image in pixels /
WORD Height; / Height of the image in pixels /
BYTE Packed; / Image and Color Table Data Information /
} GIFIMGDESC;
The separator indicates the start of the image descriptor data block. The left and top are the coordinates of upper-left corner pixel of the image. These coordinates are considered (0, 0). The width and height indicates the image size in the pixels. The BYTE Packed Image and Color Table Data Information includes the following five subfields:
Bit 0: local color table flag
Bit 1: interlace flag
Bit 2: sort flag
Bit 3–4: reserved
Bit 5–7: size of local color table entry
Local color table: The local image descriptor is followed by the local color table. It has the same format as the global color table. Every element consists of the three colors: red, green, and blue.
typedef struct _GifColorTable
{
BYTE Red; / Red Color Element /
BYTE Green; / Green Color Element /
BYTE Blue; / Blue Color Element /
} GIFCOLORTABLE;
| Illegal nested table : HeaderLogical Screen DescriptorGlobal Color TableLocal Image DescriptorLocal Color TableImage DataLocal Image DescriptorLocal Color TableImage Data……Local Image DescriptorLocal Color TableImage DataTrailer | |
|---|---|
Header and Color
Table Information
Image 1
Image 2
Image n
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-2 Notice that there are several images in this GIF, but information about each image is contained in the single header.
- Image data: The image data in the GIF file is compressed by using the LZW compression algorithm. Data is encoded in a continuous stream, read from start to finish. It stores the data in a series of data subblocks. Each data block starts with the count byte. The count byte is between one and 255 and shows the number of data bytes in the subblock.
Figure 5-2 shows a GIF file structure.
There are currently two versions of GIF:
GIF 87a: The first version of GIF was generated in 1987. It uses the LZW file compression technique, and supports features such as interlacing, 256-color palettes, and multiple image storage.
GIF 89a: This version was generated in 1989. It supports features like background transparency, delay times, and image replacement parameters. These features are useful for storing multiple images as animations.
JPEG (Joint Photographic Experts Group)
JPEGis a commonly used method to compress photographic images. It uses a compression algorithm to minimize the size of the file without affecting the quality of the image.
The JPEG file format is useful for the following applications: digital cinema, digital photography, printing and scanning, document imaging, medical imaging, wireless imaging, remote sensing and GIS, image archives and databases, facsimiles, surveillance, and prepress. JPEG compression happens in four phases:
First, the JPEG algorithm divides the image in separate blocks of 88 pixels.
The compression algorithm then applies a discrete cosine transform (DCT) for the whole image. DCT exchanges the values of images for every pixel in each block to an 88 matrix of DCT coefficients.
N ext, the compression algorithm checks the JPEG image quality asked for by the user, and then calculates two separate tables of quantization constants, one for luminance and one for chrominance. These constants quantize the DCT coefficients.
The last step is to compress these coefficients using a Huffman or arithmetic coding scheme.
JPEG File StructureThe first bits of a file identify the type of file. Every JPEG file starts with binary value 0xffd8 (SOI—start of image) and ends with binary value 0xffd9 (EOI—end of image),so ffd8 (the 0x is implied) shows that it is a JPEG file when viewed with a hex editor. A JPEG bit-stream contains a sequence of data chunks, or segments, and every chunk starts with a marker value. The basic format of a segment is as follows is followedby the 16-bit integer value that determines the file size value. The most significant byte of the marker (the left-most bit) is 0xff. The lower byte of the marker determines the type of marker.
The basic format of a segment is as follows:
0xffmarker number (1 byte)data size (2 bytes) data (_n_bytes)
For example, for the marker FF E1 00 0E, the marker (0xFFE1) has 0x000E (which equals 14) bytes of data.
But the data size 14 includes the data size descriptor (2 bytes); thus, only 12 bytes of data followafter 0x000E. Figure 5-3 shows a JPEG file structure. Figure 5-4 shows possible kinds of segment markers in JPEGs.
JPEG 2000
JPEG 2000 is the new version of JPEG compression from the JPEG committee. JPEG 2000 employs wavelet technology so images can be better compressed without affecting quality of an image.
JPEG 2000 Features
JPEG 2000 offers a 20% improvement in compression efficiency over the current JPEG format.
It employs wavelet technology with the existing compression algorithm. Wavelet technology gives improved image quality and better compression.
It offers lossless compression mode as an option. The size of the losslessJPEG 2000 image will be half the original image.
This compression was developed mainly for use on the Internet.
It can handle RGB, LAB, and CMYK formats with up to 256 channels of information.
JPEG File Structure
End of Image
EOI
xFF 0xD9
0
Segments
Start of image
SOI
xFF 0xD8
0
Description
Name
Contents
JPEG Image
Segment data
Segment size (2 bytes) excl. marker
Segment marker (2 bytes)
Description
JPEG Segments
Copyright © by

All rights reserved. Reproduction is strictly prohibited
Figure 5-3 A JPEG image is divided into segments.
| Some JPEG segment markers | ||
|---|---|---|
| Contents | Name | Description |
| 0xFF 0xEo | APP0 | Application marker (in every JPEG file) |
| 0xFF 0xDB | DQT | Quantization Table |
| 0xFF 0xC0 | SOF0 | Start of frame |
| 0xFF 0xC4 | DHT | Define Huffman Table |
| 0xFF 0xDA | SOS | Start of scan |
| 0xFF 0xED | APP14 | This is the marker where Photoshop stores its information |
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-4 A JPEG segment must contain an application marker, but may also contain any or all of the other information. The SOI marker and the EOI marker have no data following, but the other markers have data with them.
BMP (Bitmap) File
TheBMP (Bitmap)file format is a standard file format for a Windows DIB (Device Independent Bitmap) file. Microsoft developed this format to store bitmap files in DIB format so that on any kind of display, Windows can display it. Bitmap images can be animated. The size and color of these images can vary from 1 bit per pixel (black and white) to 24-bit color (16.7 million colors).
BMP File StructureEvery bitmap file contains the following data structure:
File header: The first part of the header that includes the data about the type, size, and layout of a file
Information header: A header component that contains the dimensions, compression type, and color format for the bitmap
The RGBQUAD array: A color table that comprises the array of elements equal to the colors present in the bitmap; this color table does not support bitmaps with 24 color bits, as each pixel is represented by 24-bit RGB values in the actual bitmap.
Image data: The array of bytes that contains bitmap image data; image data comprises color and shading information for each pixel.
Figure 5-5 shows the file structure of a bitmap file.
PNG (Portable Network Graphics)
PNGis a lossless image format intended to replace the GIF and TIFF formats. PNG improves the GIF file format and replaces it with the image file format. It is copyright- and license-free. PNG file format supports:
24-bit true color
Transparency—both normal and alpha channel
BMP
| Header |
|---|
| Info Header |
| RGBQUAD array |
| Image Data |
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-5 Bitmaps have a very basic structure for image information.
PNG File Structure
PNG File Signature:
PNG file signature shows that the remainder of a file has a single PNG image.
The images are comprised of a series of chunks, starting with an IHDR chunk and ending with an IEND chunk.
Chunk Layout
Chunk layout follows the header.
Each chunk in a set suggests some information about the image.
Every chunk has a header specifying the size and type of chunk.
Every chunk consists of four parts:
Length: a 4-byte unsigned integer that gives the number of bytes present in the chunk’s data field
_Chunk_type: a 4-byte chunk type code
Chunk data: the databytes appropriate to the chunk type, if any; this field can be of zero length.
CRC (Cyclic Redundancy Check): a 4-byte CRC calculated on the preceding bytes in the chunk; it includes the chunk type code and chunk data fields, but not the length field.
Tagged Image File Format (TIFF)
TIFFis a raster file format for digital images, created by Aldus, now controlled by Adobe. It was originally intended for use with PostScript printing. The main advantage of the TIFF file is that it can contain several image formats in a file. Tags are used to describe how the data should be represented in the final image.
The TIFF file can be used as a container for JPEG files. The file extension is .tif. TIFF supports both lossy and lossless compression algorithms; the lossless algorithms include PackBits and the LZW algorithm. It has the following features:
Extendability: This format can add new images and new information about the images without invalidating older image types.
Portability: TIFF is flexible and platform-independent.
Revisability: It was designed to efficiently exchange image information. It is also used as a native internal format for image editing applications.
TIFF File Structure
TIFF files are composed of three data structures:
Image file header (IFH): Theimage file header is the first data structure in the TIFF.
This 8-byte image file header is fixed at the location offset zero. The first two bytes contain the informa-tion about byte ordering, which is very important when the file is created. It either contains two bytes of “II” (hex 4949) for an Intel-created image file, or “MM” (hex 4D4D), for a Motorola-created image file.
Versions in the IFH consist of the decimal value of 4210. It verifies that the present file is TIFF or not. This number remains constant, but if someone changes it, it means the TIFF file format has been changed and TIFF reader becomes unable to read that file.
The last four bytes in the IFH give the number of bits from the start of the file to the image file direc-tory structure.
Notice that nothing about the image itself is included in the IFH. All image information is stored in the image file directory.
Image file directory (IFD): The IFD holds all the information about an image. If the file contains more than one IFD, there is more than one image in the file.
Each IFD entry consists of: a 16-bit header that tells the number of included tags, and all the direc-tory entries (DEs) for a given image. Each DE is 12 bytes long.
After all DEs have been listed, the remaining bytes include the offset to the next IFD. If it is the last IFD in the file, then the storage location of the offset is four bytes of zeros.
Directory entry (DE): The DE is contained in the IFD. The DE is 12 bytes divided into four parts.
The first part is the tag field; it defines the raster data present in the TIFF files.
The next field is the type field, which specifies the data type of the image parameter, each having the integer number.
Length is the third field; it specifies the number of items of particular data types used. This value represents the number of data units in this particular entry; it does not represent the number of bytes needed to store the entry.
The last part of a DE contains the offset of the file to actual data related to the tag.
Figure 5-6 shows the file structure of a TIFF.
ZIP (Zone Information Protocol)
ZIP (Zone Information Protocol)is a method of compressing files designed by Phil Katz. Tools such as WinZip and WinRAR use this protocol to compress files. In ZIP, several files may be gathered together and compressed into a single “archive” file. A zipped file must be uncompressed in order to be used. Zip files can contain any file, such as text files, pictures, executables, music, and so on, and can be password protected for security purposes.
Zip files contain all the information about a zippedfile, such as the name of the file, its path, on which data it is created, related time, and last modification. There are several advantages to Zip files:
It compresses a number of files into a single file, which reduces the space on the hard disk.
Zip files can be transmitted faster over a network.
Several files can be transferred at once.
Data Compression in Image Files
Image file formats, like bitmaps, cannot compress data without the help of some compression tools. Some of the most popular imagefile formats use the Graphics Interchange Format (GIF) and Joint Photographic Experts
Group (JPEG) to compress data. This saves disk space and reduces the time it would take to transfer the image
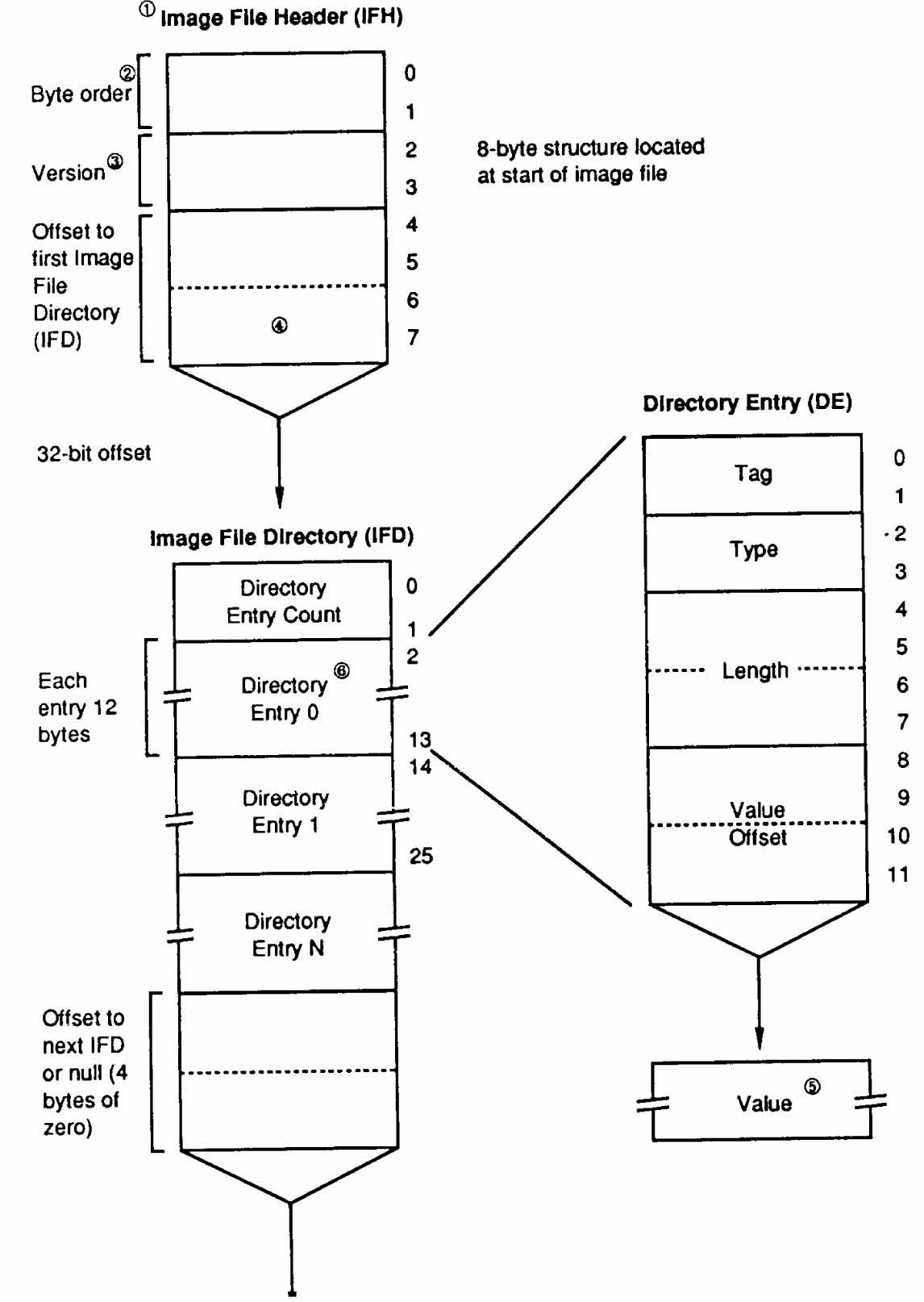
Source:http://www.ee.cooper.edu/courses/course_pages/past_courses/EE458/TIFF/.Accessed 2/2007.
Figure 5-6 TIFFs include an image file header and image file directory. Notice that the DE is part of the image file directory.
from one system to another. Compression tools make the data compact and reduce the file size so drive space can be saved.
Data compression is a procedure that makes use of multifaceted algorithms used to reduce the file size. Typically, coding the datafrom a larger image to another smaller one is known as data compression. Vector quantization is similar to data compression. A vector image makes use of a mathematical equation that is similar to rounding up decimal values to eliminate unnecessary data.
Data compression is of interest in computer forensics because of its advantages in data processing, such as the cost savings and large volume of data manipulated in many business applications. The genre of local redundancy present in business data files comprise runs of zeros in numeric fields, series of blanks in alphanumeric fields, and fields present in some records and null in others.
Understanding File Compression
Most files use the same information, meaning they repeat the same sentences or words many times. File compression programs simply get rid of the redundancy. The file compression techniques list the information that is repeated, assign a code or number to each unique bit of information, and use the code to compress the information.
In this technique, repeated words are selected and stored into the dictionary. This dictionary consists of the words and numbers assigned to them. So when any word is repeated, the number is written, rather than the word. It is necessary to maintain the dictionary because the dictionary is used to decompress the file. Most compression methods use the LZ adaptive dictionary-based algorithm.
For example: The cat is in the tree.
123415
In the above example “the” word is repeated twice, so rather than write “the” two times, it is easier to give the number.
There are two main techniques of data compression:
Lossless compression:Lossless compressionmaintains data integrity.
Lossy compression: Lossy compression does not maintain data integrity.
Lossless Compression Algorithms
Huffman Coding Algorithm
TheHuffman Coding Algorithmis a fixed-to-variable length code algorithm. It takes input characters that have a fixed length and gives the output, which has a variable length. The main concept behind the algorithm is that short code words are assigned to those input blocks that havehigh probabilities, and long code words to those with low probabilities. The characters can be arranged in any way.
This algorithm combines two possible characters into a single possibility by adding the code word. This procedure is continued until only one character remains. The tree is formed, and from that code tree, the Huffman code is obtained. Huffman codes are not unique. You can assign any label, such as a label to the upper branches of zero, and to the lower branches a label of one.
This algorithmuses two possible characters. In the example below, these characters are zero and one. The values with the highest probability,a_and_e, have the shortest codes (00 and 10). The values with the lowest probability,j_and_b, have the longest codes (111111 and 111110). Once these values are compressed, the file will be shorter because there will be fewer long-code values in the resulting file than short-code values.
Figure 5-7 shows a possible Huffman Coding system.
Lempel-Ziv-Welch Coding Algorithm
TheLempe**l-Ziv-Welch (LZW) algorithm**is used in most of the lossless compression techniques. LZW is a fixed-to-variable length code algorithm. Input is given in the variable length, while the output is given in the fixed length. It was generated not for a particular source, but for a large class of sources. In this algorithm, the input is given to the nonoverlapping blocks that have different lengths. The following explains how to apply the encoding algorithm:
F irst, create a dictionary which contains all the blocks of one length, but all are nonoverlapping blocks (D={a,b}).
Find the longest block W present in the dictionary.
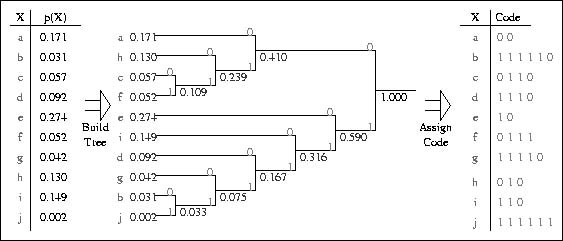
Source:http://computer.howstuffworks.com/framed.htm?parent=file-compression.htm&url=http://www.data-compression.com/lossless.html.Accessed 2/2007.
Figure 5-7 In this image, read the binary numbers backwards to reach the letters, discounting the 1.000. For example, F is 0111.
Encode that W, by its value present in the dictionary.
Add W, followed by the first symbol of the next block to the dictionary.
Return to step 2 and repeat the same procedure.
In this way, the final amount of bits needed to contain the same information is reduced.
Consider the following example.
A 000 E 100 B 001 F 101 C 011 G 110
D111STOP char010
In this example, the word BEAD would be encoded 001/100/000/111/010. Remember that when you apply LZW, you bundle single length entries and add new codes. For some of these codes, you may need to expand the returned code length (for example, adding another digit: 000 to 0000). Applying the LZW, the dictionary may be expandedto include the following entries:
| AB | 0000 | AD | 0101 |
|---|---|---|---|
| BC | 0001 | AE | 1010 |
| CD | 0011 | AF | 1001 |
| DE | 0111 | AG | 1011 |
| EF | 1111 | BD | 0110 |
| FG | 1110 | BE | 1101 |
| AC | 0100 | STOP char | 0010 |
Now the word BEAD would be encoded 1101/0101/0010, which is three bits shorter. If the dictionary is further expanded, the returned strings would get longer, but they include more values per string, and the overall length of the file is compressed.
Lossy Compression
Lossy compressionis different from lossless compression, as it can compress data permanently by overlooking some parts of the data. However, data integrity is not maintained in the lossy data compression technique.
The lossy data compression technique is never used for text compression. When a JPEG file is saved under a different image format, lossy compression is used to compress the data. However, once the image file is decompressed, the user will lose a lot of information. Another form of lossy compression is when vectors are used to compress the file, known asvector quantization.
Figure 5-8 shows lossy compression.
Lossy compression
Ori
g
inal Data
Restored
Data
Compressed
Data
Copyright © by
All rights reserved. Reproduction is strictly prohibited
Figure 5-8 In lossy compression, the restored data is less than the original data. For this reason, lossy compression is never used for text because the text is directly encoded, so any loss of information would be a critical loss.
Vector Quantization
Vector quantization is a lossy data compression technique. Vector quantization uses an algorithm to find out if the data can be disregarded based on vectors that are present in the image file. The algorithms used are based on the principle of block coding. In each block, the information is replaced by the approximate average value.
Figure 5-9 shows a sample of vector quantization. In this example, any value within a block that falls between -4 and -2 will return the value -3 (code 00). Therefore, any slight nuances to the image will be lost.
Locating and Recovering Image Files
The first and most valid step that the forensic examiner must take is to search and recover any image files that are appropriate to the case at hand. Images are not necessarily present in standard image formats; therefore, investigators must also examine files that are of nonstandard formats.
The Windows and DOS operating systems have a wide variety of tools that can recover image files. These tools search for and retrieve specific information that is embedded in the image itself. Every image file has a header, which gives programs instructions about how the image file should be displayed on the screen. When an image file is dispersedinto many areas on the disk, the forensic investigator should recover all the fragments in order to regenerate the image file. Looking for pieces of a file is known assalvaging, and in some parts of North America it is calledcarving.
In order to carve image file data from free space in the disk, it is essential to know about data patterns. These enable a forensic investigator to identify image file fragments. In any forensic investigation, this would be the first step in locating imagefiles. After recovering the parts of a fragmented image file, the next step is to restore the data fragments. The most common tool used for this purpose is DriveSpy. This tool is used to carve known data sets from the leftover recovered data. This information must be restored to view the image file.
Using DriveSpy to Locate and Recover Image File Fragments
Figure 5-10 shows the output of a DriveSpy search. It shows the location of the cluster, sector, and offset.
Vector Quantization
Error!00011011
0
1
2
3
4
-4
-3
-2
-1
Copyright © by

All rights reserved. Reproduction is strictly prohibited
Figure 5-9 Vector quantization is a kind of averaging, causing a lossy compression of data.
_Source:_DriveSpy software. Accessed 2/2007.
Figure 5-10 Fragmented image information from DriveSpy.
Computer forensic investigators use DriveSpy to locate and recover image file fragments. Investigators use the following simple steps to locate JPEG files on a disk:
Open a DOS command prompt window. Type inDriveSpyand press Enter to run the DriveSpy application.
At the DriveSpy SYS prompt, enterOutput Hdr_find.logto enable the application to record the output of the commands that can be used in a text file named Hdr_find.log.
Insert the target investigation floppy disk into the A:\ drive. At the SYS prompt, typeDrive A, and then press the Enter key to navigate to drive A:.
F rom the DA command prompt, typePart 1and then press Enter to display the partitioninformation for the floppy disk.
From the DAP1 command prompt, typeSearch**[filename]**(enter the file or folder name to look for) and press Enter. This will start a keyword search. At the prompt, press Y to turn off page mode.
From this process, the DriveSpy application searches the floppy disk for data that will match the search criteria, and can record this data in Hdr_find.log file. The log file can be viewed from Notepad as seen above.
Analyzing Image File Headers
Investigators must analyze image file headers when normal forensic tools cannot recognize new file extensions. Hexadecimal values present in the header can be used to define a file type in DriveSpy. A hexadecimal editor, such as Hex Workshop, can help access the file header.
For instance, when an investigator encounters a .h9 Freehand file, the file headers section of DriveSpy.ini is not able to define the .h9 format. In order to determine the file type, the investigator will need to know the file’s good header value. This can be found by comparing the existing file headers with file headers of another image file format. The investigator can then identify a tool that can rescue and display the image.
Repairing Damaged File Headers
Investigators recover damaged remnants from free space on the drive. This information would be similar to headers from common image files. Header data that is partly overwritten can be used to repair damaged headers. The HEX Workshop application can be used to repair damaged headers.
Each image file has a special file header value that depends upon the format of the file type. An investigator can identify residual data from partially overwritten headers in file free space by examining common image header values. For example, the JPEGimage file format has a hexadecimal value of FF D8 FF E0 00 10. Most JPEG files have the letters JFIF after the hexadecimal values of the file, as in FF D8 FF E0 00 10 JFIF. If a file fragment is found with JFIF, or the hexadecimal value associated with JPEG files, it is possible to identify the JPEG image.
Carving Data from Unallocated Space
Once a forensic investigator has identified data, a computer forensic program can carve, or retrieve, the fragmented image file. DriveSpy is the most popular tool used by forensic investigators for this purpose.
First, the investigator creates a duplicate bit-stream copy of the original evidence files using Digital Intelligence Image. Once the target disk contains the complete image of the file, DriveSpy can locate thefile on the original disk and carve the data from the unallocated space. The SaveSect command is then used to save the file as an external file.
Reconstructing File Fragments
Corruption of data prevents investigators from reconstructing file fragments from an image file. Data can be corrupted accidentally without the knowledge of the user of the computer, or the data can be corrupted intentionally. It is up to the forensic investigator to find out how the data was corrupted. File fragments can be reconstructed by using DriveSpy to examine a suspect disk. Investigators can then build the case based on the reconstructed data.
Many forensic investigations lead to the conclusion that the suspect has intentionally corrupted data in order to hide incriminating evidence. The suspect may have done this by corrupting cluster links in a FAT table of a disk. A disk-editing tool can helpa forensic investigator access the FAT table and identify the corrupted cluster. Corrupted clusters display 0000 in the disk editor. Take the example of the screenshot shown in Figure 5-11 where the image file header is a bitmap (shown in the highlightedportion of the hexadecimal values). Figure 5-11 shows the output of Hex Workshop when repairing a fragmented image file.
_Source:_Hex workshop software. Accessed 2/2007.
Figure 5-11 Fragmented data is encoded in hexadecimal.
It can be repaired using a disk-editing tool.
Identifying Unknown File Formats
Computer forensic investigators often come across unknown image file formats. The following is a list of nonstandard image file formats:
Targa (.tga)
Raster Transfer Language (.rtl)
Photoshop (.psd)
Illustrator (.ai)
Freehand (.h9)
Scalable vector graphics (.svg)
Paintbrush (.pcx)
In order to find and view nonstandard image file formats, forensic investigators can use any search engine, using the image file extension, to identifyand download a tool that can view the image. The following tools can identify nonstandard file formats:
FILExt
IrfanView
ACDSee
ThumbsPlus
ADPictureViewer
Max
FastStoneImageViewer
XnView
Tool: FILExtFILExt is a quick way to identify the file type or parent application of a file based on the extension. On the FILExt Web site, enter the extension (for example, .lmp), and the application will return the most likely file type as well as some notes aboutthe parent application and/or history of the file type. Some even return header strings in hexadecimal. Some extensions, such as .crc, will return several possible parent applications or file types. A forensic investigator can use the header strings to confirm which of the returned file types it is.
Tool: Picture Viewer: IrfanViewIrfanView is an image viewing program that supports many nonstandard file formats including:
Targa (.tga)
Illustrator (.ai)
Scalable vector graphics (.svg)
FlashPix (.fpx)
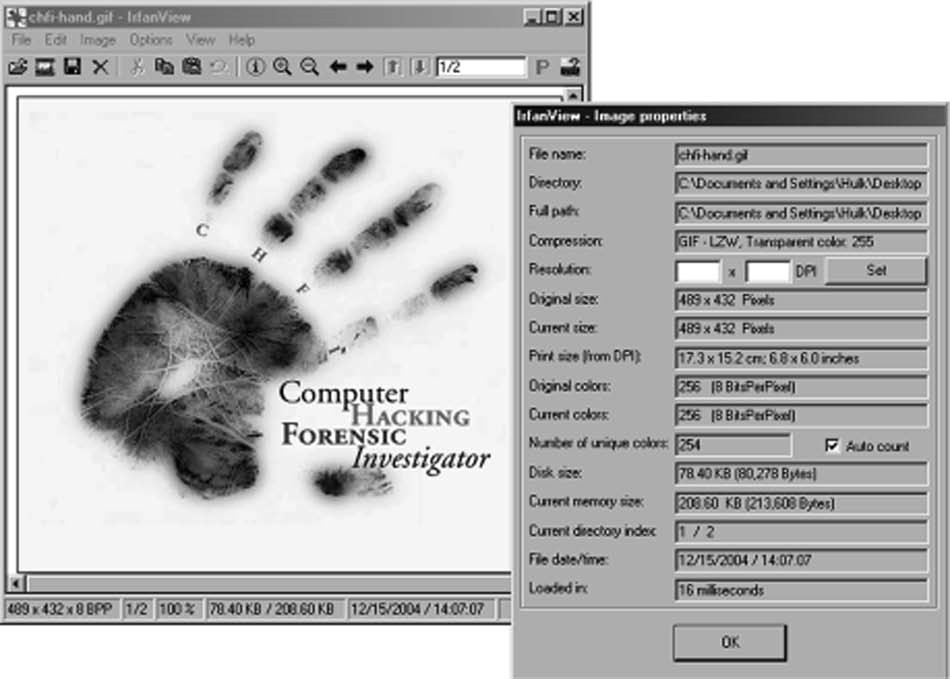
Source:
IrfanView software. Accessed 2/2007.
Figure**5-12**
IrfanViewcanrecoverseveralimagefile
formats.
_Source:_ACDSee software. Accessed 2/2007.
Figure 5-13 ACDSee can recover several image file formats.
Some notable features of IrfanView include:
Ability to edit and add to images
Various view options, including slideshow and thumbnail view
Batch conversion
Command line options
Multipage TIFF editing and lossless JPEG rotationFigure 5-12 shows the IrfanView application screen.
Tool: ACDSeeACDSee is an image-viewing program that allows an investigator to find, view, manage, and edit images. With ACDSee version 7, investigators can also acquire image files, create PDFs, and view unknown file formats, including media files. ACDSee viewer displays images in full resolution.
Figure 5-13 shows the ACDSee application screen.
Tool: ThumbsPlusThumbsPlus is an image-cataloguing program that enables an investigator to locate, view, edit, print, and organize images, metafiles, fonts, and movies.
Version 6.0 supports a variety of file formats, including:
Common formats: TIFF, JPEG, PNG, RAW
Photoshop (.psd), including documents loaded with plug-ins
Various camera file formats
Images loaded using new Cerious plug-ins
Scanned images (TWAIN)
Figure 5-14 shows thumbnails to be recovered via the ThumbsPlus application.
Tool: AD Picture ViewerAD Picture Viewer is a fast and compact image viewer for the Windows environment. It allows an investigator to view, print, organize, and manage images. It supports all popular graphic formats.
Figure 5-15 shows an image displayed by AD Picture Viewer.
Source:
ADViewer software. Accessed 2/2007.
Figure**5-15**
ADPictureViewercandisplayawide
varietyofimageformats.
_Source:_ThumbsPlus software. Accessed 2/2007.
Figure 5-14The images in this screenshot can be recovered by ThumbsPlus.
Tool: Picture Viewer MaxPicture Viewer Max is an image and multimedia viewer for Windows 98/ ME/2000/XP. It locates, views, edits, prints, organizes, sends and receives picture and image files, including videos, sounds, music, text files, documents, HTML, and system files. A forensic investigator can edit picture/ image files using techniques such as flip, reverse, rotate, resize, brightness, contrast, color saturation, gray scale, hue, and other special effects and filters.
Some notable features of Picture Viewer Max are:
It canadd 3-D text and geometric shapes to pictures and images displayed in a multiple document interface.
It can create blank picture frames with color gradients for logos or picture backgrounds.
It supports: JPG, CMP, GIF, uncompressed TIF, TIFF, BMP, ICO, CUR, PCX, DCX, PCD, FPX, WMF,
EMF, FAX, RAW, AWD, XPB, XPM, IFF, PBM, CUT, PSD, PNG, TGA, EPS, RAS, WPG, PCT, PCX,
CLP, XWD, FLC, ANI, SGI, XBM, MAC, IMG, MSP, CAL, ICA, SCT, SFF, SMP, TXT, BAT, LST, WRI, SYS, RTF, HTM, HTML, PSP, ASP, DOC, PDF, AVI, AVI(DivX), MPG, MPEG, MOV, MP3, M3U, ASX, ASF, MID, RMI, MP2, AIFF, M1V, WMA, and WMV.
It can convert picture file formats between picture file types.
It can print up to eight pictures on a page, with titles for each page and picture. Select your font and color for all printed text.
It can receive pictures and Zip files by e-mail, and view, edit, save, and print with Picture Viewer Max.
Figure 5-16 shows Picture Viewer Max.
Tool: FastStone Image Vie**wer**The FastStone Image Viewer is an image browser, converter, and editor. It has a nice array of features that include: image viewing, management, comparison, red-eye removal, emailing, resizing, cropping, and color adjustments.
Some notable features of FastStone Image Viewer are:
Image modification tools: Resize/resample, rotate/flip, crop, sharpen/blur, brightness/contrast
Support for all major graphic formats (BMP, JPEG, JPEG 2000, animated GIF, PNG, PCX, TIFF,
WMF, ICO, and TGA), and popular digital camera RAW formats (CRW, CR2, NEF, PEF, RAF, MRW, ORF, SRF, and DNG)
- High quality magnification and a musical slideshow with 150+ transitional effects
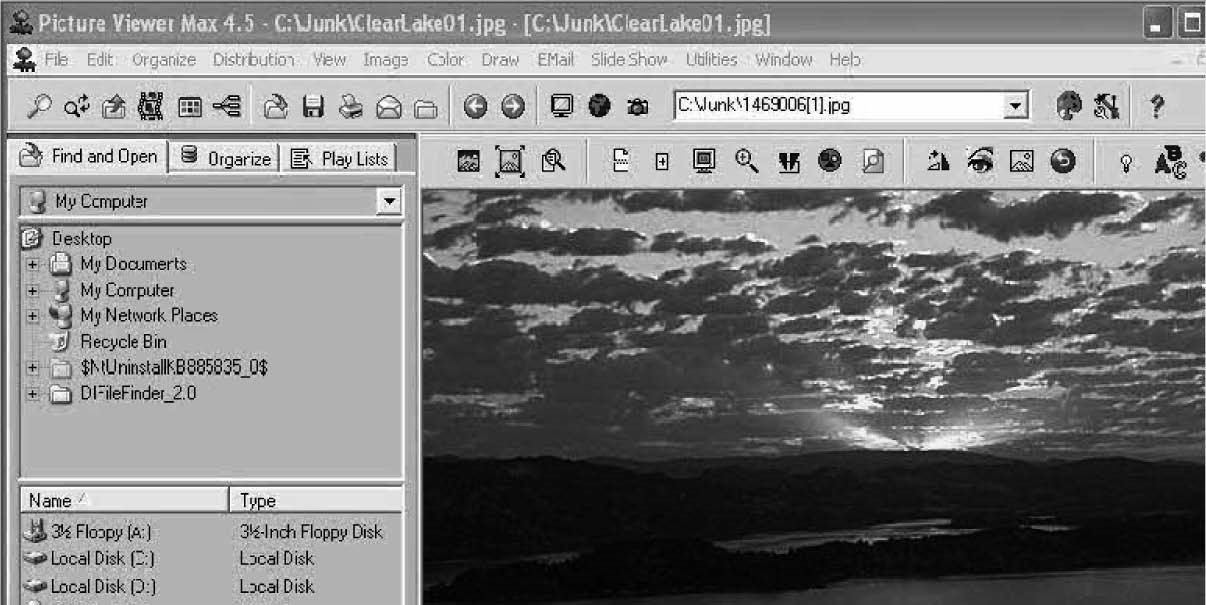
Source:http://www.accessoryware.com/PictView.htm.Accessed 2/2007.
Figure 5-16 Picture Viewer Max supports a huge variety of file types, including image, music, and movie files.
Source:http://www.faststone.org/FSViewerDetail.htm.Accessed 2/2007.
Figure 5-17FastStone Image Viewer is an image editing and management tool.
Image annotation and scanner support
Image color effects: gray scale, sepia, negative, red/green/blue adjustment
Image special effects: watermark, annotation, drop shadows, framing, bump map, lens, morph, waves
Image management, including tagging capability, with drag-and-drop and copy to/move to folder support
Versatile screen capture capability
Figure 5-17 shows the application screen for FastStone Image Viewer.
_Source:_XNView software. Accessed 2/2007.
Figure 5-18This is the XnView application screen.
Tool: XnViewThe XnView tool can display and convert graphics files. It supports more than 400 graphics formats. It supports Windows, MacOS X, Linux x86, Linux ppc, FreeBSD x86, OpenBSD x86, NetBSD x86, Solaris sparc, Solaris x86, Irix mips, HP-UX, and AIX.
XnView includes the following features:
It can import about 400 graphics file formats and export about 50 graphics file formats.
It can support multipage TIFF, animated GIF, and animated ICO, as well as Image IPTC and EXIF metadata.
It can support resize, rotate, and crop.
It includes support for auto levels and contrast.
The user can apply filters and effects (for example, blur, average, emboss, lens, wave) and modify the number of colors.
It supports full-screen mode.
It has support to create or edit multipage files (TIFF, DCX, LDF).
It prints, drags and drops, and has 44 languages in Windows.
Figure 5-18 shows the XnView application.
Tool: FACES—Sketch SoftwareFACES contains a database of more than 3850 facial features, including tools and accessories. This utility allows you to compose many images with their permutations and combinations. Law enforcement agencies use the software to identify suspects.
The features included in the software are coded in morphological order, and allow you to design images or faces of your choice with ease. One of the main features of this software is the utility InterCode, which encrypts the composite image and converts itinto a character ID code. There exists a unique InterCode with every original image. When you click in the InterCode, a corresponding composite image appears on the screen. Thus, the software performs the process in seconds. This software is primarily used by law enforcement agencies and crime branch investigation organizations in identifying suspects.
Figure 5-19 shows the FACES sketch software application screen.
Source:http://www.facesinterquest.com.Accessed 2/2007.
Figure 5-19Users can add or change facial features to develop a composite image of a suspect.
Steganography in Image Files
Since the introduction of the Internet, hidden messages inside digital images have become the most common and highly effective form of steganography. Images are stored as a group of pixels, 8–24 bits per pixel. This group of pixels can be stored in a second image file in one of three ways.
There are also three methods that are used to hide the messages inside these images, they include:
Least-significant-bit method
Filtering and masking
Algorithms and transformation
Figure 5-20 shows the process of steganography, embedding a message into an image and extracting it for analysis.
Steganography in Image Files
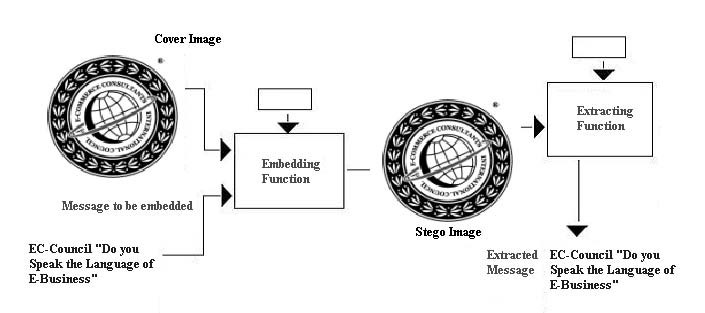
Copyright © by

All rights reserved. Reproduction is strictly prohibited
Figure 5-20Notice how a secretmessage is embedded into an unrelated image.
Steganalysis
Steganalysisis the reverse process of steganography. Steganography hides the data, while steganalysis is used to detect the data hidden via steganography. Steganalysis determines the encoded hiddenmessage, and if possible, recovers that message. The message can be detected by looking at variances between bit patterns and unusually large file sizes.
There are two main challenges of steganalysis:
The data may have been encrypted before it was hidden.
If some of the signal or file contains noise or irrelevant data encoded into it, steganalysis can be compli-cated and take longer.
Tool: Hex Workshop
The Hex Workshop is a set of hexadecimal development tools for Microsoft Windows, combining advanced binary editing with the ease and flexibility of a word processor. With Hex Workshop, forensic investigators can edit, cut, copy, paste, insert, and delete hex; print customizable hex dumps; and export to RTF or HTML for publishing. Additionally, investigatorscan go to, find, replace, compare, and calculate checksums and character distributions within a sector or file.
Hex Workshop is integrated with Windows Explorer so investigators can hex-edit from the most frequently used workspaces. Hex Workshop includes aBase Converter for converting between hex, decimal, and binary, and a Hex Calculator supporting arithmetic and logical operations. The Hex Workshop also contains a Data Inspector and Structure Viewer so examiners can view and edit interpreted decimal values and embedded arithmetic and logical operations, allowing direct manipulation of the data. Some features of the Hex Workshop application include:
A highly customizable editing environment
Data in its natural and native structured form as viewed through the Structure Viewer
Dynamic bookmarks in a simple macro language
The ability to edit sectors of floppies and hard disks
Prints high-quality hex dumps with customized headers, footers, and fonts
Views and edits raw binary data as decimal values with the Data Inspector
Interprets values in either little-endian (e.g., Intel) or big-endian (e.g., Motorola) byte ordering
Manipulates data using one of 22 embedded operations: byteflip, inverse bits, left shift, right shift, rotate left, rotate right, block shift left, block shift right, XOR, OR, AND, change sign, plus, minus, multiply, divide, mod, setfloorvalue, setceilingvalue, uppercase, lowercase, and swapcased
Inserts external file contents or savea block of data as a new file
Changes are tracked and coded in color
Exports and copies hex as RTF, text, and HTML for publishing or as C source or Java source
Imports and exports Intel hex code and Motorola S-Records.
Finds and replaces hex, bitmasks, decimal, or ASCII (including Unicode) values
Easily navigates documents and sectors using the goto command
Views text interpretations under ASCII, DOS, EBCDIC, Macintosh, Windows, and Unicode character
set filters
A binary compare tool to find differences in files
Calculates checksums and digests (MD2, MD4, MD5, SHA1) for all or part of a file
Views character distributions and exports results as tabbed text or comma-separated values
File/disk properties with the click of the mouse
File/disk attributes in the status bar
Online help including multiple character tables and list of data types and rangesFigure 5-20a shows the Hex Workshop application.
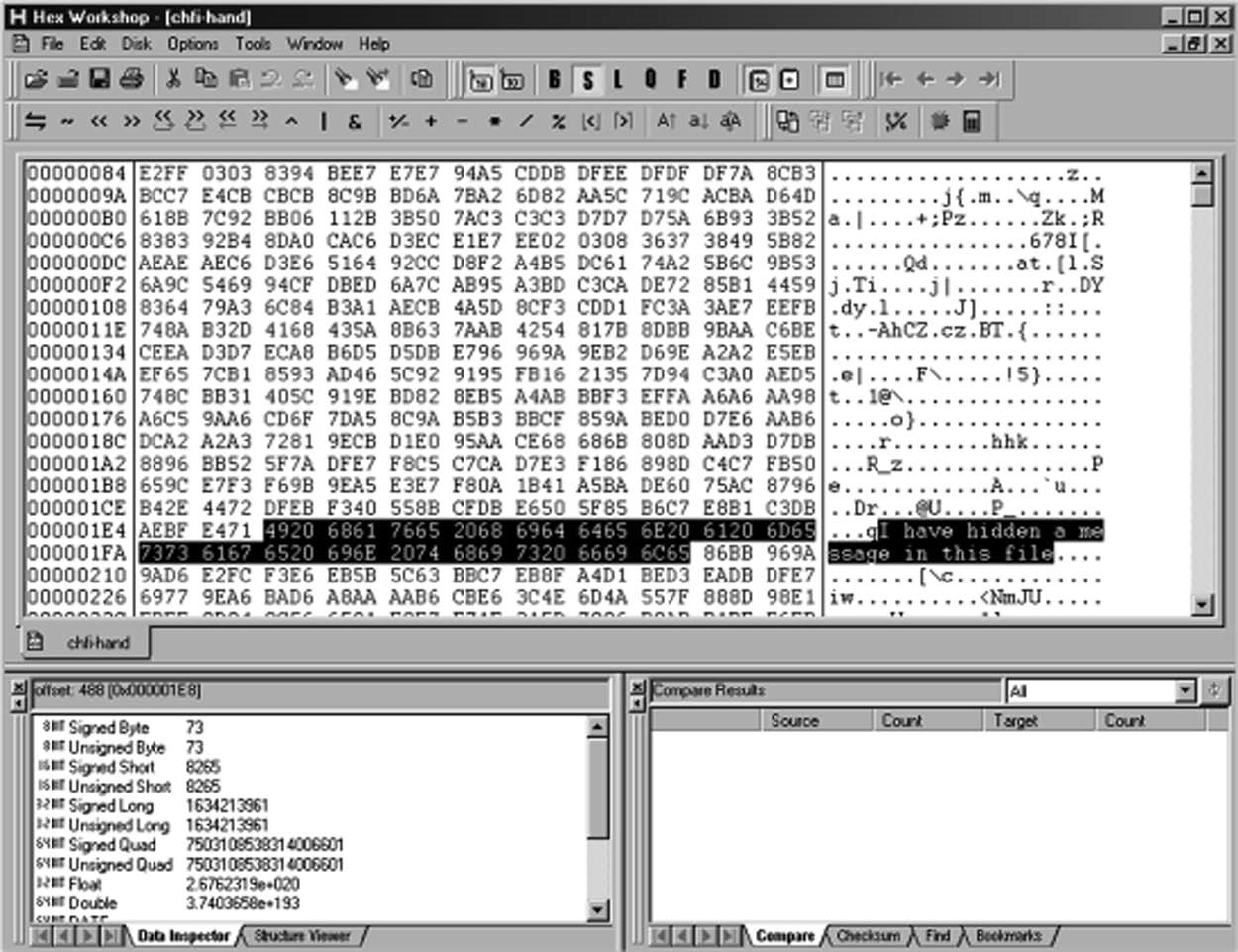
Figure 5-20aHex Workshop is one of the most popular applications forsteganalysis and image recovery.
Tool: S-Tools
The S-Tools steganographic tool has one advantage over other steganographic tools: hiding multiple files in one object. S-Tools first compresses individual files. This application inserts some random data strings on the front of the data in order to prevent two identical sets of files encrypting the same. All the files are then encrypted using a user-generated pass phrase. The encryption algorithms all operate in cipher feedback mode. The S-Tools application seeds a cryptographically strong pseudorandom number from the pass phrase, and uses its output in order to choose the position of the next bit from the cover data.
Take the following example: If a sound file had 100 bits available for hiding, and the user wanted to hide 10 bits in it, then S-Tools would not choose bits 0 through 9, as they are detectable by a potential enemy. Instead it might choose bits 63, 32, 89, 2, 53, 21, 35, 44, 99, and 80. It might even choose any ten others; it all depends on the pass phrase used. Thereby, an investigator would have a difficult time in deciphering the code.
Tool: Stegdetect
Stegdetect is used for the detection of steganographic content in an image. Stegdetect supports linear discriminant analysis.Linear discriminant analysisis the technique that determines the stego image that contains the hidden data. It detects different steganographic methods to embed hidden information in JPEG images.
Stegdetect supports several different feature vectors, andautomatically computes receiver operating characteristics, which can be used to evaluate the quality of the automatically learned detection function.
Can penetrate information hidden using applications such as jsteg, jphide (UNIX and Windows), Invisible Secrets, Outguess v.01.3b, F5, appendX, and Camouflage.
Figure 5-21 shows the application screen for xsteg.
Tool: GFE Stealth (Graphics File Extractor)
GFE stealth is an image file forensics tool, which reveals the exact copies of the graphics file images from ambient data sources and SafeBack bit-stream image backup files. It quickly detects all graphics file images on the hard disk drive, and extracts the required images with the help of the graphics file viewer. It recovers GIF, BMP, and JPEG files from the computer. It recovers the image files quickly, which saves the investigator time.
GFE Stealth operates under DOS, Windows 98/NT/2000/XP. It identifies partial image file patterns (caused due to fragmentation and/or file corruption) and views and reconstructs the files. The search engine ensures that every byte is checked for integrity. When the software is combined with other NTI software processes,
_Source:_xsteg software. Accessed 2/2007.
Figure 5-21In this image, the software shows that it has not detected steganography in the selected file.
it operates in batch file mode for automatic processing. The software is very fast and evaluates graphic image files quickly.
Tool: ILook v8
ILook is a multithreaded, Unicode-compliant image file forensic investigation tool. It recovers images from seized computer systems or other digital media quickly. It is also used to detect images obtained from forensic imaging tools that produce a raw bit-stream image. It supports Windows 2000 or Windows XP 32-bit platforms and the Windows Server 2003 64-bit platform. Some features of ILook include:
Identification and support of the following file systems: FAT12, FAT16, FAT32, FAT32x, VFAT, NTFS, HFS, HFS+, Ext2FS, Ext3FS, SysV AFS, SysV EAFS, SysV HTFS, CDFS, Netware NWFS, ReiserFS, and ISO9660
An Internet Explorer–like interface allowing an investigator to view and navigate the file system as it originally appeared on the suspect’s computer
Granular extraction facilities that allow all or part of a file system to be extracted from an image
Fast, sophisticated, regular expression search engine
Built-in multiformat file viewing
Password and pass-phrase dictionary generators
File salvage (carve) capabilities
Orphaned FAT directory recovery
Hash analysis functions
Data tagging and categorization features
Case and evidence management features and multievidential item handling
Internet cache and mailbox deconstruction functions
Additional imager built into ILookfor imaging directly attached devices
Source:http://www.ilook-forensics.org/iLookv8.html.Accessed 2/2007.
Figure 5-22This is the ILook application screen.
File filtering and elimination functions
Search-results database stores the results of all searches run against any item in a caseFigure 5-22 shows the ILook application screen.
Tool: P2 eXplorer
Paraben’s P2 eXplorer allows an investigator to mount a forensic image and explore it as though it were a drive. The image is not just mounted to view logical files, but is mounted as the actual bit-stream image, preserving unallocated, slack, and deleted data. P2 eXplorer is able to:
Mount compressed and encryptedPFR images and several images at a time
Mount Paraben’s Forensic Replicator images (PFR), EnCase images (up to v4.02), SafeBack 1 and 2 im-ages, WinImage noncompressed images and RAW images from Linux dd and other tools
Support dynamic drive images and both logical and physical image types
Autodetect image format
Shell support easy mounting/unmounting as well as mounting over a network
Write-protect for preserving evidence
MD5 checksum verify and hash verify
Figure 5-23 shows the P2 eXplorer screen.
Identifying Copyright Issues with Graphics
Section 106 of the 1976 Copyright Act gives the owner of a graphic or image copyright the exclusive right to do and to authorize any of the following:
Reproduce the copyrighted work in copies or phonorecords;
Prepare derivative works based upon the copyrighted work;
Distribute copies or phonorecords of the copyrighted work to the public by sale or other transfer of ownership, or by rental, lease, or lending;
In the case of literary, musical, dramatic, and choreographic works, pantomimes, and motion pictures and other audiovisual works, perform the copyrighted work publicly;
Review Questions
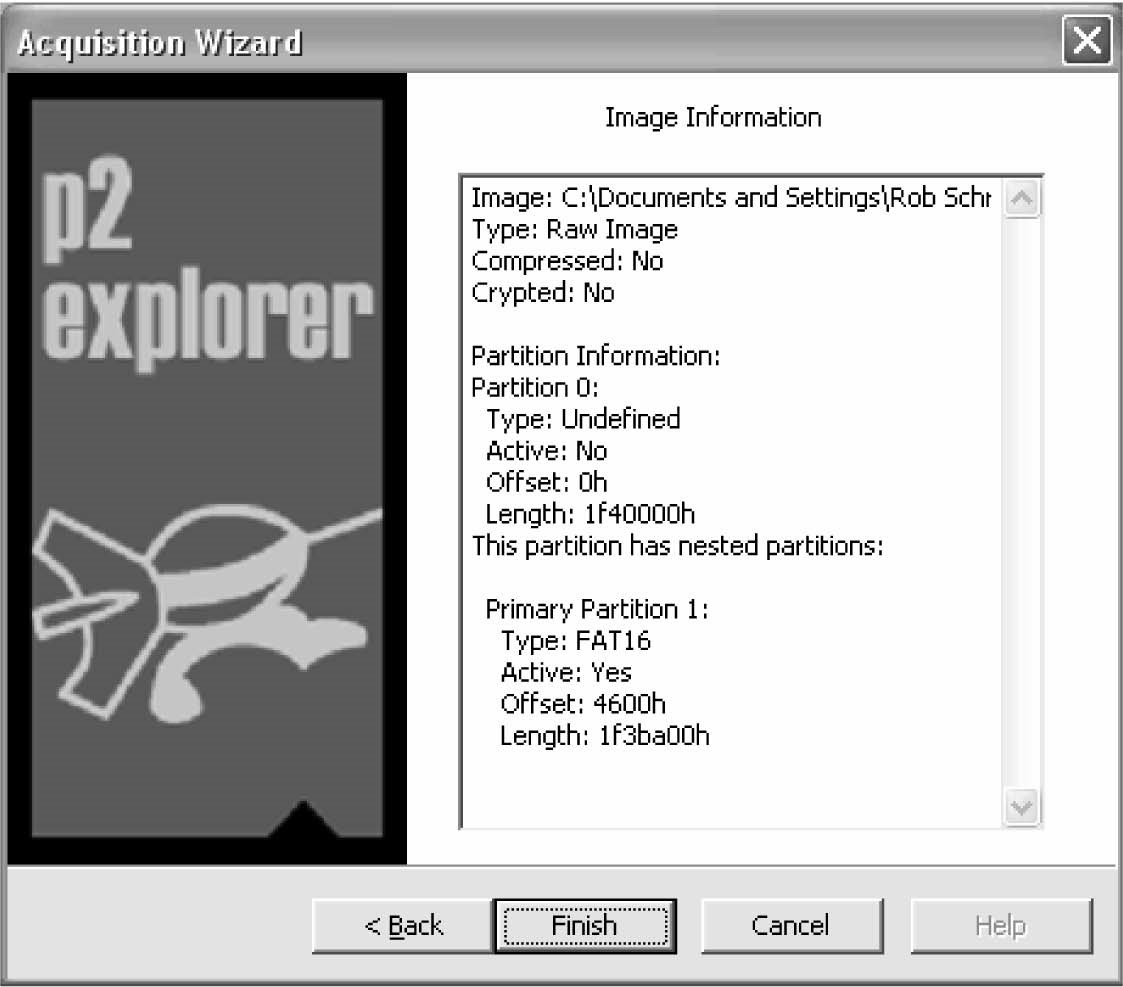
Source:https://www.paraben-forensics.com/catalog/product_info.php?cPath=25&
products_id=268. Accessed 2/2007.
Figure 5-23This figure shows an image mounted as a drive.
It has a secondary “partition,” which may be a hidden image.
In the case of literary, musical, dramatic, and choreographic works, pantomimes, and pictorial, graphic, or sculptural works, including the individual images of a motion picture or other audiovisual work, display the copyrighted work publicly; and
In the case of sound recordings, perform the work publicly by means of a digital audio transmission.
Chapter Summary
■An image is an artifact that reproduces the likeness of some subject.
■A file format is a particular way to encode information for storage ina computer file.
■Standard image file formats include JPEG, GIF, BMP, TIFF, and PNG.
■Data compression means encoding the data to take up less storage space and less bandwidth for t ransmission.
■Data compression is performed by using a complex algorithm to reduce the size of a file.
■Lossy compression compresses data permanently by removing information contained in the file.
■Image files have a unique file header value. Common image header values have residual data from partially overwritten headers in file slack.
Review Questions
- Describe three differences between vector images and raster images.
- Name three image file formats and name whether each is vector, raster, or both.
- How does file compression work?
- What is the difference between lossless and lossy data compression? Which would you use with text
files?
- Describe two main differences between the LZW and Huffman coding systems.
- When you analyze image file headers, what are you looking for?
- What does carvingmean?
- Name a steganalysis tool and describe how it works.
- How do you reconstruct file fragments?
- List three different image file forensic tools. Describe why you would use each.
Hands-On Projects
 Install ACDSee and search for images on your hard disk.
Install ACDSee and search for images on your hard disk.Install XnView and convert a BMP file to a GIF format. Find the difference in the size of the image file.
Install S-Tools and try to hide/unhide an image file. Find out whether the amount of free space on the disk changes when you hide/unhide an image file.
Use Photoshop to edit an image of your choice.
A
ACDSee, 5-18
Acronis Recovery Expert, 4-54
Active@ Disk Image, 4-54–4-55, 4-56
Active@ Partition Recovery, 4-55–4-56, 4-57
Active@ UNDELETE, 4-9, 4-10
Active@ UNERASER, 4-9–4-11
AD Picture Viewer, 5-18, 5-19 Algorithms, 1-10 appendX, 1-40
Audio files, 1-11, 1-18
B
BadCopy Pro, 4-12
Bitmap (BMP) files, 5-9, 5-10 BlindSide, 1-20–1-21
BMP (Bitmap) files, 5-9, 5-10
Bookmarks, in Encase, 3-10–3-12, 3-13
Boot disks, in Encase, 3-20
ByteShelter I, 1-39, 1-40
C
Camera/Shy, 1-23
Camouflage, 1-38, 1-39
Carving, 5-15, 5-16
CD Data Rescue, 4-43, 4-44
CDRoller, 4-44–4-45
Checksum, 3-2
Cloak, 1-31–1-32
CMYK scale, 5-3
Compression, watermarks and,
1-14–1-15
Copying files and folders, in Encase, 3-19
Copyright issues, with graphics,
5-26–5-27
Covered ciphers, 1-4
Cover medium, 1-2
CRC (cyclic redundancy check), 3-2
CryptArkan, 1-35, 1-36
CryptoBola JPEG, 1-39, 1-40
Cryptography, 1-12–1-13
Cyclic redundancy check (CRC), 3-2
D
Data acquisition defined, 2-2 determining best methods for, 2-2 hardware tools, 2-8–2-12 introduction, 2-2 recovery contingencies, 2-3 software tools, 2-3–2-8
Data compression, in image files, 5-11–5-12
Data duplication defined, 2-2 hardware tools, 2-16–2-18 introduction, 2-2 need for, 2-3 software tools, 2-12–2-16 Data Stash, 1-30 dd command, 2-4

Index
Deleted files data recovery in Linux, 4-8 introduction,4-2 overview, 4-2–4-7 recovery tools for, 4-8–4-50
Deleted NTFS Partition Data Recovery, 4-58
Deleted partitions introduction, 4-2 recovering, 4-50–4-63 recovering in Encase, 3-16, 3-17 using command line, 4-51–4-53 using Windows interface, 4-51
Delete partition, defined, 4-52
Desktop.ini file, 4-7
Device tab, in Encase, 3-6–3-7
DFSMSdss, 2-15–2-16
Digimarc Digital Watermarking, 1-15
Digital file types audio, 1-11, 1-18 image, 1-9–1-10, 1-18 text, 1-8–1-9, 1-18 video, 1-11, 1-18
Digital music, steganography for, 1-3
Digital steganography, 1-4, 1-5–1-8
Digital watermarks, 1-14
Direct sequence, 1-6
DiskExplorer, 2-14
Disk geometry, in Encase, 3-16
DiskInternals CD and DVD Recovery,
4-46–4-47
DiskInternals Flash Recovery, 4-45–4-46
DiskInternals Partition Recovery, 4-56, 4-58
DiskInternals Uneraser, 4-12–4-13
Disk Jockey IT, 2-17–2-18
Disk-to-disk copy, 2-2
Disk-to-image file, 2-2
Distortion technique, 1-8
Dithering, 5-5
DriveLook, 2-13–2-14
Drive SnapShot, 2-7, 2-8
DriveSpy, 2-5–2-6, 5-15–5-16
E
e2undel, 4-33, 4-34
Easy-Undelete, 4-14–4-15 Echo data hiding, 1-11 eData Unerase, 4-13–4-14 eIMAGE Recovery, 4-41
E-mail recovery, in Encase, 3-19
Embedded message, 1-2
EnCase bookmarks, 3-10–3-12, 3-13 boot disks, 3-20 configuring, 3-4 copying files and folders, 3-19, 3-20 Device tab, 3-6–3-7 e-mail recovery, 3-19 evidence files, 3-2–3-3 hash values, 3-16–3-18 image acquisition, 3-4 introduction, 3-2
master boot record (MBR), 3-14–3-15
recovering deleted files/folders in FATpartition, 3-12–3-13, 3-14
I-1
I-2Index
recovering deleted partitions, 3-16
recovering files/folders in NTFS partition, 3-13–3-14reporting, 3-19, 3-20 searching, 3-8–3-10, 3-11 signature analysis, 3-18, 3-19 status bar, 3-7–3-8 view disk geometry, 3-16 viewers, 3-18
View menu, 3-4–3-6
End-of-line spacing, 1-9
Evidence files, 3-2–3-3
EzStego, 1-38
F
FACES—Sketch Software,
5-21, 5-22
FastStone Image Viewer, 5-19–5-20
File compression, 5-12–5-13
File generation, 1-7
File Recover, 4-15–4-16
File-Saver, 4-17
File Scavenger, 4-17–4-18
FILExt, 5-17
Filtering, 1-10
FortKnox, 1-20
Fragile watermarks, 1-15
Frequency hopping, 1-6
FTK imager, 2-6
Fundelete, 4-19
G
GetDataBack, 4-57–4-58, 4-59, 4-60
GFE Stealth (Graphics File Extractor),
5-24–5-25
GIFExtract, 1-41
GIF (Graphics Interchange Format) files,
1-9, 5-5–5-7
Gifshuffle, 1-24
Global Regular Expressions Post (GREP) search, 3-8
Graphics, copyright issues with,
5-26–5-27
Graphics Interchange Format (GIF) files,
1-9, 5-5–5-7
Grayscale, 5-3
Grill ciphers, 1-4
H
Handy Recovery, 4-19–4-20
Hashing, 3-3, 3-16–3-18
Hermetic Stego, 1-32–1-33
Hex Workshop, 5-23, 5-24
Huffman Coding Algorithm, 5-13
Hydan, 1-30, 1-31
I
ILook v8, 5-25–5-26
Image acquisition, in Encase, 3-4
Image files, 1-9–1-10, 1-18 data compression in, 5-11–5-12 formats of, 5-4–5-11 introduction, 5-3
locating and recovering, 5-15–5-21, 5-22raster images, 5-4 steganography in, 5-22–5-27 vector images, 5-3
ImageMASSter 6007SAS, 2-16–2-17
Image MASSter Solo-3, 2-8–2-10
ImageRecall, 4-40 Indexed color, 5-3 inDisc Recovery, 4-47–4-48 INFO2 files, 4-5–4-6
Information hiding issues, 1-16–1-17
Info Stego, 1-36, 1-37
Injection, 1-5
InPlainView, 1-38
Interlacing, 5-5
International Organization for
Standardization (ISO), 3-18
International Telecommunications
Union (ITU), 3-18
Intersentence spacing, 1-8
Interword spacing, 1-9
Invisible inks, 1-3
Invisible Secrets 4, 1-28, 1-29
Invisible watermarks, 1-14
IsoBuster, 4-48–4-49, 4-50
J
Jargon codes, 1-4
JPEG (Joint Photographic Experts Group) files, 1-9, 5-7–5-8
Jpegx, 1-38
JPHS, 1-25
K
Keywords, in Encase, 3-9–3-10
L
Least significant bit (LSB), 1-5–1-6
Least-significant-bit (LSB) insertion, 1-9–1-10
Lempel-Ziv-Welch (LZW) algorithm,
5-13–5-14
Limited color palette, 5-5
Linear discriminant analysis, 5-24
Linguistic steganography, 1-3, 1-4
LinkMASSter-2, 2-10–2-11
Linux, data recovery in, 4-8
Linux data acquisition tools, 2-3–2-4
List disk, 4-52
List partition, 4-52
Lossless compression algorithms, 5-13–5-14
Lossy compression, 5-14–5-15
Low-bit encoding, in audio files, 1-11
LZW algorithm, 5-13–5-14
LZW compression, 5-5
M
MandelSteg, 1-41
Masker, 1-28–1-29
Masking, 1-10
Master boot record (MBR), 2-4, 3-14–3-15
Master key, 1-13
MD5 Hash, 3-16, 3-18
Medical records, steganography for, 1-2
Metafile graphics, 5-4
Microdots, 1-3
Mosaic attacks, 1-16
Mount Image Pro, 2-6–2-7
Movie industry, steganography for, 1-3
Mycroft, 4-20–4-21
N
Null ciphers, 1-4
O
O&O UnErase, 4-21–4-22
OfficeFIX, 4-36–4-37
Open codes, 1-4
Open-space steganography, 1-8–1-9
OutGuess, 1-26–1-27
P
P2 eXplorer, 5-26, 5-27
Partitions._See_Deleted partitions recovering deleted, in Encase, 3-16, 3-17
Partition Table Doctor, 4-59, 4-61
PC Inspector File Recovery, 4-22, 4-23
PC Inspector Smart Recovery, 4-49, 4-50
Perceptual masking, 1-7
Phase coding, 1-11
Picture Viewer- IrfanView, 5-17–5-18
Picture Viewer Max, 5-19, 5-20
Pixel, 5-4
PNG (Portable Network Graphics) files,
5-9–5-10
Pretty Good Envelope, 1-24
Public key infrastructure (PKI), 1-13
Q
QuickCopy, 2-18
R
Raster images, 5-4
R-Drive Image, 2-12, 2-13
Recover4all Professional, 4-25–4-26
Recovering deleted files and folders, in
Encase, 3-12–3-15
Recover It All!, 4-59–4-60
Recover My Files, 4-24, 4-25
RecoverPlus Pro, 4-38–4-39
Recycle bin for deleting files, 4-2, 4-3 explained, 4-5–4-6 storage location in FAT and NTFS, 4-4–4-5 in Windows, 4-3–4-4
Recycled folder, 4-5, 4-6–4-7
Repair My Excel, 4-37–4-38
Reporting, 3-19, 3-20
Restorer2000, 4-26, 4-27
RGB scale, 5-3
R-Linux, 4-34, 4-35
RoadMASSter-2, 2-11–2-12
Robustness attack, 1-15–1-16
Robust watermarks, 1-15
R-Undelete, 4-23, 4-24
S
SafeBack, 2-8
Salvaging, 5-15
Save-N-Sync, 2-14–2-15
Scaven, 4-60–4-61
Scramdisk, 1-38, 1-39
SCSIPAK, 2-16
Search and Recover, 4-27–4-28
Searching, in Encase, 3-8–3-10
Security identifier (SID), 4-4
Select disk, 4-52
Select partition, 4-52
Semagrams, 1-4
Semifragile watermarks, 1-15
Session key, 1-13
Signature analysis, in Encase, 3-18, 3-19
SnapBack DatArrest, 2-8
Snow, 1-22, 1-23
Sparse data copy, 2-2
Spread spectrum, 1-11
Spread-spectrum encoding, 1-6
Statistical method, 1-7
Status bar, in Encase, 3-7–3-8
Stealth files, 1-36–1-38
Steganalysis, 1-18–1-19, 5-23
Steganography application of, 1-2–1-3 classification of, 1-3–1-8 cryptography, 1-12–1-13 defined, 1-2 detecting, 1-17–1-19 digital file types, 1-8–1-11 file systems, 1-11–1-12 in image files, 5-22–5-27 information hiding issues, 1-16–1-17 introduction, 1-2 stegosystem model, 1-2 tools for, 1-19–1-41 watermarking, 1-14–1-16
Steganos, 1-24
Steganosaurus, 1-39
StegaNote, 1-32
IndexI-3
Stegdetect, 5-24
StegHide, 1-22
Stego-forensics, 1-19
Stego Hunter, 1-35
Stego-key, 1-2
Stegomagic, 1-32, 1-33
Stego-medium, 1-2
Stego Suite, 1-34, 1-35
Stegosystem model, 1-2
StegParty, 1-34
StegSpy, 1-35
Stellar Phoenix, 4-35, 4-36
S-Tools, 1-21, 5-24
SUPERFileRecover, 4-28, 4-29
Syntactic steganography, 1-9
T
Tagged Image File Format (TIFF) files,
1-9, 5-10–5-11, 5-12
TCP, 2-4
Technical steganography, 1-3, 1-4
Terrorism, steganography for, 1-3
TestDisk, 4-61–4-62, 4-63
Text files, 1-8–1-9, 1-18 Text semagrams, 1-4
ThumbsPlus, 5-18, 5-19
TIFF files, 1-9, 5-10–5-11, 5-12
Transformation, 1-10
Transform-domain techniques, 1-6
Transmission Control Protocol (TCP), 2-4
2Mosaic, 1-19–1-20
U
UDP (User Datagram Protocol), 2-4
Undelete (tool), 4-29–4-30
Undeleting a file, 4-7
UNIX-based systems, tools for, 4-33–4-43
User Datagram Protocol (UDP), 2-4
V
Vector images, 5-3
Vector quantization, 5-14–5-15
Video files, 1-11, 1-18
Viewers, in Encase, 3-18
View menu, in Encase, 3-4, 3-6
VirtualLab, 4-30, 4-31
I-4Index
Visible watermarks, 1-14
Visual semagrams, 1-4
W
Watermarking, 1-14–1-16 wbStego, 1-25, 1-26
Windows
creating new Desktop.ini file, 4-7 data acquisition tools, 2-3 file recovery tools for, 4-9–4-33 WinUndelete, 4-31, 4-32Z
WNSTORM, 1-35Zero Assumption Recovery, 4-32–4-33
Word Repair, 4-42Z-File, 1-40
Workplace communication, steganographyZip Repair Pro, 4-43 for, 1-2
ZIP (Zone Information Protocol) files, 5-11
X
Xidie, 1-35, 1-36
XnView, 5-21
This page intentionally left blank
This page intentionally left blank
This page inte__ntionally left blank
This page intentionally left blank
This page intentionally left blank
This page intentionally left blank
This page intentionally left blank
This page intentionally left blank
General Notice
The EC-Council | Press Series’ mission is to educate, introduce and demonstrate Information Security related tools and techniques for internal security analysis purposes only. You will not use the newly acquired skills for illegal or malicious attacks and you will not use such tools in anattempt to compromise any computer system, and you shall indemnify EC-Council and its partners from all liability with respect to the use or misuse of these tools, regardless of intent.
EC-Council provides the hacking skills and tools presented throughout the EC-Council | Press for educational use. The hacking tools are not authored by EC-Council, and in many cases are submitted by the security community. EC-Council will not be held accountable for any damages caused by the proper or improper usage of these materials, and makes no guarantee in regards to their operation or suitability for any specific purpose.
The hacking tools used in the EC-Council | Press programs are meant for research and educational purposes only. The primary intent of these tools is to provide the user with hard to find content for research or self education relevant to network security and various protection methods and their intrinsic flaws by demonstrating exploitation methods and techniques used to circumvent them. We hope that you become more aware of the dangers that lurk in society today and learn how to protect yourself from them with the knowledge you are about to learn. In order to continue you must acceptthat you are going to use this information only for educational and research purposes only.
While possession of information or programs included in this training violates no laws, actually using or implementing some of the programs or content may violate U.S. Federal and other laws. For this reason, the user is instructed not to use any programs or content contained in this training which may violate any laws or infringe on the rights, including intellectual property rights, of others. We provide them for research and educational purposes only.